Valid 98-366 Dumps shared by PassLeader for Helping Passing 98-366 Exam! PassLeader now offer the newest 98-366 VCE dumps and 98-366 PDF dumps, the PassLeader 98-366 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 98-366 dumps with VCE and PDF here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 98-366 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc
QUESTION 161
What are three advantages of VLANs? (Choose three.)
A. They can logically address packets by using IP.
B. They require a router to connect to VLANs on another switch.
C. They compartmentalize a network and isolate traffic.
D. They are efficient because a single switch can implement only a single VLAN.
E. They act as though they are on the same LAN regardless of physical location.
Answer: BCE
QUESTION 162
Drag and Drop
Match the OSI layer to its corresponding description. To answer, drag the appropriate OSI layer from the column on the left to its description on the right. Each OSI layer may be used once, more than once, or not at all. Each correct match is worth one point.

Answer:

Explanation:
– Application Layer protocols include:
* Remote login to hosts: Telnet.
* File transfer: File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP) Electronic mail transport: Simple Mail Transfer Protocol (SMTP) NTP, Network Time Protocol.
– Session Layer:
Session layer services are commonly used in application environments that make use of remote procedure calls (RPCs). NetBios is also a session layer protocol.
– Network Layer:
The network layer is responsible for packet forwarding including routing through intermediate routers. Network Layer protocols include:
* IPX (Internetwork Packet Exchange).
* X.25 is one of the oldest packet-switched services available. It was developed before the OSI Reference Model. The protocol suite is designed as three conceptual layers, which correspond closely to the lower three layers of the seven-layer OSI model. It also supports functionality not found in the OSI network layer.
* NetWare Link Services Protocol (NLSP) is a routing protocol for Internetwork Packet Exchange (IPX).
– Data Link Layer:
WAPs (Wireless access points) and wwitches operate on the data link layer.
– Network Layer:
Network layer protocols include ICMP (Internet Control Message Protocol), RIP (Routing Information Protocol), and ARP (Address Resolution Protocol).
– Data Link Layer:
The data link layer is responsible for media access control, flow control and error checking. Bridges and network cards are on the data link layer.
QUESTION 163
Hotspot
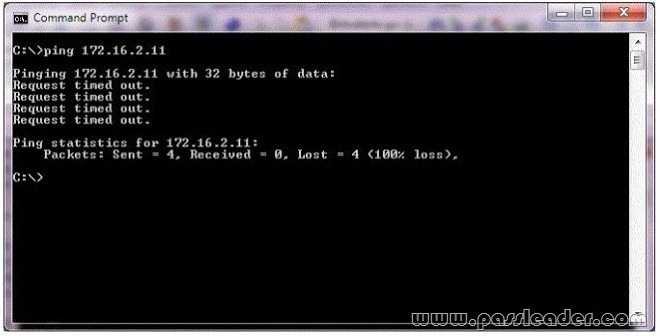
You receive a call from a family member who is unable to connect to a game server. You learn that the server’s IP is 172.16.2.11. To help, you ping the server and receive the information shown in the following image:
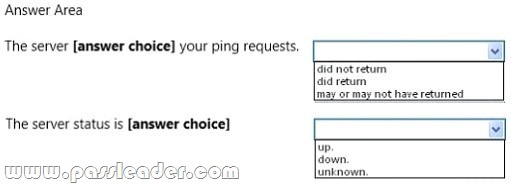
Use the drop-down menus to select the answer choice that completes each statement. Each correct selection is worth one point.
Answer:
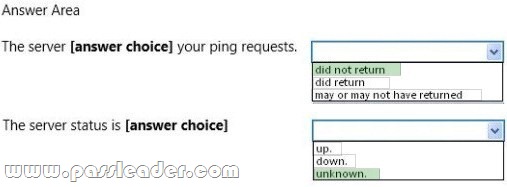
Explanation:
– Received = 0 means that that the ping request did not return any answers.
– Request timed out. This message indicates that no Echo Reply messages were received within the default time of 1 second. This can be due to many different causes; the most common include network congestion, failure of the ARP request, packet filtering, routing error, or a silent discard. So we cannot know if the server is down or not.
QUESTION 164
Drag and Drop
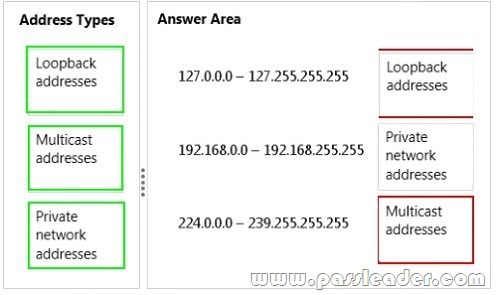
Match each address type to its appropriate range. To answer, drag the appropriate address type from the column on the left to its range on the right. Each address type may be used once, more than once, or not at all. Each correct match is worth one point.

