Valid 70-410 Dumps shared by PassLeader for Helping Passing 70-410 Exam! PassLeader now offer the newest 70-410 VCE dumps and 70-410 PDF dumps, the PassLeader 70-410 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-410 dumps with VCE and PDF here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-410 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg
QUESTION 41
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4. Server1 is configured as shown in the following table.

You install Windows Server 2012 R2 on VM2 by using Windows Deployment Services (WDS). You need to ensure that the next time VM2 restarts, you can connect to the WDS server by using PXE. Which virtual machine setting should you configure for VM2?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Answer: G
Explanation:
G. Configure the BIOS of the computer to enable PXE boot, and set the boot order so that it is booting from the network is first.

http://technet.microsoft.com/en-us/library/cc766320(v=ws.10).aspx
QUESTION 42
Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers. The domain controllers are configured as shown in the following table.

In the perimeter network, you install a new server named Server1 that runs a Server Core Installation of Windows Server 2012 R2. You need to join Server1 to the contoso.com domain. What should you use?
A. The New-ADComputer cmdlet
B. The djoin.exe command
C. The dsadd.exe command
D. The Add-Computer cmdlet
Answer: D
Explanation:
A. Creates a new Active Directory computer.
B. Use djoin for offline join in the perimeter network.
C. Adds specific types of objects to the directory.
D. Add the local computer to a domain or workgroup.
http://technet.microsoft.com/en-us/library/ee617245.aspx
http://technet.microsoft.com/en-us/library/ff793312(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc753708(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/hh849798.aspx
QUESTION 43
Your network contains an Active Directory domain named adatum.com. The domain contains three domain DC3 loses network connectivity due to a hardware failure. You plan to remove DC3 from the domain. You log on to DC3. You need to identify which service location (SRV) records are registered by DC3. What should you do?
A. Open the %windir%\system32\config\netlogon.dns file
B. Run dcdiag /test:dns
C. Open the %windir%\system32\dns\backup\adatum.com.dns file
D. Run ipconfig /displaydns
Answer: A
Explanation:
A. Netlogon service creates a log file that contains all the locator resource records and places the logfile in the following location: %windir%\system32\config\netlogon.dns.
B. Analyzes the state of domain controllers in a forest or enterprise and reports any problems to help introubleshooting.
C. dns backup file.
D. used to display current resolver cache content.
You can verify SRV locator resource records by viewing netlogon.dns, located in the %systemroot%\System32\Config folder. The SRV record is a Domain Name System (DNS) resource record that is used to identify computers that hostspecific services. SRV resource records are used to locate domain controllers for Active Directory. You can use Notepad, to view this file. The first record in the file is the domain controller’s Lightweight Directory Access Protocol (LDAP) SRV record. This record should appear similar to the following: _ldap._tcp.Domain_Name.

http://support.microsoft.com/kb/816587/en-us
http://technet.microsoft.com/en-us/library/cc959303.aspx
http://technet.microsoft.com/en-us/library/cc731968(v=ws.10).aspx
QUESTION 44
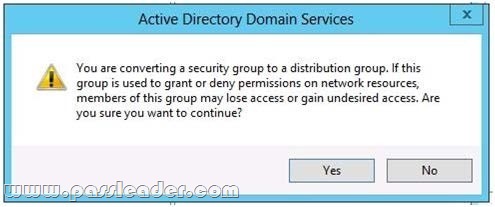
Your network contains an Active Directory forest that contains three domains. A group named Group1 is configured as a domain local distribution group in the forest root domain. You plan to grant Group1 read-only access to a shared folder named Share1. Share1 is located in a child domain. You need to ensure that the members of Group1 can access Share1. What should you do first?
A. Convert Group1 to a global distribution group.
B. Convert Group1 to a universal security group.
C. Convert Group1 to a universal distribution group.
D. Convert Group1 to a domain local security group.
Answer: B
Explanation:
A. Distribution Groups only used for email.
B, Universal can be used for any domain or forest.
C. Distribution Groups only used for email.
D. Permissions can be assigned only within the same domain as the parent domain local group.
Group scope universal can be assigned permissions in any domain or forest.
http://technet.microsoft.com/en-us/library/cc781446(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc755692(v=ws.10).aspx
QUESTION 45
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2008 R2. One of the domain controllers is named DCI. The network contains a member server named Server1 that runs Windows Server 2012 R2. You need to promote Server1 to a domain controller by using install from media (IFM). What should you do first?
A. Create a system state backup of DC1.
B. Create IFM media on DC1.
C. Upgrade DC1 to Windows Server 2012 R2.
D. Run the Active Directory Domain Services Configuration Wizard on Server1.
E. Run the Active Directory Domain Services Installation Wizard on DC1.
Answer: C
Explanation:
A. Backs up system state data to be restored.
C. Only valid option. You could install ADDS role on Server 1 and run ADDS configuration wizard andadd DC to existing domain.
D. Need to add ADDS role first.
E. Wrong server.
Installation from media does not work across different operating system versions. In other words, you must use a Windows Server 2012 R2 domain controller to generate installation media to usefor another Windows Server 2012 R2 domain controller installation. We can use the Install from media (IFM) option to install an Additional Domain Controller in an existing domainis the best option such as a branch office scenario where network is slow, unreliable and costly. IFM will minimize replication traffic during the installation because it uses restored backup files to populate theAD DS database. This will significantly reduce the amount of traffic copied over the WAN link.
Things to remember:
If you are deploying your first Domain Controller in the domain, you cannot use IFM. The OS will need to match the IFM media. (If you create a 2008 R2 IFM, promote a 2008 R2 DC) If you are creating a DC that will be a Global Catalog Server, create your IFM on a Global Catalog Server. If you are creating a DC that will be a DNS Server, create your IFM on a DNS Server. If you want to copy the SYSVOL, the DC on which you generate the installation media and the new DC mustbe at least running Windows Server 2008 with Service Pack 2 or Windows Server 2008 R2. Membership of the Domain Admins group is the minimum required to complete IFM.
http://www.brandonlawson.com/active-directory/deploying-domain-controllers-with-installfrom-media-ifm/
http://technet.microsoft.com/en-us/library/jj574166.aspx
http://technet.microsoft.com/en-us/library/cc770654%28v=ws.10%29.aspx
http://technet.microsoft.com/en-us/library/jj574134.aspx
Media used by the IFM option is created with Windows Server Backup or Ntdsutil.exe from another existingWindows Server 2012 R2 computer only You cannot use a Windows Server 2008 R2 or previous operating system to create media for a Windows Server 2012 R2 domain controller.
QUESTION 46
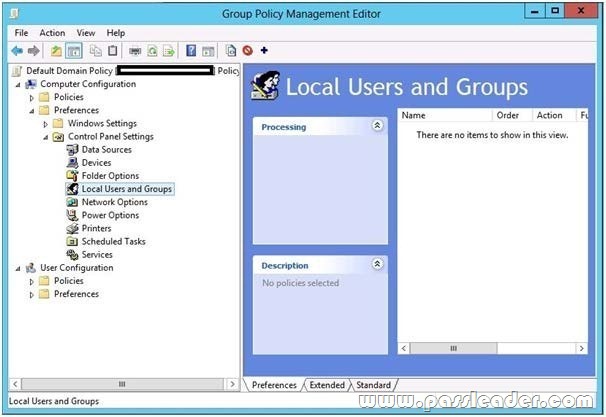
Your network contains an Active Directory domain named contoso.com. The domain contains 100 servers. The servers are contained in a organizational unit (OU) named ServersOU. You need to create a group named Group1 on all of the servers in the domain. You must ensure that Group1 is added only to the servers. What should you configure?
A. a Local Users and Groups preferences setting in a Group Policy linked to the Domain Controllers OU
B. a Restricted Groups setting in a Group Policy linked to the domain
C. a Local Users and Groups preferences setting in a Group Policy linked to ServersOU
D. a Restricted Groups setting in a Group Policy linked to ServersOU
Answer: C
Explanation:
A. This would add the group to the wrong OU.
B. This would affect the whole domain and would effect member of the group.
C. allows you to centrally manage local users and groups on domain member computers and is this isthe correct OU for the GPO change.
D. Restricted Groups defines what member or groups should exist as part of a group.
Why use Group Policy preferences?
Unlike Group Policy settings, which Apply to both local computer policy and Active Directory policy, GroupPolicy preferences only Apply to Active Directory policy. You use preferences to configure many areas of theOS, including:
– System devices, such as USB ports, floppy drives and removable media Network shares and mapping network shares to drive letters System and user environment variables
– User and group accounts for the local computer
– VPN and dial-up networking connections
– Printer configuration and mapping
– Registry settings, schedule tasks and system services
– Settings for Folder Options, Internet Options and Regional and Language Options Settings for power schemes and power management
– Start Menu properties and menu items
http://www.grouppolicy.biz/2010/01/how-to-use-group-policy-preferences-to-secure-localadministrator-groups/
http://technet.microsoft.com/en-us/magazine/hh848751.aspx
http://technet.microsoft.com/en-us/library/cc957640.aspx
http://technet.microsoft.com/en-us/library/cc731972.aspx
QUESTION 47
Your network contains an Active Directory domain named adatum.com. The domain contains several thousand member servers that run Windows Server 2012 R2. All of the computer accounts for the member servers are in an organizational unit (OU) named ServersAccounts. Servers are restarted only occasionally. You need to identify which servers were restarted during the last two days. What should you do?
A. Run dsquery computer and specify the -staiepwd parameter.
B. Run Get-ADComputer and specify the SearchScope parameter.
C. Run Get-ADComputer and specify the IastLogon property.
D. Run dsquery server and specify the -o parameter.
Answer: C
QUESTION 48
Your network contains an Active Directory domain named contoso.com. You log on to a domain controller by using an account named Admin1. Admin1 is a member of the Domain Admins group. You view the properties of a group named Group1 as shown in the exhibit. Group1 is located in an organizational unit (OU) named OU1. You need to ensure that you can modify the Security settings of Group1 by using Active Directory Users and Computers. What should you do from Active Directory Users and Computers?

A. From the View menu, select Users, Contacts, Groups, and Computers as containers.
B. Right-click OU1 and select Delegate Control.
C. From the View menu, select Advanced Features.
D. Right-click contoso.com and select Delegate Control.
Answer: C
Explanation:
From ADUC select view toolbar then select advanced features When you open up the ADUC in a default installation of Active Directory, you are only presented with the basiccontainers. These basic containers include the only organizational unit (OU), which is the Domain Controllers OU, as wellas the other containers such as Users and Computers. To see more in-depth containers, you need to configure the ADUC by going to the View option on thetoolbar, then selecting Advanced Features. This will refresh the view within the ADUC and add some new containers. There are no hidden (or Advanced) OUs that will show up when you configure the ADUC in this way. Viewing ADUC Advanced Settings:

http://searchwindowsserver.techtarget.com/tip/Viewing-advanced-settings-in-ActiveDirectory-Users-and-Computers
QUESTION 49
Your network contains an Active Directory domain named contoso.com. The domain contains two domain controllers named DC1 and DC2. You install Windows Server 2012 on a new computer named DC3. You need to manually configure DC3 as a domain controller. Which tool should you use?
A. Server Manager
B. winrm.exe
C. Active Directory Domains and Trusts
D. dcpromo.exe
Answer: A
Explanation:
A. using the Add Roles Wizard in Server Manager, followed by the Active Directory Domain Services Configuration Wizard.
B. winrm is the server side service for remote management.
C. used for trust between multiple domains.
D. Dcpromo.exe has been deprecated.
In Windows Server 2012 R2, if you run dcpromo.exe (without anyparameters) from a command prompt, you receive a message directing you to Server Manager.
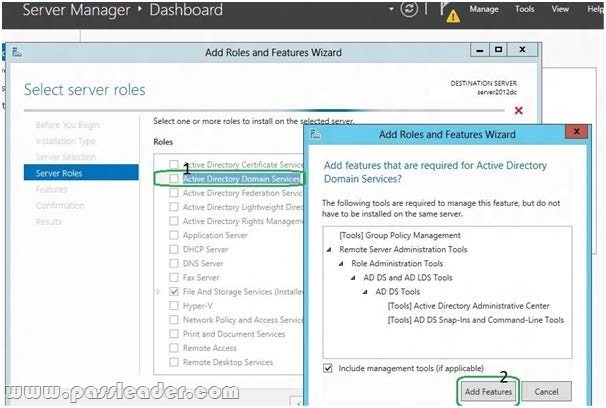
http://technet.microsoft.com/en-us/library/hh472162.aspx#BKMK_GUI
http://technet.microsoft.com/en-us/library/dd163506.aspx
http://technet.microsoft.com/en-us/library/hh831568.aspx
QUESTION 50
You have a server named Core1 that has a Server Core Installation of Windows Server 2012 R2. Core1 has the Hyper-V server role installed Core1 has two network adapters from different third-party hardware vendors. You need to configure network traffic failover to prevent connectivity loss if a network adapter fails. What should you use?
A. New-NetSwitchTeam
B. Add-NetSwitchTeamMember
C. Install-Feature
D. netsh.exe
Answer: A
Explanation:
A. Creates a new switch team.
B. Adds a network adapter member to an existing switch team.
C. Not a valid cmdlet.
D. Network shell (netsh) is a command-line utility that allows you to configure and display the status of various network communications server role.
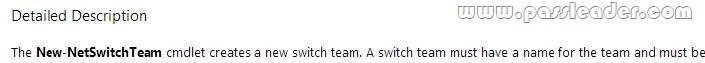
http://technet.microsoft.com/en-us/library/jj553814.aspx
http://technet.microsoft.com/en-us/library/jj553811(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/cc725935(v=ws.10).aspx
QUESTION 51
You have a server named Server1 that runs Windows Server 2012 R2. You connect three new hard disks to Server1. You need to create a storage space that contains the three disks. The solution must meet the following requirements:
– Provide fault tolerance if a single disk fails.
– Maximize the number of files that can be stored in the storage space.
What should you create?
A. A simple space
B. A spanned volume
C. A mirrored space
D. A parity space
Answer: D
Explanation:
A. Stripes data across a set of pool disks, and is not resilient to any disk failures.
B. A spanned volume is a dynamic volume consisting of disk space on more than one physical disk and not fault tolerant.
C. Fault tolerant but Not max space.
D. Fault tolerant and better space ratio.
Parity spaces are designed for capacity efficiency and increased resiliency. Parity spaces are best suited for archival data and streaming media, such as music and videos.
http://social.technet.microsoft.com/wiki/contents/articles/11382.storage-spaces-frequently-asked-questions-faq.aspx
http://social.technet.microsoft.com/wiki/contents/articles/15198.storage-spaces-overview.aspx
http://technet.microsoft.com/en-us/library/cc772180.aspx
QUESTION 52
You perform a Server Core Installation of Windows Server 2012 R2 on a server named Server1. You need to add a graphical user interface (GUI) to Server1. Which tool should you use?
A. The setup.exe command
B. The dism.exe command
C. The imagex.exe command
D. The Add-WindowsPackage cmdlet
Answer: B
Explanation:
The DISM command is called by the Add-WindowsFeature command. Here is the systax for DISM:
Dism /online /enable-feature /featurename:ServerCore-FullServer /featurename:ServerGui-Shell /featurename:Server-Gui-Mgmt

QUESTION 53
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has five network adapters. Three of the network adapters an connected to a network named LAN1. The two other network adapters are connected to a network named LAN2. You need to create a network adapter team from the three network adapters connected to LAN1. Which tool should you use?
A. Routing and Remote Access
B. Network and Sharing Center
C. Server Manager
D. Network Load Balancing Manager
Answer: C
Explanation:
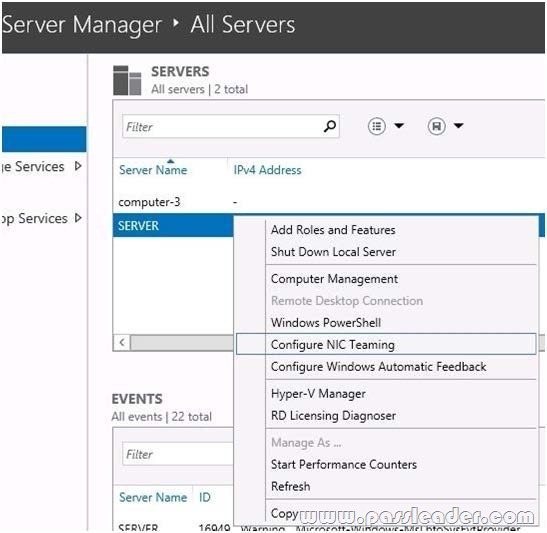

http://technet.microsoft.com/en-us/library/hh831648.aspx
QUESTION 54
You have a server named Server1 that runs Windows Server 2012 R2. You need to remove Windows Explorer, Windows Internet Explorer, and all related components and files from Server1. What should you run on Server1?
A. Uninstall-WindowsFeature Server-Gui-Mgmt-Infra Remove
B. Uninstall-WindowsFeature Server-Gui-Shell Remove
C. msiexec.exe /uninstall iexplore.exe /x
D. msiexec.exe /uninstall explorer.exe /x
Answer: B
Explanation:
A. Would be a server core install.
B. No IE or taskbar, explorer or control panel.
C. Would leave components.
D. Would leave components.
In Windows Server 2012 R2, you can remove the Server Graphical Shell, resulting in the “Minimal ServerInterface”. This is similar to a Server with a GUI installation, but Internet Explorer 10, Windows Explorer, the desktop, andthe Start screen are not installed. Microsoft Management Console (MMC), Server Manager, and a subset of Control Panel are still present. If the server has a full installation of Windows Server, and you need to bring the server down to minimal server interface, you only need to remove the Server-GUI-Shell.
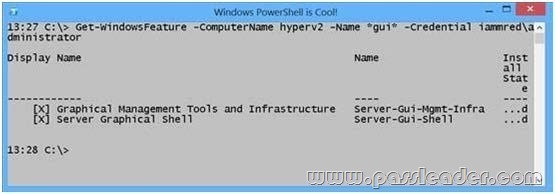
http://technet.microsoft.com/en-us/library/hh831786(v=ws.11).aspx
QUESTION 55
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Hyper-V server role installed. On Server1, you create a virtual machine named VM1. VM1 has a legacy network adapter. You need to assign a specific amount of available network bandwidth to VM1. What should you do first?
A. Remove the legacy network adapter, and then run the Set-VMNetworkAdapter cmdlet
B. Add a second legacy network adapter, and then run the Set-VMNetworkAdopter cmdlet
C. Add a second legacy network adapter, and then configure network adapter teaming
D. Remove the legacy network adapter, and then add a network adapter
Answer: D
Explanation:
A. Set-VMNetworkAdaptercmdlet configures features of the virtual network adapter in a virtual machine or the management operating system.
B. The legacy network adapter doesn’t support bandwidth management.
C. The legacy network adapter doesn’t support bandwidth management.
D. Add a New network adapter.
The legacy network adapter doesn’t support bandwidth management.
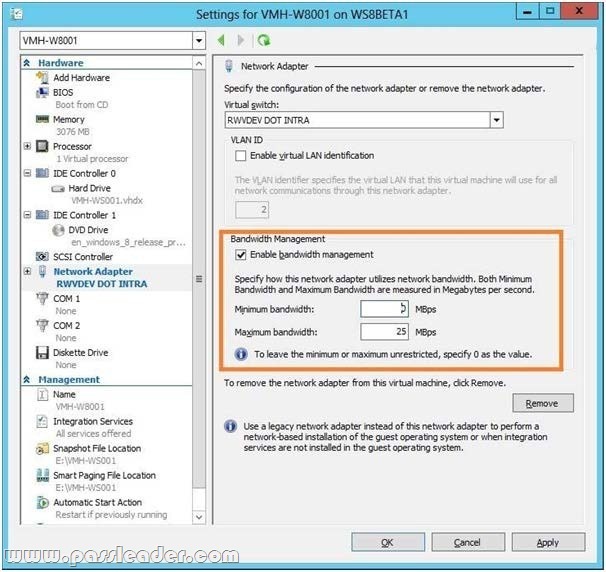
http://technet.microsoft.com/en-us/library/hh848457(v=wps.620).aspx
http://www.techrepublic.com/blog/networking/set-bandwidth-limits-for-hyper-v-vms-withwindows-server-2012/5924
QUESTION 56
Your network contains an Active Directory domain named adatum.com. The domain contains a server named Server1 that runs Windows Server 2012 R2. On a server named Core1, you perform a Server Core Installation of Windows Server 2012 R2. You join Core1 to the adatum.com domain. You need to ensure that you can use Event Viewer on Server1 to view the event logs on Core1. What should you do on Core1?
A. Run the Enable-NetFirewallRule cmdlet.
B. Run sconfig.exeand configure remote management.
C. Run the Disable-NetFirewallRule cmdlet.
D. Run sconfiq.exeand configure the network settings.
Answer: A
Explanation:
A. Allows MMC snap in for Event Viewer.
B. Modifies service entries.
C. Would Disable a firewall rule which was enabled.
D. Modifies service entries.
Enable-NetFirewallRule -DisplayGroup “Remote Event Log Management”
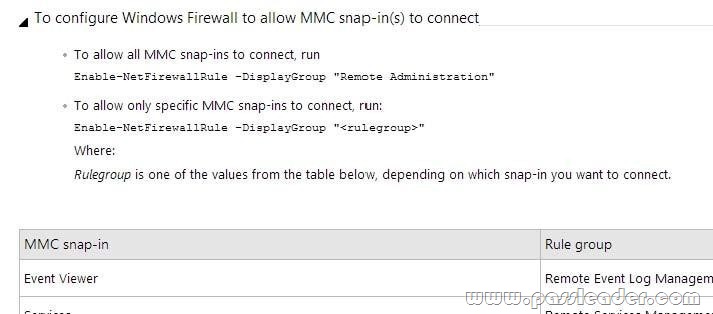
http://technet.microsoft.com/en-us/library/cc990290(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/jj574205.aspx
http://mikefrobbins.com/2013/02/28/use-powershell-to-remotely-enable-firewall-exceptions-on-windows-server-2012/
QUESTION 57
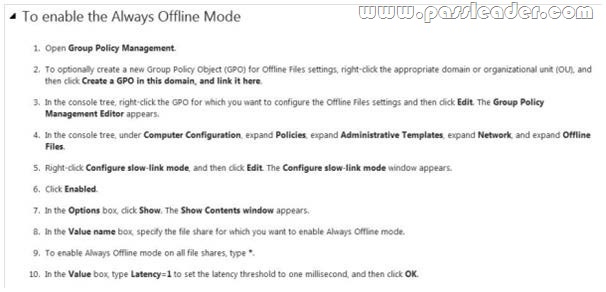
Your network contains a file server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8. You need to ensure that when users are connected to the network, they always use local offline files that are cached from Server1. Which Group Policy setting should you configure?
A. Configure slow-link mode
B. Configure Slow link speed
C. Enable file synchronization on costed networks
D. Turn on economical application of Administratively assigned Offline Files
Answer: A
Explanation:
A. Offline Files to provide faster access to cached files and redirected folders.
B. Defines a slow connection for purposes of Applying and updating Group Policy.
C. automatically tracks roaming and bandwidth usage limits while on metered connections.
D. Lists network files and folders that are always available for offline use. This policy makes the specified filesand folders available offline to users of the computer. When Offline Files is operating in the slow-link mode, all network file requests are satisfied from the OfflineFiles cache. This is similar to a user working offline. If you enable this policy setting, Offline Files uses the slow-link mode if the network throughput between theclient and the server is below (slower than) the Throughput threshold parameter, or if the round-trip networklatency is above (slower than) the Latency threshold parameter.

http://technet.microsoft.com/en-us/library/hh968298.aspx
http://technet.microsoft.com/en-us/library/cc957631.aspx
http://technet.microsoft.com/en-us/library/jj127408.aspx
http://www.group-policy.com/ref/policy/2229/Configure_slow-link_mode
QUESTION 58
Your network contains an Active Directory domain named contoso.com. All servers run either Windows Server 2008 R2 or Windows Serve 2012 R2. All client computers run either Windows 7 or Windows 8. The domain contains a member server named Server1 that runs Windows Server 2012 R2. Server1 has the File and Storage Services server role installed. On Server1, you create a share named Share1. You need to ensure that users can use Previous Versions to restore the files in Share1. What should you configure on Server1?
A. The Shadow Copies settings
B. A Windows Server Backup schedule
C. A data recovery agent
D. The Recycle Bin properties
Answer: A
Explanation:
A. Enable and schedule shadow copies for Share1.
B. The backup doesn’t give users access until files are restored.
D. No settings for file version.
http://technet.microsoft.com/en-us/library/cc786104(v=ws.10).aspx
QUESTION 60
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Print and Document Services server role installed. Server1 is connected to two identical print devices. You need to ensure that users can submit print jobs to the print devices. The solution must ensure that if one print device fails, the print jobs will print automatically on the other print device. What should you do on Server1?
A. Add two printers and configure the priority of each printer.
B. Add one printer and configure printer pooling.
C. Install the Network Load Balancing (NLB) feature, and then add one printer.
D. Install the Failover Clustering feature, and then add one printer.
Answer: B
Explanation:
A. expedite documents that need to be printed immediately.
B. A printing pool is one logical printer connected to multiple printers through multiple ports of theprint server. The printer that is idle receives the next document sent to the logical printer. Whenprinting to a printer pool, the spooler will send waiting jobs to alternate ports. If the original or alternateports are not available.
C. NLB for printing is not supported.
D. Would need 2 nodes.
A printing pool is one logical printer connected to multiple printers through multiple ports of the print server. The printer that is idle receives the next document sent to the logical printer. This is useful in a network with a high volume of printing because it decreases the time users wait for theirdocuments. A printing pool also simplifies administration because multiple printers can be managed from the same logicalprinter on a server. If one device within a pool stops printing, the current document is held at that device. The succeedingdocuments print to other devices in the pool, while the delayed document waits until the nonfunctioningprinter is fixed. Efficient printer pools have the following characteristics: All printers in the pool are the same model. Printer ports can be of the same type or mixed (parallel, serial, and network). It is recommended that all printers be in one location. Because it is impossible to predict which printer willreceive the document, keep all printers in a pool in a single location. Otherwise, users might have a hard timefinding their printed document.
http://technet.microsoft.com/en-us/library/cc757086(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc784619(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc958172.aspx
You can create a printing pool to automatically distribute print jobs to the next available printer. A printing poolis one logical printer connected to multiple printers through multiple ports of the print server. The printer that isidle receives the next document sent to the logical printer.
QUESTION 61
You have a server named Server2 that runs Windows Server 2012 R2. You open Server Manager on Server2 as shown in the exhibit. The Everyone group has read share permission and read NTFS permission to Sources. You need to ensure that when users browse the network, the Sources share is not visible. What should you do?
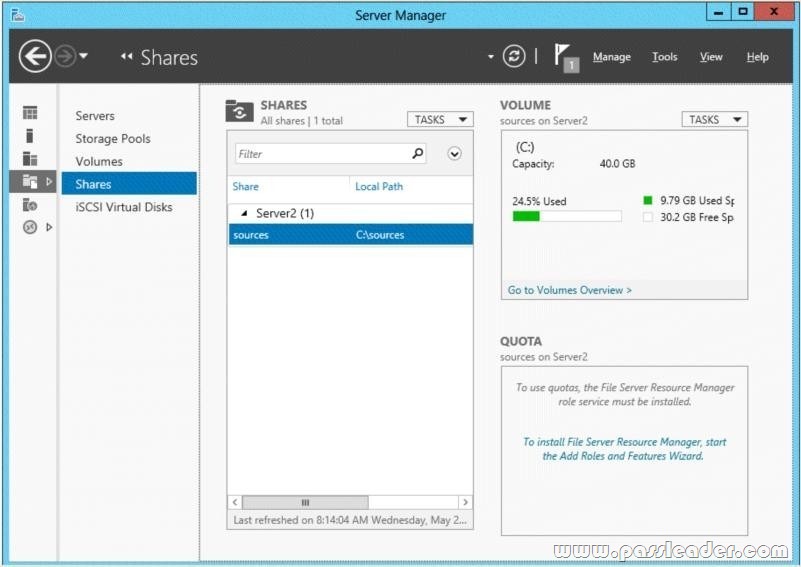
A. From the properties of the Sources folder, remove the Sources share, and then share the Sources folder as Sources$
B. From the properties of the Sources folder, deny the List Folder Contents permission for the Everyone group
C. From the properties of the Sources share, configure access-based enumeration
D. From the properties of the Sources folder, configure the hidden attribute
Answer: A
Explanation:
A. need to remove the old share, $ creates a hidden share.
B. This would deny everyine.
C. This feature allows users of Windows Server 2003-Based file servers to list only the files and folders towhich they have access when browsing content on the file server.
D. This would hide the physical folder not the share.
A hidden share is identified by a dollar sign ($) at the end of the share name. Hidden shares are not listed when you look through the shares on a computer or use the “net view” command Why Use Hidden Shares? Using hidden shares on your network is useful if you do not want a shared folder or drive on the network to beeasily accessible. Hidden shares can add another layer of protection for shared files against unauthorizedpeople connecting to your network. Using hidden shares helps eliminate the chance for people to guess yourpassword (or be logged into an authorized Windows account) and then receive access to the shared resource.
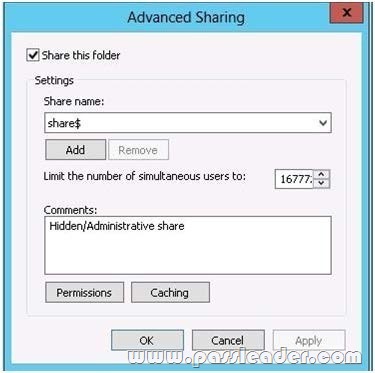
http://support.microsoft.com/kb/314984
http://technet.microsoft.com/en-us/library/cc784710(v=ws.10).aspx
QUESTION 62
Your network contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the Print and Document Services server role installed. You connect a new print device to the network. The marketing department and the sales department will use the print device. You need to provide users from both departments with the ability to print to the network print device. The solution must ensure that if there are multiple documents queued to print, the documents from the sales users print before the documents from the marketing users. What should you do on Server1?
A. Add two printers.
Modify the priorities of each printer and the security settings of each printer.
B. Add two printers and configure printer pooling.
C. Add one printer and configure printer pooling.
D. Add one printer.
Modify the printer priority and the security settings.
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc738090(v=ws.10).aspx
To set different print priority to different groups:
1. Open Printers and Faxes.
Right-click the printer you want to set, click Properties, and then click the Advanced tab. In Priority, click the up or down arrows, and then click OK. Or, type a priority level, where 1 is the lowest level and 99 is the highest, and then click OK. Click Add Printer to add a second logical printer for the same physical printer. For instructions, see Related Topics.
2. Click the Advanced tab.
In Priority, set a priority higher than that of the first logical printer. Instruct the regular group of users to use the first logical printer name and the group with higher priority to use the second logical printer name. Set the appropriate permissions for the different groups.
QUESTION 63
Your network contains an Active Directory domain named contoso.com. The network contains a server named Server1 that runs Window Server 2012 and a server named Server2 that runs Windows Server 2008 R2 Service Pack 1 (SP1). Server1 and Server2 are member server. You need to ensure that you can manage Server2 from Server1 by using Server Manager. Which two tasks should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Install Remote Server Administration Tools on Server1.
B. Install Windows Management Framework 3.0 on Server2.
C. Install the Windows PowerShell 2.0 engine on Server1.
D. Install Microsoft .NET Framework 4 on Server2.
E. Install Remote Server Administration Tools on Server2
Answer: BD
Explanation:
Windows Server 2012 can manage Windows Server 2012 R2, Hyper-V Server 2012 ,Server 2008 SP2 and Server 2008 R2 SP1. These instructions explain how to install:
– Install the full installation of Microsoft .NET Framework 4.0 (dotNetFx40_Full_setup.exe) or, install Microsoft .NET Framework 4.5 (dotNetFx45_Full_setup.exe)
– Install Windows Management Framework 3.0
Security Note By default, Server Manager and Windows PowerShell remote management is enabled in Windows Server 2012 R2.

http://technet.microsoft.com/en-us/library/hh831456.aspx
http://blogs.technet.com/b/keithmayer/archive/2012/10/02/managing-windows-server-2008-sp2-and-r2-from-windows-server-2012-server-manager.aspx#.UaSV9djxkf8
http://technet.microsoft.com/en-us/library/hh847837.aspx#BKMK_InstallingOnWindows7andWindowsServer2008R2
QUESTION 64
Hotspot Question
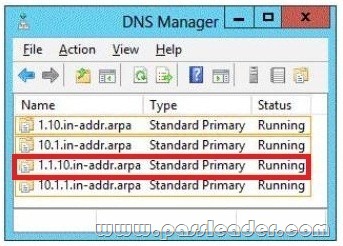
You have a DNS server named Server1. Server1 runs Windows Server 2012 R2. The network ID is 10.1.1.0/24. An administrator creates several reverse lookup zones. You need to identify which reverse lookup zone is configured correctly. Which zone should you identify? To answer, select the appropriate zone in the answer area.
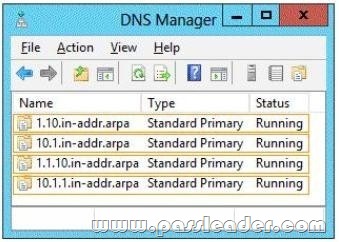
QUESTION 65
Hotspot Question
You have a server named Server1. Server1 runs Windows Server 2012 R2. Server1 has two network adapters. Each network adapter must be configured as shown in the following table.
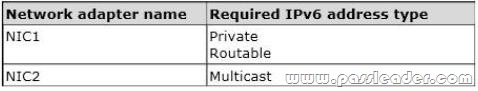
You need to configure the correct IPv6 address prefix for each network adapter. Which prefix should you select for each network adapter? (To answer, drag the appropriate IPv6 prefix to the correct network adapter in the answer area. Each prefix may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

Answer:

Explanation:

http://www.iana.org/assignments/ipv6-address-space/ipv6-address-space.xml
QUESTION 66
Drag and Drop Question
Your company has a main office that contains 225 client computers. The client computers are located on a subnet that uses the network ID of 10.10.1.0/24. The company plans to open two branch offices. The offices will be configured as shown in the following table.

You need to select a network prefix for each office to ensure that there are enough IPv4 addresses for each client computer. The solution must minimize the number of unused IP addresses. Which network prefixes should you select? To answer, drag the appropriate network prefix to the correct branch office in the answer area.

QUESTION 67
Your infrastructure divided in 2 sites. You have a forest root domain and child domain. There is only one DC on site 2 with no FSMO roles. The link goes down to site 2 and no users can log on. What FSMO roles you need on to restore the access?
A. Infrastructure master
B. RID master
C. Domain Naming master
D. PDC emulator
Answer: D
Explanation:
D. The PDC emulator is used as a reference DC to double-check incorrect passwords and it also receives new password changes. PDC Emulator is the most complicated and least understood role, for it runs a diverse range of critical tasks. It is a domain-specific role, so exists in the forest root domain and every child domain. Password changes and account lockouts are immediately processed at the PDC Emulator for a domain, to ensure such changes do not prevent a user logging on as a result of multi-master replication delays, such as across Active Directory sites.
QUESTION 68
You perform a Server Core Installation of window Server 2012 R2 on server named Server1. You need to add a graphical user interface (GUI) to server1. Which tool should you use?
A. the Add-WindowsFeature cmdlet
B. the Install-Module cmdlet
C. the setup.exe command
D. the Add-WindowsPackage cmdlet
Answer: A
Explanation:
A. The Add-WindowsFeature cmdlet allows you to install specified roles, role services, and features
B. Not a valid cmdlet
D. Adds a single .cab or .msu file to a Windows image
Add-WindowsFeature – Allows you to install specified roles, role services, and features.
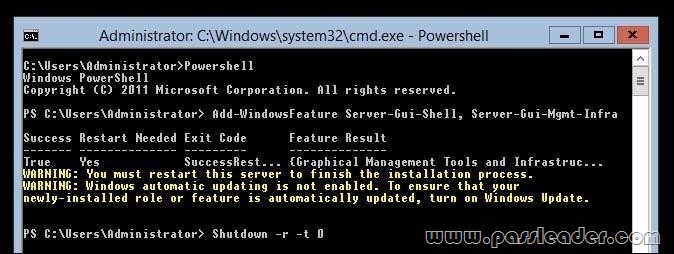
http://technet.microsoft.com/en-us/library/ee662309.aspx
http://technet.microsoft.com/en-us/library/hh852164.aspx
QUESTION 69
A network technician installs Windows Server 2012 R2 Standard on a server named Server1. A corporate policy states that all servers must run Windows Server 2012 R2 Enterprise. You need to ensure that Server1 complies with the corporate policy. You want to achieve this goal by using the minimum amount of administrative effort. What should you perform?
A. a clean installation of Windows Server 2012 R2
B. an upgrade installation of Windows Server 2012 R2
C. online servicing by using Dism
D. offline servicing by using Dism
Answer: C
Explanation:
A. Not least effort
B. Not least effort
C. dism /online /set-edition
D. offline would be less ideal and more workex: DISM /online /Set-Edition:ServerEnterprise/ProductKey:489J6-VHDMP-X63PK-3K798-CPX3Y
Windows Server 2008 R2/2012 contains a command-line utility called DISM (Deployment Image Servicing and Management tool). This tool has many features, but one of those features is the ability to upgrade the edition ofWindows in use. Note that this process is for upgrades only and is irreversible. You cannot set a Windowsimage to a lower edition. The lowest edition will not appear when you run the /Get- TargetEditions option. If the server is running an evaluation version of Windows Server 2012 R2 Standard or Windows Server 2012 R2 Datacenter, you can convert it to a retail version as follows: If the server is a domain controller, you cannot convert it to a retail version. In this case, install an additionaldomain controller on a server that runs a retail version and remove AD DS from the domain controller thatruns on the evaluation version. From an elevated command prompt, determine the current edition name with the command DISM /online /Get-CurrentEdition. Make note of the edition ID, an abbreviated form of the edition name. Then run DISM /online /Set-Edition:<edition ID> /ProductKey:XXXXXXXXXX-XXXXX-XXXXX- XXXXX/AcceptEula,providing the edition ID and a retail product key. The server will restart twice.
http://technet.microsoft.com/en-us/library/jj574204.aspx
http://technet.microsoft.com/en-us/library/dd744380%28v=ws.10%29.aspx
http://blogs.technet.com/b/server_core/archive/2009/10/14/upgrading-windows-server2008-r2-without-media.aspx
http://communities.vmware.com/people/vmroyale/blog/2012/05/30/howto-upgradingwindows-edition-with-dism
QUESTION 70
You have a domain controller named Server1 that runs Windows Server 2012 R2 and has the DNS Server server role installed. Server1 hosts a DNS zone named contoso.com and a GlobalNames zone. You discover that the root hints were removed from Server1. You need to view the default root hints of Server1. What should you do?
A. From Event Viewer, open the DNS Manager log
B. From Notepad, open the Cache.dns file
C. From Windows Powershell, run Get-DNSServerDiagnostics
D. From nslookup, run root server1.contoso.com
Answer: B
Explanation:
A. Allows you to troubleshoot DNS issues
B. DNS Server service implements root hints using a file, Cache.dns, stored in the systemroot\System32\Dnsfolder on the server
C. Gets DNS event logging details
http://technet.microsoft.com/en-us/library/cc758353(v=ws.10).aspx
QUESTION 71
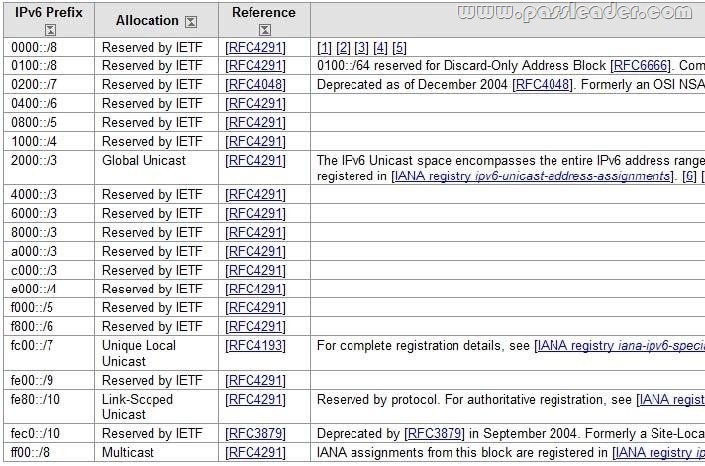
Your company has a main office and two branch offices. The offices connect to each other by using a WAN link. In the main office, you have a server named Server1 that runs Windows Server 2012 R2. Server1 is configured to use an IPv4 address only. You need to assign an IPv6 address to Server1. The IP address must be private and routable. Which IPv6 address should you assign to Server1?
A. fe80:ab32:145c::32cc:401b
B. ff00:3fff:65df:145c:dca8::82a4
C. 2001:ab32:145c::32cc:401b
D. fd00:ab32:14:ad88:ac:58:abc2:4
Answer: D
Explanation:
Installing and Configuring Windows Server 2012 R2
Unique local addresses
Unique local addresses are IPv6 addresses that are private to an organization in the same way that private addresses–such as 10.x.x.x, 192.168.x.x, or 172.16.0.0 172.31.255.255–can be used on an IPv4 network. Unique local addresses, therefore, are not routable on the IPv6 Internet in the same way that an address like 10.20.100.55 is not routable on the IPv4 Internet. A unique local address is always structured as follows: the first 8 bits are always 11111101 in binary format. This means that a unique local address always begins with FD and has a prefix identifier of FD00::/8.
QUESTION 72
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8. You deploy a server named Server1 that runs Windows Server 2012 R2. You install a new client-server application named App1 on Server1 and on the client computers. The client computers must use TCP port 6444 to connect to App1 on Server1. Server1 publishes the information of App1 to an intranet server named Server2 by using TCP port 3080. You need to ensure that all of the client computers can connect to App1. The solution must ensure that the application can connect to Server2. Which Windows Firewall rule should you create on Server1?
A. an inbound rule to allow a connection to TCP port 3080
B. an outbound rule to allow a connection to TCP port 3080
C. an outbound rule to allow a connection to TCP port 6444
D. an inbound rule to allow a connection to TCP port 6444
Answer: D
Explanation:
A. Server2 needs inbound on 3080
B. All ports outbound allowed by default
D. Server1 gets request from Client PC’s it needs a inbound rule for 6444
By default, Windows Firewall with Advanced Security blocks all unsolicited inbound networktraffic, and allows all outbound network traffic. For unsolicited inbound network traffic to reach your computer, you must create an allow rule to permit that type of network traffic. If a network program cannot get access, verify that in the Windows Firewall with Advanced Security snap-in there is an active allow rule for the current profile. To verify that there is an active allow rule, double-click Monitoring and then click Firewall. If there is no active allow rule for the program, go to the Inbound Rules node and create a new rule for that program. Create either a program rule, or a service rule, or search for a group that applies to the feature and make sure all the rules in the group are enabled. To permit the traffic, you must create a rule for the program that needs to listen for that traffic. If you know the TCP or UDP port numbers required by the program, you can additionally restrict the rule to only those ports, reducing the vulnerability of opening up all ports for the program.
http://social.technet.microsoft.com/wiki/contents/articles/13894.troubleshooting-windows-firewall-with-advanced-security-in-windows-server-2012.aspx
QUESTION 73
Your network contains an Active Directory domain named contoso.com. All user accounts in the sales department reside in an organizational unit (OU) named OU1. You have a Group Policy Object (GPO) named GPO1. GPO1 is used to deploy a logon script to all of the users in the sales department. You discover that the logon script does not run when the sales users log on to their computers. You open Group Policy Management as shown in the exhibit. You need to ensure that the logon script in GPO1 is applied to the sales users. What should you do?

A. Enforce GPO1.
B. Modify the link order of GPO1.
C. Modify the Delegation settings of GPO1.
D. Enable the link of GPO1.
Answer: D
Explanation:
D. GPO1 needs to be linked to OU1.

http://technet.microsoft.com/en-us/library/cc732979.aspx
http://technet.microsoft.com/en-us/library/cc776004%28v=ws.10%29.aspx#BKMK_icons_link
QUESTION 74
Your network contains an Active Directory domain named contoso.com. All servers run Windows Server 2012 R2. The domain contains a server named Server1. You install the Windows PowerShell Web Access gateway on Server1. You need to provide administrators with the ability to manage the servers in the domain by using the Windows PowerShell Web Access gateway. Which two cmdlets should you run on Server1? (Each correct answer presents part of the solution. Choose two.)
A. Set-WSManQuickConfig
B. Set-WSManInstance
C. Add-PswaAuthorizationRule
D. Set-BCAuthentication
E. Install-PswaWebApplication
Answer: CE
Explanation:
A. Configures the local computer for remote management
B. Modifies the management information that is related to a resource
C. Adds a new authorization rule to the Windows PowerShell Web Access authorization rule set
D. Specifies the BranchCache computer authentication mode
E. Configures the Windows PowerShell ® Web Access web Application in IIS
http://technet.microsoft.com/en-us/library/hh849867.aspx
http://technet.microsoft.com/en-us/library/hh849875.aspx
http://technet.microsoft.com/en-us/library/jj592890(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/hh848404(v=wps.620).aspx
http://technet.microsoft.com/en-us/library/jj592894(v=wps.620).aspx
QUESTION 75
You have a server named Server 1 that runs Windows Server 2012 R2. Server 1 has the Hyper-V server role installed. You have fixed-size VHD named Files.vhd. You need to make the contents in Files.vhd available to several virtual machines. The solution must meet the following requirements:
– Ensure that if the contents are changed on any virtual machine, the changes are not reflected on the other virtual machines.
– Minimize the amount of disk space used.
What should you do?
A. Create a fixed-size VHDX. Transfer the information from Files.vhd to the new VHDX file.
B. Convert Files.vhd to a dynamically expanding VHD.
C. Create a dynamically expanding VHDX. Transfer the information from Files.vhd to the new VHDX file.
D. Create differencing VHDs that use Files.vhd as the parent disk.
Answer: D
Explanation:
A. A conversion would be needed from VHD to VHDX. Not available to multiple VM’s
B. Single VHD not available to multiple VM’s. Changes wouldn’t be reflected
C. A conversion would be needed from VHD to VHDX. Not available to multiple VM’s
D. Child disk for multiple VM’s with Files.vhd as parent
A differencing disk is associated with another virtual hard disk that you select when you create the differencing disk. This means that the disk to which you want to associate the differencing disk must exist first. This virtual hard disk is called the “parent” disk and the differencing disk is the “child” disk. The parent disk can be any type of virtual hard disk. The differencing disk stores all changes that would otherwise be made to the parent disk if the differencing disk was not being used. The differencing disk provides an ongoing way to save changes without altering the parent disk. You can use the differencing disk to store changes indefinitely, as long as there is enough space on the physical disk where the differencing disk is stored. The differencing disk expands dynamically as data is written to it and can grow as large as the maximum size allocated for the parent disk when the parent disk was created.
http://technet.microsoft.com/en-us/library/cc720381(v=ws.10).aspx
QUESTION 76
Your network contains an Active Directory domain named adatum.com. The domain contains several thousand member servers that run Windows Server 2012 R2. All of the computer accounts for the member servers are in an organizational unit (OU) named ServersAccounts. Servers are restarted only occasionally. You need to identify which servers were restarted during the last two days. What should you do?
A. Run dsquery computer and specify the -stalepwd parameter
B. Run dsquery server and specify the -o parameter
C. Run Get-ADComputer and specify the lastlogon property
D. Run Get-ADComputer and specify the SearchScope parameter
Answer: C
Explanation:
A. dsquery computer -stalepwdnumber_of_days – Searches for all computers that have not changed theirpassword for the specified number_of_days
B. dsquery server -o {dn | rdn | samid} – Specifies the format in which the list of entries found by the search willbe displayed: dn distinguished name of each entry, default; rdn relative distinguished name of each entry; samid SAM account name of each entry computer group server user; upn user principal name of each entryuser
C. Gets one or more Active Directory computers lastLogondate should be used
D. SearchScope specifies the scope of an Active Directory search. Possible values for this parameter are: Base or 0; One Level or 1; Subtree or 2
– A Base query searches only the current path or object.
– A One Level query searches the immediate children of that path or object.
– A Subtree query searches the current path orobject and all children of that path or object.

http://technet.microsoft.com/en-us/library/ee617192.aspx
http://technet.microsoft.com/en-us/library/cc732952(v=ws.10).aspx
QUESTION 77
Your network contains three servers that run Windows Server 2012 R2. The servers are configured as shown in the following table (click Exhibit). Server3 is configured to obtain an IP address automatically. You need to ensure that Server3 only receives an IP address from Server1. The IP address must always be the same. Which two tasks should you perform? (Each correct answer presents part of the solution. Choose two.)

A. Create an exclusion on Server1.
B. Create a filter on Server1.
C. Create a reservation on Server2.
D. Create a reservation on Server1.
E. Create a filter on Server2.
Answer: DE
Explanation:
A. Exclude range of IP’s for lease
B. Wrong Server
C. Wrong Sever
D. For clients that require a constant IP address, you can either manually configure a static IP address,or assign a reservation on the DHCP server
E. DHCP Deny Filter at Server2 to exclude MAC address of Server3 MAC address filter
– Enable and define an explicit allow list. The DHCP server provides DHCP services only to clients whose MAC addresses are in the allow list. Any client that previously received IP addresses is denied address renewal if its MAC address isn’t on the allow list.
– Enable and define an explicit deny list. The DHCP server denies DHCP services only to clients whose MAC addresses are in the deny list. Any client that previously received IP addresses is denied address renewal if its MAC address is on thedeny list.
– Enable and define an allow list and a block list. The block list has precedence over the allow list. This means that the DHCP server provides DHCP services only to clients whose MAC addresses are in the allow list, provided that no corresponding matchesare in the deny list. If a MAC address has been denied, the address is always blocked even if the address is on the allow list.
http://technet.microsoft.com/en-us/library/cc754537(v=ws.10).aspx
http://technet.microsoft.com/en-us/magazine/ff521761.aspx
http://technet.microsoft.com/en-us/library/cc779507(v=ws.10).aspx
QUESTION 78
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that runs Windows Server 2012 R2 and a client computer named Computer1 that runs Windows 8. DC1 is configured as a DHCP server as shown in the exhibit. Computer1 is configured to obtain an IP address automatically. You need to ensure that Computer1 can receive an IP address from DC1. What should you do?

A. Disable the Allow filters
B. Disable the Deny filters
C. Activate Scope [10.1.1.0] Contoso.com
D. Authorize dc1.contoso.com
Answer: D
Explanation:
Red down arrow indicates a unauthorized DHCP server A DHCP server that is a domain controller or a member of an Active Directory domain queries Active Directoryfor the list of authorized servers (identified by IP address). If its own IP address is not in the list of authorized DHCP servers, the DHCP Server service does not completeits startup sequence and automatically shuts down.
http://technet.microsoft.com/en-us/library/cc754792.aspx
http://technet.microsoft.com/en-us/library/ee941131(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/gg722802(v=ws.10).aspx
http://pc-addicts.com/server-2012-dhcp-server-role/
QUESTION 79
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named Server1 that has the DNS Server server role installed. Server1 hosts a primary zone for contoso.com. The domain contains a member server named Server2 that is configured to use Server1 as its primary DNS server. From Server2, you run nslookup.exe as shown in the exhibit. You need to ensure that when you run Nslookup, the correct name of the default server is displayed. What should you do?
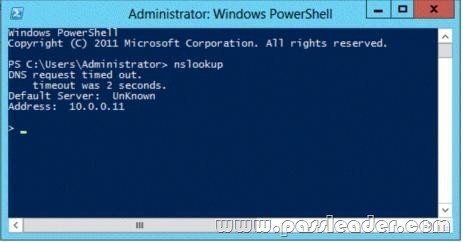
A. From Advanced TCP/IP Settings on Server1, add contoso.com to the DNS suffix list
B. On Server1, modify the Security settings of the contoso.com zone
C. On Server1, create a reverse lookup zone
D. From Advanced TCP/IP Settings on Server2, add contoso.com to the DNS suffix list
Answer: C
Explanation:
C. Make sure that a reverse lookup zone that is authoritative for the PTR resource record exists. For more information about adding a reverse lookup zone, see “Adding a Reverse Lookup Zone”.
http://technet.microsoft.com/en-us/library/cc961417.aspx
QUESTION 80
Your network contains an Active Directory domain named contoso.com. The domain contains a domain controller named DC1 that hosts the primary DNS zone for contoso.com. All client computers are configured to use DC1 as the primary DNS server. You need to configure DC1 to resolve any DNS requests that are not for the contoso.com zone by querying the DNS server of your Internet Service Provider (ISP). What should you configure?
A. Name server (NS) records
B. Condition& forwarders
C. Forwarders
D. Naming Authority Pointer (NAPTR) DNS resource records (RR)
Answer: C
Explanation:
A. Specifies a name server for the domain, which allows DNS lookups within various zones. Each primary and secondary name server should be declared through this record
B. http://windowsitpro.com/networking/q-whats-conditional-dns-forwarding
C. manage the Domain Name System (DNS) traffic between your network and the Internet
D. Configure forwarders to send DNS queries directly to your ISP’s DNS server or other DNS servers. Most of the time, when you configure forwarders, DNS performance and efficiency increases, but thisconfiguration can also introduce a point of failure if the forwarding DNS server is experiencing problems
A forwarder is a Domain Name System (DNS) server on a network used to forward DNS queries for externalDNS names to DNS servers outside of that network. A DNS server on a network is designated as a forwarder by having the other DNS servers in the networkforward the queries they cannot resolve locally to that DNS server. By using a forwarder, you can manage name resolution for names outside of your network, such as names onthe Internet, and improve the efficiency of name resolution for the computers in your network.
http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/2f35cae2-341c4bfe-9dac-724ddace6d51/
http://technet.microsoft.com/en-us/library/cc722542.aspx
http://technet.microsoft.com/en-us/library/cc754931.aspx
Get the newest PassLeader 70-410 VCE dumps here: http://www.passleader.com/70-410.html (512 Q&As Dumps –> 528 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-410 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpfnJzOE1fWnlJOWVtaE93SnJNT3gtaTNYYnVpZkw5THBSMWRKbFlfaXh1azg