Valid 70-246 Dumps shared by PassLeader for Helping Passing 70-246 Exam! PassLeader now offer the newest 70-246 VCE dumps and 70-246 PDF dumps, the PassLeader 70-246 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-246 dumps with VCE and PDF here: http://www.passleader.com/70-246.html (224 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-246 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpflh1S25KeW95OF9NaDFwTGJvelBfOW9UWXQ1LVFjR3lRbTU3bTF6RXNxTzQ
QUESTION 161
Your network contains an Active Directory domain named contoso.com that connects to a Windows Azure environment. You deploy System Center 2012 R2 Data Protection Manager (DPM) to the domain. You need to ensure that you can use DPM to back up to the Windows Azure environment. Which three actions should you perform? Each correct answer presents part of the solution.
A. From Windows Azure, create an endpoint.
B. On the DPM server, allow inbound traffic on TCP port 135.
C. Install the Windows Azure Backup agent.
D. Install a certificate on the DPM server and the upload the certificate to Windows Azure.
E. Create a backup vault.
Answer: CDE
Explanation:
C: From Windows Azure Backup, install the agent on each DPM server you want to backup online.
D: Install a certificate on the DPM server and the upload the certificate to Windows Azure.
E: Create a backup vault.
The following two TechNet articles cover this topic fairly well.
http://technet.microsoft.com/en-us/library/dn296608.aspx
http://technet.microsoft.com/en-us/library/jj728748.aspx
QUESTION 162
Drag and Drop Questions
You have a System Center 2012 R2 infrastructure that has Operations Manager installed. Your company is testing a custom application named App1. App1 is deployed to a test server named Server1. Server1 runs Windows Server 2012 R2. You push the Operations Manager agent to Server1 and you start to receive alerts from Server1. You need to give a team of developers historical traces of App1. The developers will store the traces in Team Foundation Server (TFS). Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.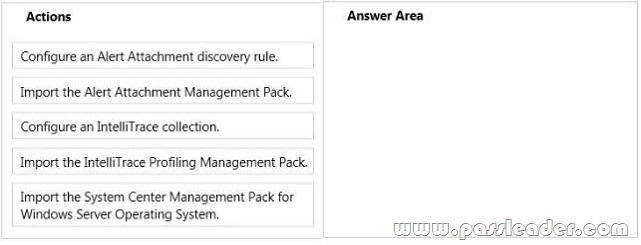
QUESTION 163
Your company has a private cloud that contains a System Center 2012 R2 infrastructure. You have a server named Server1 that runs Windows Server 2012 R2. Server1 hosts a Java-based application. You need to ensure that you can monitor exceptions generated by the application. Which three actions should you perform? Each correct answer presents part of the solution.
A. Deploy the Java Application Performance Monitoring agent to Server1.
B. Import the Management Pack for Java Application Performance Monitoring (APM).
C. Deploy JavaBeans to Server1.
D. Import the Management Pack for Java Enterprise Edition (JEE).
E. Deploy JavaBeans to the Operations Manager server.
Answer: ABD
QUESTION 164
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a member server named Server1. You have a server named Server2 that is a member of a workgroup. All servers run Windows Server 2012 R2. Server1 has System Center 2012 R2 Operations Manager installed. DC1 is configured as an enterprise certification authority (CA). Server1 and DC1 are located on the internal network. Server2 is located on a perimeter network. You need to monitor Server2 by using Operations Manager. Which three actions should you perform? Each correct answer presents part of the solution.
A. Request and install a certificate on Server2, and then import the certificate to Server1.
B. Run the Discovery Wizard on Server1.
C. Open port UDP 161 and UDP 162 on the firewall between the internal network and the perimeter network.
D. Open port TCP 5723 on the firewall between the internal network and the perimeter network.
E. Manually install the Microsoft Monitoring Agent on Server2.
F. Request and install a certificate on Server1, and then import the certificate to Server2.
Answer: ADE
Explanation:
SCOM will authenticate by Kerberos or certificate. In a domain it will be kerberos. On an untrusted Workgroup Server there is no Kerberos so certificates will be used.
– Create certificate for the untrusted Server.
– Import the certificate on the Operation Manager Server.
– Open TCP 5723 both directions in Firewall if there is any (like in DMZ).
http://www.toolzz.com/?p=279
QUESTION 165
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 and a server named Server1. You install the management server role on Server1. You install the Operations Manager agent on DC1. You run the Operations Manager console and discover the active alerts shown in the exhibit. (Click the Exhibit button.)
You need to resolve the active alerts. What should you do?
A. On DC1, install MOMADAdmin.exe.
B. On Server1, install OomADs.msi.
C. On Server1, install MOMADAdmin.exe.
D. On DC1, install OomADs.msi.
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/hh230736.aspx
QUESTION 166
You have a System Center 2012 R2 infrastructure. You plan to implement the Audit Collection Service (ACS). ACS reports will not be available from the Operations Manager console. You need to recommend a solution to view the ACS reports. What should you include in the recommendation?
A. A Microsoft SQL Server Reporting Services (SSRS) instance
B. A reporting services point in Configuration Manager
C. A Reporting data warehouse for Service Manager
D. A Microsoft SharePoint Server report library
Answer: A
QUESTION 167
Your company has a private cloud that is managed by using a System Center 2012 infrastructure. The network contains a Service Manager infrastructure. The company implements a service level agreement (SLA) for the private cloud. You need to recommend an escalation notification solution for when an SLA warning threshold is exceeded. What should you include in the recommendation?
A. a subscription
B. a Desired Configuration Management Event Workflow Configuration
C. an incident event workflow
D. a monitor
E. a rule
Answer: C
Explanation:
You can use the following procedure to create a workflow rule that will change the support tier to Tier 2 whenever the Urgency property of an incident that is related to printing problems is changed to High. This procedure assumes that you already created an incident template to change the support tier to Tier 2, and it assumes that you already created the priority calculation table. For more information, see How to Set Incident Priority and “To create a new printer-related incident template” in How to Create Incident Templates.
http://technet.microsoft.com/en-us/library/ff461123.aspx
QUESTION 168
You have a System Center 2012 Operations Manager infrastructure. You have a line-of-business web application named App1. App1 stores its information in a dedicated Microsoft SQL Server database. Your company defines a service level agreement (SLA) for App1 of at least 98 percent uptime. You need to implement a solution that measures the availability of App1. You create a distributed application for App1. What should you create next?
A. a monitor
B. a Monitor state SLO
C. a Collection rule SLO
D. a rule
Answer: B
Explanation:
http://blogs.technet.com/b/server-cloud/archive/2011/11/11/application-performance-monitoring-withoperations-manager-2012.aspx
QUESTION 169
Your company has a private cloud that contains a System Center 2012 infrastructure. The network contains a Service Manager infrastructure and a Configuration Manager infrastructure. You create a configuration baseline for desired configuration management. You need to ensure that an incident is created automatically in Service Manager when a device is non-compliant. You install the Configuration Manager connector for Service Manager. What should you do next?
A. Create a Desired Configuration Management Event Workflow Configuration.
B. Create a service level objective (SLO) for the desired configuration management incident.
C. Create an incident template.
D. Import the Configuration Manager Management Packs.
Answer: A
Explanation:
A connector is required to bring data from Configuration Manager into Service Manager. From there, you create a Desired Configuration management Event Workflow.
Using Connectors to Import Data into System Center 2012 – Service Manager.
http://technet.microsoft.com/en-us/library/hh524326.aspx
How to Configure Desired Configuration Management to Generate Incidents.
http://technet.microsoft.com/en-us/library/hh495577.aspx
Gol: http://technet.microsoft.com/en-us/library/ff460938
In System Center Service Manager 2010 Service Pack 1 (SP1), you can import configuration baselines from System Center Configuration Manager 2007 by using a Configuration Manager connector. Then, you can configure Service Manager to create incidents for each Service Manager configuration item that is reported as noncompliant against the defined values. You can use the following procedures to configure incident management to automatically generate desired configuration management-based incidents. To configure incident management to automatically generate desired configuration management based incidents:
1. In the Service Manager console, click Administration.
2. In the Administration pane, expand Workflows, and then click Configuration.
3. In the Configuration pane, double-click Desired Configuration Management Event Workflow Configuration.
4. In the Configure Desired Configuration Management Workflows dialog box, click Add.
http://technet.microsoft.com/en-us/library/ff460938.aspx
QUESTION 170
Your company has a private cloud that contains a System Center 2012 Service Manager instance. Service Manager has the Self-Service Portal installed. You create a service offering that contains a single request offering. The service offering provides logged-on users with the ability to add their user account automatically to a group named Group1. You need to ensure that all requests for group membership changes require approval from the security department. What should you modify?