QUESTION 165
For which two reasons should you use IPsec between computers? (Choose two.)
A. Data compression
B. Data integrity
C. Data redundancy
D. Data confidentiality
Answer: BD
Explanation:
IPsec (Internet Protocol Security) is a security protocol that provides encryption and authentication over the Internet. IPSEC supports network-level data integrity, data confidentiality, data origin authentication, and replay protection.
QUESTION 166
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
Every router today is TCP/IP enabled, which is an industry-standard protocol that you use on the Internet and for local addressing.
A. HTTP
B. FTP
C. SNMP
D. No change is needed
Answer: D
QUESTION 167
You are home for vacation, and a family member wants your help to purchase and install network cable for a home office. The cable needs to support at least 300 Mbps. What is the least expensive option that meets this requirement?
A. Cat3
B. Cat5
C. Cat5e
D. Cat6
Answer: C
Explanation:
Cat5e cables support up to 1000BASE-T (Gigabit Ethernet).
Incorrect:
Not Cat5: Max speed is 100Mbps.
Not Cat6: 20% higher cost than Cat 5e.
QUESTION 168
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
WEP wireless encryption is the most susceptible to interception and decryption.
A. WPA-AES
B. WPA2
C. WPA-PSK
D. No change is needed
Answer: D
Explanation:
Several weaknesses have been discovered using WEP encryption that allows an attacker using readily available software to crack the key within minutes.
QUESTION 169
Hotspot
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
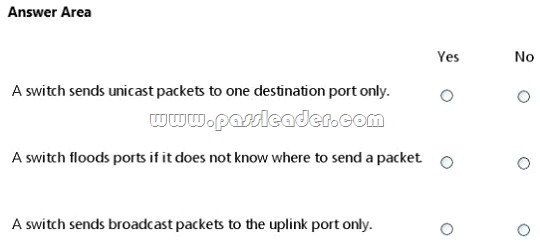
QUESTION 170
The default subnet mask for a Class B network is ____.
A. 0.0.0.255
B. 0.0.255.255
C. 255.0.0.0
D. 255.255.0.0
Answer: D
Explanation:
Class A default subnet mask is 255.0.0.0.
Class B default subnet mask is 255.255.0.0.
Class C default subnet mask is 255.255.255.0.
QUESTION 171
Teredo tunneling is a protocol that ____.
A. translates Internet Protocol version 4 (IPv4) to Internet Protocol version 6 (IPv6)
B. allows IPv6 connectivity through IPv4 devices
C. provides VPN security
D. dynamically allocates IPv6 addresses
Answer: B
Explanation:
Teredo alleviates this problem by encapsulating IPv6 packets within UDP/IPv4 datagrams, which most NATs can forward properly. Thus, IPv6-aware hosts behind NATs can be used as Teredo tunnel endpoints even when they don’t have a dedicated public IPv4 address.
QUESTION 172
What is the default subnet mask for a Class C Internet network?
A. 255.255.255.252
B. 255.255.255.240
C. 255.255.255.192
D. 255.255.255.0
Answer: D
Explanation:
Class A default subnet mask is 255.0.0.0.
Class B default subnet mask is 255.255.0.0.
Class C default subnet mask is 255.255.255.0.
QUESTION 173
The default port used for telnet is ____.
A. 23
B. 25
C. 80
D. 8080
Answer: A
Explanation:
The telnet protocol is used to establish a connection to Transmission Control Protocol (TCP) port number 23, where a Telnet server application (telnetd) is listening.
QUESTION 174
When a client’s DHCP-issued address expires, the client will ____.
A. select a new address and request approval from the DHCP server
B. require manual configuration with a static IP address
C. attempt to obtain a new address by broadcasting
D. continue to use the address until it is notified to stop
Answer: C
Explanation:
If the DHCP client is unable to communicate with the DHCP server from which it obtained its lease, and 87.5 percent of its lease time has expired, it will attempt to contact any available DHCP server by broadcasting DHCP Request messages. Any DHCP server can respond with a DHCPAck message, renewing the lease, or a DHCP Nak message, forcing the DHCP client to initialize and restart the lease process.
Note:
Renewing: IP addressing information is leased to a client, and the client is responsible for renewing the lease. By default, DHCP clients try to renew their lease when 50 percent of the lease time has expired. To renew its lease, a DHCP client sends a DHCPRequest message to the DHCP server from which it originally obtained the lease.
QUESTION 175
You ping a server by using fully qualified domain name (FQDN) and do not receive a response. You then ping the same server by using its IP address and receive a response. Why do you receive a response on the second attempt but not on the first attempt?
A. PING is improperly configured.
B. The DNS is not resolving.
C. The DHCP server is offline.
D. NSLOOKUP is stopped.
Answer: B
Explanation:
DNS is not working.
QUESTION 176
A user reports that she cannot connect to network resources from a computer on the company network. The user was able to connect to the network resources yesterday. You verify that the user’s computer is properly physically connected to the network. You discover that the computer’s IP address is 169.254.48.97. You need to restore access to network resources. What should you do next?
A. Flush the cache on the DNS server.
B. Reset the user’s password on the server.
C. Check your router’s current routing tables.
D. Verify that the DHCP service is available.
Answer: D
Explanation:
169.254.48.97 is an APIPA address. An APIPA address is used when the DHCP server is not available.
QUESTION 177
What command do you use to release the IP configuration handed out by a DHCP server?
A. ipconfig /renew
B. ipconfig /releasedns
C. ipconfig /savestatic
D. ipconfig /release
Answer: D
QUESTION 178
When a signal degrades as it runs through a wire, you have ____.
A. Degradation
B. Attenuation
C. Cross Over
D. Resistance
Answer: A
QUESTION 179
What command do you use to reacquire IP configuration from a DHCP server?
A. ipconfig /renew
B. ipconfig /releasedns
C. ipconfig /savestatic
D. ipconfig /release
Answer: A
QUESTION 180
List the four steps for a client to get an IP address from a DHCP server in the correct order. Which is correct?
A. Discovery > Offering > Request > Acknowledge
B. Request > Offering > Discovery > Acknowledge
C. Discovery > Request > Offering > Acknowledge
D. Request > Offering > Discovery > Acknowledge
Answer: A
Get the newest PassLeader 98-366 VCE dumps here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 98-366 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc