Valid 70-697 Dumps shared by PassLeader for Helping Passing 70-697 Exam! PassLeader now offer the newest 70-697 VCE dumps and 70-697 PDF dumps, the PassLeader 70-697 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 70-697 dumps with VCE and PDF here: http://www.passleader.com/70-697.html (201 Q&As Dumps –> 308 Q&As Dumps –> 350 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 70-697 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpd0pjaGx0bzVXVG8
QUESTION 61
Drag and Drop Questions
You support desktop computers for a company named Fabrikam, Inc. The computers are members of the Active Directory domain named fabrikam.com. Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam employees regularly use a Contoso website that is hosted on a server in the contoso.com domain. The website requires SSL and mutual authentication. You need to configure the computers to allow Fabrikam users to access the Contoso website without any warning prompts. You also need to use the fewest certificates possible. Which certificate or certificates should you use? (To answer, drag the appropriate certificate to the correct certificate store. Each certificate may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
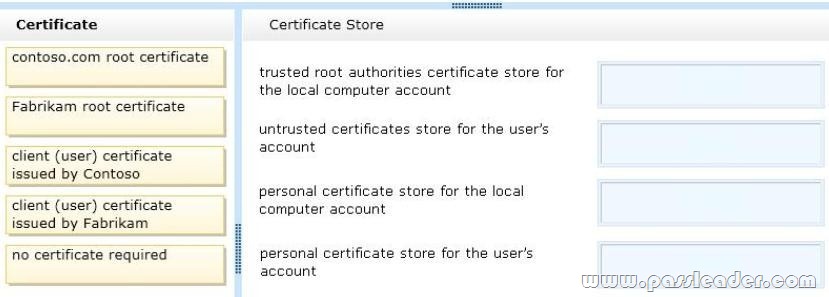
Answer:
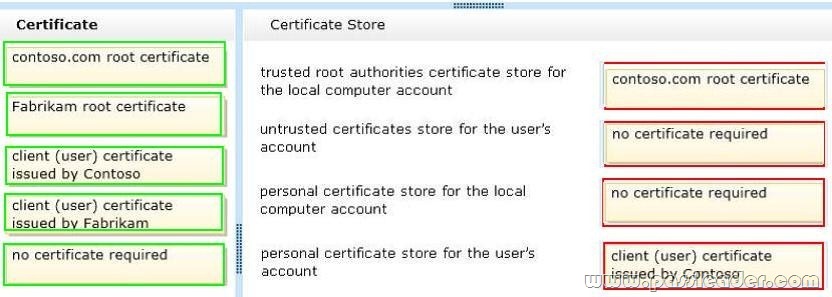
Explanation:
Note:
– contoso.com provided the resources. contoso.com be the trusted root authorities store
– No untrusted certificates
– Not allow access to local computer account (just to user account)
– user account access through client (user) certificate issued by Contoso
QUESTION 62
You administer computers that run Windows 8 Pro and are members of an Active Directory domain. The computers are encrypted with BitLocker and are configured to store BitLocker encryption passwords in Active Directory. A user reports that he has forgotten the BitLocker encryption password for volume E on his computer. You need to provide the user a BitLocker recovery key to unlock the protected volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Ask the user for his computer name.
B. Ask the user to run the manage-bde-unlock E:-pw command.
C. Ask the user for his logon name.
D. Ask the user for a recovery key ID for the protected volume.
Answer: AD
Explanation:
(1) Saying a name does not verify you at all. You can easily find out the name of the owner if you have the access to the PC. For example, open Outlook or simply press Start to verify username. In such cases mobile phone call verification would is preferred, but it is not mentioned in the answers.
(2) It is mentioned in the conditions, that some (NOT ONE) volumes on the computers are encrypted. This means you will have to find out which is locked. So you need recovery key ID.
http://www.concurrency.com/blog/enable-bitlocker-automatically-save-keys-to-active-directory/
QUESTION 63
You have a desktop computer that runs Windows 8 Enterprise. You add three new 3-terabyte disks. You need to create a new 9-terabyte volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Disk Management, create a new spanned volume.
B. From Disk Management, convert all of the 3-terabyte disks to GPT.
C. From PowerShell, run the New-VirtualDisk cmdlet.
D. From Disk Management, bring all disks offline.
E. From Diskpart, run the Convert MBR command.
F. From PowerShell, run the Add-PhysicalDisk cmdlet.
Answer: AB
Explanation:
Create a Spanned Volume. A spanned volume is a dynamic volume consisting of disk space on more than one physical disk. If a simple volume is not a system volume or boot volume, you can extend it across additional disks to create a spanned volume, or you can create a spanned volume in unallocated space on a dynamic disk.
http://technet.microsoft.com/en-us/library/cc772180.aspx
To create a spanned volume using the Windows interface:
1. In Disk Management, right click the unallocated space on one of the dynamic disks where you want to create the spanned volume.
2. Click New Spanned Volume.
3. Follow the instructions on your screen.Using GPT Drives.
http://msdn.microsoft.com/en-us/library/windows/hardware/gg463524.aspx
A GPT disk uses the GUID partition table (GPT) disk partitioning system. A GPT disk offers these benefits:
– Allows up to 128 primary partitions.
– Master Boot Record (MBR) disks can support up to four primary partitions and an additional 124 partitions inside extended partitions.
– Allows a much larger partition size-greater than 2 terabytes (TB), which is the limit for MBR disks.
– Provides greater reliability because of replication and cyclical redundancy check (CRC) protection of the partition table. Can be used as a storage volume on all x64-based platforms, including platforms running Windows XP Professional x64 Edition.
– Starting with Windows Server 2003 SP1, GPT disks can also be used as a storage volume on x86-based Windows platforms.Can be used as a boot volume on x64-based editions of Windows 7, Windows Vista, and Windows Server 2008.
– Starting with Windows Server 2003 SP1, GPT disks can also be used as a boot volume on Itanium-based systems.
Note: Windows only supports booting from a GPT disk on systems that contain Unified Extensible Firmware Interface (UEFI) boot firmware.
QUESTION 64
A company has a main office located in Miami, and brach offices in Boston, Los Angeles and Portland. The Office Networks are configured as described in the following table.