A. the request offering
B. the service request template
C. the service offering
D. the Service Offering Category list
Answer: B
Explanation:
http://syscen.blogspot.com/2012/01/automating-new-user-creation-with-scsm.html
http://syscen.blogspot.com/2012/02/automating-new-user-creation-with-scsm.html
http://syscen.blogspot.com/2012/02/automating-new-user-creation-with-scsm_09.html
http://syscen.blogspot.com/2012/02/automating-new-user-creation-with-scsm_15.html
1. Create Runbook Automated Activity Template.
2. Extend service request class.
3. Create Service Request template using the new Class and include the Runbook Automated Activity Template.
4. Create the Service Request Offering.
QUESTION 171
Your company has a private cloud that is managed by using a System Center 2012 infrastructure. A server named Server1 hosts the System Center 2012 Service Manager management server. A server named Server2 hosts the System Center 2012 Orchestrator management server. You plan to use a runbook named Runbook1 to update the status of Service Manager incidents. You need to ensure that you can create Runbook1, and then reference the runbook in Service Manager. What should you do? (Each correct answer presents part of the solution. Choose all that apply.)
A. From the Service Manager Console, add an incident event workflow.
B. From the Service Manager Shell, run the Update-SCSMWorkflow cmdlet.
C. From the Service Manager Console, create an Orchestrator connector.
D. From the Orchestrator Deployment Manager, register the Integration Pack for System Center Service Manager.
E. From the Service Manager Console, update the Problem Status list.
F. From the System Center 2012 Orchestrator Runbook designer, create a connection.
Answer: CDF
Explanation:
http://social.technet.microsoft.com/Forums/en/administration/thread/ea41a3a4-0b40-47ee-9ecc-a2ecab8794bf
http://technet.microsoft.com/en-us/library/hh519779.aspx
http://go.microsoft.com/fwlink/?LinkID=202690
http://technet.microsoft.com/en-us/library/gg464964.aspx
QUESTION 172
You work as a Network Administrator at ABC.com. The network includes a System Center 2012 infrastructure. System Center 2012 – Service Manager is used by the help desk department to track any problems reported with network devices, servers or computers. You want to be notified every time a new incident that pertains to a server problem is opened. You open the System Center 2012 Service Manager Console. What should you do next?
A. You should configure an announcement.
B. You should configure a subscription.
C. You should configure a template.
D. You should configure a connector.
Answer: C
Explanation:
Although you will need a subscription to receive the messages, you need a template first (to satisfy the requirement — You want to be notified every time a new incident that pertains to a server problem is opened”). When you create a template, you can specify a target class. The target class is used to target certain types of incidents for notifications.
http://technet.microsoft.com/en-us/library/hh519689.aspx
http://blogs.technet.com/b/servicemanager/archive/2009/09/28/creating-notification-templates-in-system-center-service-manager.aspx
QUESTION 173
System Center 2012 allows you to configure how content distribution is managed on remote distribution points that are identified as prestaged. Which setting is desirable for this scenario: You have large packages, with content such as an operating system, and never want to use the network to distribute the content to the distribution point. When you select this option, you must prestage the content on the distribution point.
A. Manually copy the content in this package to the distribution point
B. Download only content changes to the distribution point
C. Automatically download content when packages are assigned to distribution points
D. None of these
Answer: A
QUESTION 174
The storage pool is a set of disks on which the DPM server stores the replicas and recovery points for the protected data. Planning the storage pool involves calculating capacity requirements and planning the configuration of the disks. Which of the following can you NOT use for the storage pool?
A. Direct attached storage (DAS)
B. USB/1394 disks
C. iSCSI storage device or SAN
D. Fiber Channel storage area network (SAN)
Answer: B
QUESTION 175
To view Application Performance Monitoring event details, you must install the Operations Manager web console. Which of the following is NOT a valid requirement for installing web console?
A. ISAPI and CGI Restrictions in IIS are enabled for ASP.NET 4
B. Server must be running SharePoint
C. OS must be 64 bit
D. OS must be Windows Serve 2008 R2 SP1
Answer: B
QUESTION 176
Your company has a datacenter in Los Angeles. The datacenter contains a private cloud that is managed by a System Center 2012 Virtual Machine Manager (VMM) infrastructure. The infrastructure contains two management servers and 10 Hyper-V hosts. You configure VMM to use an update server and to synchronize the updates by using a windows Server Update Services (WSUS) server named WSUS1. You attempt to verify compliance with the Sample Baseline for Security Updates. You view the console as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that you can verify compliance for all of the Hyper-V hosts. What should you modify?
A. the update classifications of the update server
B. the Assignment Scope of the baseline
C. the default configuration provider
D. the Network settings of the All Hosts host group
Answer: B
Explanation:
– In the VMM console, open the Fabric workspace.
– On the Home tab, in the Add group, click Add Resources, and then click Update Server.
– The Add Windows Server Update Services Server dialog box opens.
– In Computer name, enter the fully qualified domain name (FQDN) of the WSUS server (for example, VMMServer01.contoso.com).Specify which TCP/IP port that the WSUS website listens on for connections (for example, port 8530).
– Enter credentials for connecting to the WSUS server.
– The account must have administrator rights on the WSUS server.
– If necessary, select the Use Secure Socket Layer (SSL) to communicate with the WSUS server and client’s check box.
– Click Add.
The WSUS server will be added to VMM, followed by initial synchronization of the updates catalog. Depending on how many update classifications and products you chose when you installed the WSUS server, this operation can take a long time, depending on such factors as network traffic and the load on the WSUS server. To find out the status of the operation, monitor the status of the Add Update Server and Synchronize Update Server jobs in the Jobs window or in the Jobs workspace.
Note:
After you enable update management in VMM, you should manage the WSUS server only through VMM, unless you are using a WSUS server in a Configuration Manager environment. To verify that the WSUS server was added to VMM successfully:
– In the Fabric workspace, on the Fabric pane, expand Servers, and click Update Server. The results pane should display the WSUS server.
– In the Library workspace, on the Library pane, expand Update Catalog and Baselines, and then click Update Catalog. The results pane should display the updates that were downloaded during WSUS synchronization.
QUESTION 177
Your role of Systems Administrator at ABC.com includes the management of the company’s private cloud. The private cloud is hosted on an internal System Center 2012 infrastructure. System Center 2012 – Operations Manager (SCOM) is used to monitor the servers in the private cloud. An SCOM monitor targets all the servers in the private cloud. You want to create an override for the monitor to target only the servers that have a specific application installed. A registry value is used to identify the servers with the application installed. Which two of the following should you create to use with the override? (Choose two.)
A. A Dynamic Group.
B. A Static Group.
C. A Workflow.
D. A Task.
E. An Attribute.
Answer: AE
Explanation:
http://blogs.technet.com/b/kevinholman/archive/2009/06/10/creating-custom-dynamic-computer-groups-based-on-registry-keys-on-agents.aspx
QUESTION 178
Your company has a datacenter in Los Angeles that contains a private cloud. The private cloud is managed by using a System Center 2012 Operations Manager infrastructure. You plan to create a distributed application named App1. You need to ensure that a folder for App1 is available from the Monitoring workspace in the Operations Manager console. What should you do?
A. Run the Protect-SCOMManagementPack cmdlet.
B. Save App1 in the Default Management Pack.
C. Run the Import-SCOMManagementPack cmdlet.
D. Save App1 as a new Management Pack.
Answer: D
Explanation:
The Default Management Pack file contains common elements such as views at the top level of the Monitoring workspace. This is an unsealed management pack file so that you can create views and folders at this level. It should not be used for any other purpose. For creating elements such as monitors and rules, create a new management pack file.
Selecting a Management Pack File.
http://technet.microsoft.com/en-us/library/hh457560.aspx
The Default management pack that ships with OpsMgr 2007 is used to store very specific information for the management group. It is a widely known best practice to NOT write any custom rules, monitors, groups, views, or overrides to this MP. Even customers who know this – and try to enforce this across their organizations… will still inadvertently get junk in their default MP… they will save things here by accident, or by granting access to advanced operators who aren’t educated on this topic. The main problem with doing so… is that we will build a dependency for this MP on any MP it references… and therefore we wont ever be able to delete those management packs, until we clean this Default MP up, and start enforcing best practices.
http://blogs.technet.com/b/kevinholman/archive/2008/11/11/cleaning-up-the-default-mp.aspx
QUESTION 179
Your company has a private cloud that is managed by using a System Center 2012 Operations Manager infrastructure. From Operations Manager, you create a group named Group1. You add multiple servers to Group1. You have an Active Directory group named Group2. You configure a dashboard for the users in Group2 to manage the client computers in Group1. You need to ensure that the users in Group2 can achieve the following tasks:
– View open critical alerts generated by Group1.
– Identify whether a monitor generated an alert.
Which object should you add to the dashboard?
A. a state widget
B. an alert widget
C. an event view
D. a state view
E. an alert view
Answer: B
Explanation:
Adding an alert widget to a dashboard:
Step 1: In an empty dashboard cell, click on the “Click to add widget” link. This opens the New Dashboard and Widget Wizard.
Step 2: Now you are presented with a selection of the available widgets. Select Alert Widgets and then click Next.
Step 3: Once you give your widget a name and a description, you can choose a group or object for which to display alerts. The ability to select between “Groups” and “Groups and objects” allows you to change the scope of objects for which you will receive alerts. If you only want to target a certain object within a group or class, the “Groups and objects” option allows you to do so, while the “Groups” option enables you to view alerts for all objects within the group you choose.
Step 4: Next you can specify the criteria for the alerts you will receive. You may choose the Severity, Priority, and Resolution State of the alerts. For example, I will receive alerts for warnings and information of all priority, and in either the new or closed state.
Step 5: Lastly, select the columns to display for each alert. You can also decide how the alerts are sorted by default as well as how they are grouped. One great addition to the alert widget that is not present in the alert view is the addition of the “Is Monitor Alert” column. This column allows you to see whether the alert was generated by monitor rather than a rule. In my example, I will group alerts by “Is Monitor Alert” and sort by “Last Modified”. And there you have it. We’ve configured a dashboard with a powerful alert widget. It is a great way to quickly view the alerts you care about organized in the way you want. If you aren’t satisfied with your configuration or if your needs change, you can always click the button which gives you the option to reconfigure, personalize, or remove your widget. Reconfiguring a widget opens a wizard with your previously chosen widget configuration and allows you to change all of options to keep up to date with your needs. Here you can change everything from the groups or objects targeted, to the name of the widget. Personalizing a widget allows you to change the display options for that widget. Here you can change which columns are displayed and how your alerts are grouped and sorted. This allows you to view the alerts within a context that is most appropriate to you, but without having to worry about the primary configuration details.
http://blogs.technet.com/b/momteam/archive/2011/10/17/operations-manager-2012-dashboards-the-alertwidget.aspx
QUESTION 180
You deploy System Center 2012 Operations Manager. You create two unsealed management packs named MP1 and MP2. You create an override for MP1. You create a group in MP2. You need to apply the override for MP1 to the group in MP2. What should you do before you apply the override?
A. Create a new class in MP2.
B. Seal MP1.
C. Seal MP2.
D. Create a new class in MP1.
Answer: C
Explanation:
When you create a group, you save it to an unsealed management pack. However, an element in an unsealed management pack, such as a group, cannot reference an element in a different unsealed management pack, such as an override or a view. If you are going to use a group to target an override or scope a view, you must either save the group to the same unsealed management pack as the override or view, or you must seal the management pack that contains the group. If you save the group to the same unsealed management pack as the override or view, you can only use that group for overrides and views that are also contained in that unsealed management pack. If you seal the management pack that contains the group, you can reference that group from other unsealed management packs. However, you cannot easily change any group settings in the sealed management pack or add new groups to the sealed management pack.
http://www.code4ward.net/main/Blog/tabid/70/EntryId/130/Implications-when-using-groups-from-a-sealed-MPfor-overrides.aspx
Get the newest PassLeader 70-246 VCE dumps here: http://www.passleader.com/70-246.html (224 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-246 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpflh1S25KeW95OF9NaDFwTGJvelBfOW9UWXQ1LVFjR3lRbTU3bTF6RXNxTzQ
