Valid AZ-304 Dumps shared by PassLeader for Helping Passing AZ-304 Exam! PassLeader now offer the newest AZ-304 VCE dumps and AZ-304 PDF dumps, the PassLeader AZ-304 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader AZ-304 dumps with VCE and PDF here: https://www.passleader.com/az-304.html (380 Q&As Dumps –> 411 Q&As Dumps –> 432 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader AZ-304 dumps from Cloud Storage: https://drive.google.com/drive/folders/1R6gKXyDGLSdnm0n5rTRLOkJFkIR9zJ0R
NEW QUESTION 355
You deploy an Azure virtual machine that runs an ASP.NET application. The application will be accessed from the internet by the users at your company. You need to recommend a solution to ensure that the users are pre-authenticated by using their Azure Active Directory (Azure AD) account before they can connect to the ASP.NET application. What should you include in the recommendation?
A. an Azure AD enterprise application
B. Azure Traffic Manager
C. a public Azure Load Balancer
D. Azure Application Gateway
Answer: B
NEW QUESTION 356
Your company plans to use a separate Azure subscription for each of its business units. You identify the following governance requirements:
– Each business unit will analyze costs for different workloads such as production, development, and testing.
– The company will analyze costs by business unit and workload.
What should you use to meet the governance requirements?
A. Azure Advisor alerts and Azure Logic Apps.
B. Microsoft Intune and compliance policies.
C. Azure management groups and RBAC.
D. Tags and Azure Policy.
Answer: D
NEW QUESTION 357
You have an Azure SQL Database elastic pool. You need to monitor the resource usage of the elastic pool for anomalous database activity based on historic usage patterns. The solution must minimize administrative effort. What should you include in the solution?
A. a metric alert that uses a dynamic threshold
B. a metric alert that uses a static threshold
C. a log alert that uses a dynamic threshold
D. a log alert that uses a static threshold
Answer: A
NEW QUESTION 358
You are designing an Azure web app that will use Azure Active Directory (Azure AD) for authentication. You need to recommend a solution to provide users from multiple Azure AD tenants with access to App1. The solution must ensure that the users use Azure Multi-Factor Authentication (MFA) when they connect to App1. Which two types of objects should you include in the recommendation? (Each correct answer presents part of the solution. Choose two.)
A. Azure AD managed identities
B. an identity Experience Framework policy
C. Azure AD conditional access policies
D. a Microsoft intune app protection policy
E. an Azure application security group
F. Azure AD guest accounts
Answer: DE
NEW QUESTION 359
You need to create an Azure Storage account that uses a custom encryption key. What do you need to implement the encryption?
A. An Azure key vault in the tame Azure region as the storage account.
B. A managed identity that is configured to access the storage account.
C. A certificate issued by an integrated certification authority (CA) and stored in Azure Key Vault.
D. Azure Active Directory Premium subscription.
Answer: C
NEW QUESTION 360
You have an Azure web app that uses an Azure key vault named KeyVault1 in the West US Azure region. You are designing a disaster recovery plan for KeyVault1. You plan to back up the keys in KeyVault1. You need to identify to where you can restore the backup. What should you identify?
A. KeyVault1 only
B. the same region only
C. the same geography only
D. any region worldwide
Answer: B
NEW QUESTION 361
You nave 200 resource groups across 20 Azure subscriptions. Your company’s security policy states that the security administrator most verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved try the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification. What should you use to implement the security policy?
A. Access reviews in identity Governance.
B. Role assignments in Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
C. Identity Secure Score in Azure Security Center.
D. The user risk policy Azure Active Directory (Azure AD) Identity Protection.
Answer: B
NEW QUESTION 362
You have an on-premises Hyper-V cluster that hosts 20 virtual machines. Some virtual machines run Windows Server 2016 and some run Linux. You plan to migrate the virtual machines to an Azure subscription. You need to recommend a solution to replicate the disks of the virtual machines to Azure. The solution must ensure that the virtual machines remain available during the migration of the disks.