A management computer in the main office, named COMPUTER1, runs windows 8 and several third-party management applications.
– Ensure that only users in the Boston office can connect to COMPUTER1 by using http.
– Ensure that only users in the Los Angeles office can connect COMPUTER1 by using https.
– Ensure that only users in th Portland office can connect to COMPUTER1 by using FTP.
You are configuring access to COMPUTER1. How should you configure windows firewall? (To answer, drag the appropriate elements to the correct location or locations in the answer area. Elements may be used once, more than once, or not at all. You ma need to drag the split bar between panes or scroll.)

Answer:

Explanation:
Seems to be TCP on every answer.
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
QUESTION 65
Drag and Drop Question
You administer Windows 8.1 Enterprise computers. Your company has a team of technical writers that is preparing technical manuals and help files. The team manager wants to ensure that the technical writers are able to restore any documents that been modified within the last year. You need to ensure that the technical writers can restore Microsoft Word files to any previous versions for up to one year. Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
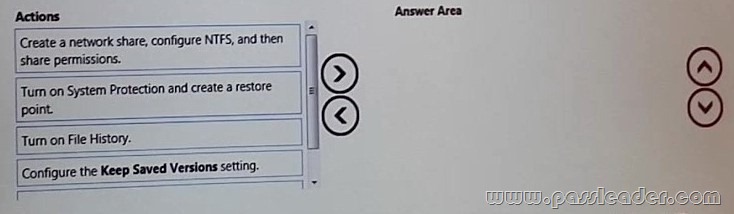
Answer:

Explanation:
We need a NTFS folder. In the Advanced settings we can configure the Keep Saved Versions settings. Finally we turn on File History.
Incorrect Answers:
File History does not use restore points.
https://www.winhelp.us/file-history-in-windows-8.html
QUESTION 66
Drag and Drop Question
You manage update compliance for Windows 8.1 desktop computers that are part of a domain. You need to configure new desktops to automatically receive updates from an intranet resource that you manage. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
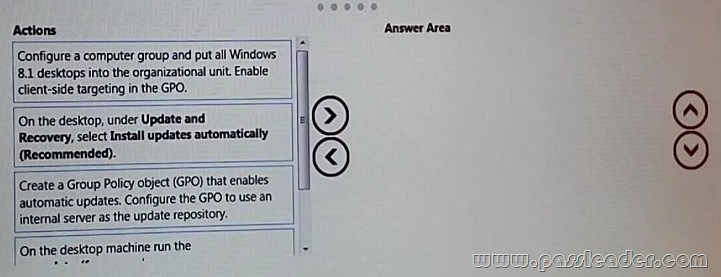
Answer:
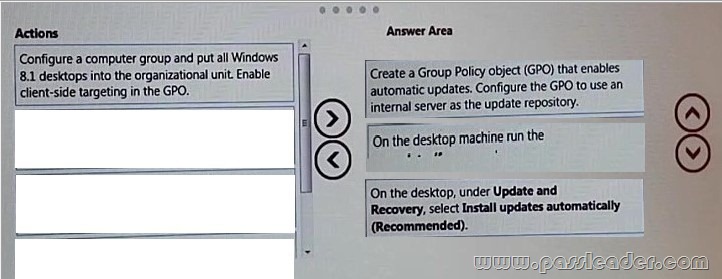
Explanation:
Box 1: Create a GPO that enables automatic updates through the intranet source.
Box 2: gpupdate /force
The Gpupdate command refreshes local and Active Directory-based Group Policy settings, including security settings. The /force Ignores all processing optimizations and reapplies all settings.
Box 3: Configure the clients to install updates automatically.
Incorrect Answers:
* Client side targeting
With client-side targeting, you enable client-computers to add themselves to the computer groups you create in the WSUS console.
https://technet.microsoft.com/en-us/library/bb490983.aspx
QUESTION 67
Drag and Drop Question
You have a Windows 8 computer. You need to migrate from Windows 8 to Windows 8.1 while retaining as much data as possible. You load the Windows 8 media into the DVD drive. Which three actions should you perform next in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)

Answer:
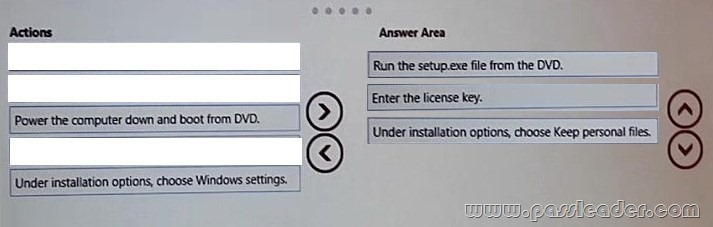
Explanation:
Box 1: Run the Setup.exe file from the DVD. Launch setup.exe on the DVD drive to start the upgrade process.
Box 2: Enter the license key. You will be prompted for the license key.
Box 3: Under the installation, choose Keep personal files.

References:
http://www.laptopmag.com/articles/how-to-upgrade-windows-10
QUESTION 68
Drag and Drop Question
You work for a small company that uses Windows 8.1 computers. The computers are joined to a homegroup. You want to share an existing folder named Research. It is located in the Documents folder. You need to give users the ability to change the files in this folder. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)

Answer:

Explanation:
Box 1: Right-click on the Research folder. Select the folder.
Box 2: Share it with the home group. Finally we need to change the level of access, which by default is view.
Box 3: Under Share With, choose HomeGroup (View and edit).
Incorrect Answers:
* Not read/write
There is no option read/write for Homegroup. The two options are view and view and edit.
Note:
To share individual files or folders:
– Open File Explorer by typing file explorer in the search box in the taskbar, and then selecting File Explorer.
– Select the item, and then select the Share tab.
– Choose an option in the Share with group. There are different Share with options depending on whether your PC is connected to a network and what kind of network it is. To share items with a particular person, choose that person’s account. To share with all the members of your homegroup, choose one of the Homegroup options.(Select libraries to share with all the members of your homegroup by opening HomeGroup.)To prevent a file or folder from being shared with anyone, select the Share tab, and then select Stop sharing. To change the level of access to a file or folder, select the Share tab, and then select either Homegroup (view) or Homegroup (view and edit).If you need to share a location such as a drive or system folder, select the Advanced sharing option.
https://support.microsoft.com/en-us/help/17145/windows-homegroup-from-start-to-finish
QUESTION 69
Hotspot Question
You provide support for a small company. The company purchases a Windows 8.1 laptop for an employee who travels often. The company wants to use BitLocker to secure the hard drive for the laptop in case it is lost or stolen. While attempting to enable BitLocker, you receive the error message shown in the following image.

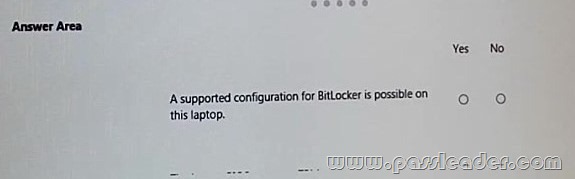
Answer:

Explanation:
How to Configure Computer to Enable BitLocker without Compatible TPM:
– Administrators must follow the steps below to configure their Windows 8 computers to allow enabling Bit Locker Drive Encryption without compatible TPM.
– Log on to Windows 8 computer with the account that has administrative privileges.
– Assuming that the computer has been configured to display classic start menu, click Start and at the bottom of the menu in search box type GPEDIT.MSC command and press enter key.
– On the opened Local Group Policy Editor snap-in from the left pane expand Computer Configuration > Administrative Templates > Windows Components > Bit Locker Drive Encryption and from the expanded list click to select Operating System Devices.
– From the right pane double-click “Require additional authentication” at startup.
– On the opened box click to select Enabled radio button and ensure that under Options section Allow Bit Locker without a compatible TPM checkbox is checked.
– Once done, click Ok button to allow the changes to take effect and close Local Group Policy Editor snap-in.
https://answers.microsoft.com/en-us/windows/forum/windows_8-security/allow-bitlocker-without-compatible-tmp-module/4c0623b5-70f4-4953-bde4-34ef18045e4f?auth=1
QUESTION 70
You have 100 client Windows 8.1 computers. Users are NOT configured as local administrators. You need to prevent the users from running applications that they downloaded from the Internet, unless the applications are signed by a trusted publisher. What should you configure in the Security settings from the Action Center?
A. Virus protection
B. User Account Control
C. Windows SmartScreen settings
D. Network Access Protection
Answer: C
Explanation:
http://windows.microsoft.com/en-ZA/internet-explorer/products/ie-9/features/smartscreen-filter
http://windows.microsoft.com/en-US/windows7/SmartScreen-Filter-frequently-asked-questions-IE9
http://technet.microsoft.com/en-us/network/bb545879.aspx
http://technet.microsoft.com/en-us/library/cc709691%28v=WS.10%29.aspx
QUESTION 71
At home, you use a Windows 8.1 desktop computer. At work, you use a Windows 8.1 laptop that is connected to a corporate network. You use the same Microsoft account to log on to both computers. You have a folder with some personal documents on your desktop computer. The folder must be available and synced between both computers. You need to ensure that the latest version of these files is available. What should you do?
A. Create a folder by using SkyDrive for Windows.
Move all of the personal documents to the new folder.
B. Move the folder to the Libraries folder.
Go to PC Settings.
Under Sync your settings, enable App settings.
C. Right-click the folder and click Properties.
Under Security, provide Full Control for the Microsoft account.
D. Right-click the folder and select Share With, and then select Homegroup (view and edit).
Answer: A
Explanation:
http://answers.microsoft.com/en-us/windows/forum/windows8_1-files/some-solutions-for-skydrive-syncing-problems-in/f69180ad-e9b5-47cd-a3f3-24a4d67e0093
http://answers.microsoft.com/en-us/windows/forum/windows8_1-files/skydrive-in-windows-81-is-not-syncing/1627111e-2ccb-4e6d-ae5f-ee325829191f
QUESTION 72
Drag and Drop Questions
You administer 50 laptops that run Windows 7 Professional 32-bit. You want to install Windows 8 Pro 64-bit on every laptop. Users will keep their own laptops. You need to ensure that user application settings, Windows settings, and user files are maintained after Windows 8 Pro is installed. Which four actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)

Answer:

Explanation:
User State Migration Toolkit (USMT) Reference.
http://technet.microsoft.com/en-us/library/hh825171.aspx
How to Use Hard Links for User State Migration
http://technet.microsoft.com/en-us/library/ee344267.aspx
32-bit and 64-bit Windows: frequently asked questions
http://windows.microsoft.com/en-us/windows7/32-bit-and-64-bit-windows-frequently-asked-questions
If you want to move from a 32-bit version of Windows to a 64-bit version of Windows 7 or vice versa, you’ll need to back up your files and choose the Custom option during Windows 7 installation. Then, you’ll need to restore your files and reinstall your programs.
QUESTION 73
You are a systems administrator for your company. The company has employees who work remotely by using a virtual private network (VPN) connection from their computers, which run Windows 8 Pro. These employees use an application to access the company intranet database servers. The company recently decided to distribute the latest version of the application through using a public cloud. Some users report that every time they try to download the application by using Internet Explorer, they receive a warning message that indicates the application could harm their computer. You need to recommend a solution that prevents this warning message from appearing, without compromising the security protection of the computers. What should you do?
A. Publish the application through a public file transfer protocol (FTP) site.
B. Publish the application through an intranet web site.
C. Instruct employees to disable the SmartScreen Filter from within the Internet Explorer settings.
D. Publish the application to Windows Store.
Answer: B
Explanation:
Intranet is the generic term for a collection of private computer networks within an organization. An intranet uses network technologies as a tool to facilitate communication between people or work groups to improve the data sharing capability and overall knowledge base of an organization’s employees. Intranets utilize standard network hardware and software technologies like Ethernet, Wi-Fi, TCP/IP, Web browsers and Web servers. An organization’s intranet typically includes Internet access but is firewalled so that its computers cannot be reached directly from the outside.
http://compnetworking.about.com/cs/intranets/g/bldef_intranet.htm
http://www.dynamicwebs.com.au/tutorials/ftp.htm
http://msdn.microsoft.com/en-us/library/windows/apps/xaml/hh974576.aspx
QUESTION 74
You administer computers that run Windows 8 Enterprise and are members of an Active Directory domain. Some volumes on the computers are encrypted with BitLocker. The BitLocker recovery passwords are stored in Active Directory. A user forgets the BitLocker password to local drive E: and is unable to access the protected volume. You need to provide a BitLocker recovery key to unlock the protected volume. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Ask the user to run the manage-bde-protectors-disable e: command.
B. Ask the user for his or her logon name.
C. Ask the user to run the manage-bde-unlock E:-pw command.
D. Ask the user for his or her computer name.
E. Ask the user for a recovery key ID for the protected drive.
Answer: DE
Explanation:
Asking user their logon name is a very lame way to verify their identity. Answers D & E seem to be the best solution, because:
– You need to know computer name in order to find computer object in AD, where bitlocker passwords are store
– Without recovery key ID you will not know which bitlocker recovery password to use
QUESTION 75
Hotspot Questions
Your company has a main office and two branch offices named Branch1 and Branch2. The main office contains a file server named Server1 that has BranchCache enabled. Branch1 contains a server named Server2 that is configured as a hosted cache server. All client computers run Windows 8 Enterprise. All of the computers are joined to an Active Directory domain. The BranchCache settings of all the computers are configured as shown in the following exhibit. (Click the Exhibit button.)
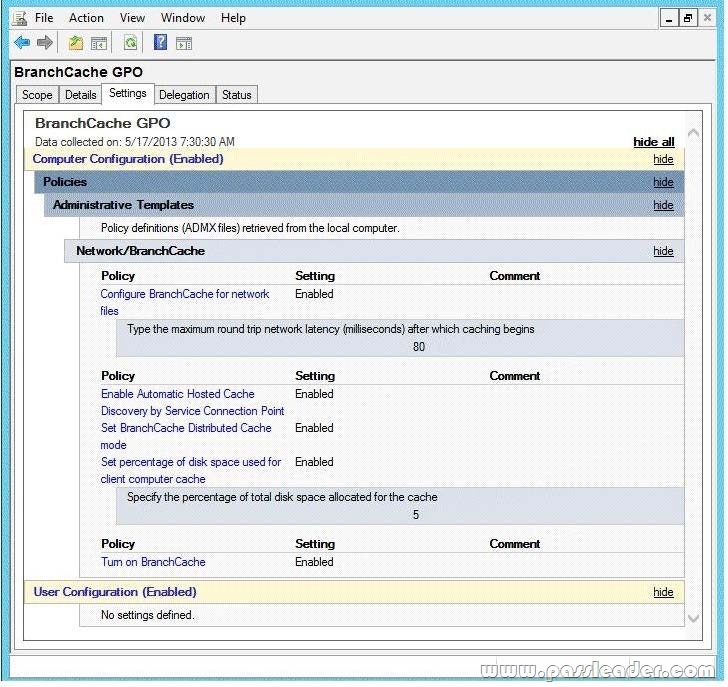
In the table below, identify the effective setting for the client computers in each branch office. Make one selection in each column. Each correct selection is worth one point.

Get the newest PassLeader 70-697 VCE dumps here: http://www.passleader.com/70-697.html (201 Q&As Dumps –> 308 Q&As Dumps –> 350 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 70-697 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpd0pjaGx0bzVXVG8