Solution: You recommend implementing an Azure Storage account and then running AzCopy.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
AzCopy only copy files, not the disks. Instead use Azure Site Recovery.
https://docs.microsoft.com/en-us/azure/site-recovery/site-recovery-overview
NEW QUESTION 363
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity. Several VMs are exhibiting network connectivity issues. You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Use the Azure Advisor to analyze the network traffic.
Does the solution meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 364
You need to design a highly available Azure SQL database that meets the following requirements:
– Failover between replicas of the database must occur without any data loss.
– The database must remain available in the event of a zone outage.
– Costs must be minimized.
Which deployment option should you use?
A. Azure SQL Database Hyperscale
B. Azure SQL Database Premium
C. Azure SQL Database Serverless
D. Azure SQL Database Managed Instance General Purpose
Answer: D
NEW QUESTION 365
Your company provides customer support for multiple Azure subscriptions and third-party hosting providers. You are designing a centralized monitoring solution. The solution must provide the following services:
– Collect log and diagnostic data from all the third-party hosting providers into a centralized repository.
– Collect log and diagnostic data from all the subscriptions into a centralized repository.
– Automatically analyze log data and detect threats.
– Provide automatic responses to known events.
Which Azure service should you include in the solution?
A. Azure Sentinel
B. Azure Log Analytics
C. Azure Monitor
D. Azure Application Insights
Answer: D
NEW QUESTION 366
Your company purchases an app named App1. You need to recommend a solution 10 ensure that App 1 can read and modify access reviews. What should you recommend?
A. From the Azure Active Directory admin center, register App1, and then delegate permissions to the Microsoft Graph API.
B. From the Azure Active Directory admin center, register App1, from the Access control (1AM) blade, delegate permissions.
C. From API Management services, publish the API of App1, and then delegate permissions to the Microsoft Graph API.
D. From API Management services, publish the API of App1, from the Access control (1AM) blade, delegate permissions.
Answer: B
NEW QUESTION 367
You have an Azure subscription that contains two applications named App1 and App2. App1 is a sales processing application. When a transaction in App1 requires shipping, a message is added to an Azure Storage account queue, and then App2 listens to the queue (or relevant transactions. In the future, additional applications will be added that will process some of the shipping requests based on the specific details of the transactions. You need to recommend a replacement for the storage account queue to ensure that each additional application will be able to read the relevant transactions. What should you recommend?
A. one Azure Service Bus queue
B. one Azure Service Bus topic
C. one Azure Data Factory pipeline
D. multiple storage account queues
Answer: D
NEW QUESTION 368
Hotspot
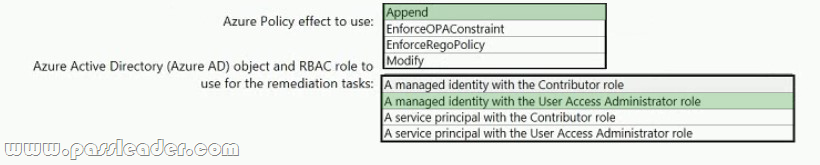
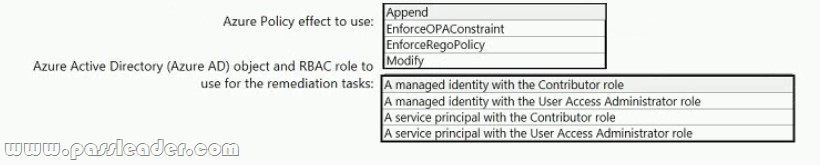
You need to design an Azure policy that will implement the following functionality:
– For new resources, assign tags and values that match the tags and values of the resource group to which the resources are deployed.
– For existing resources, identify whether the tags and values match the tags and values of the resource group that contains the resources.
– For any non-compliant resources, trigger auto-generated remediation tasks to create missing tags and values.
The solution must use the principle of least privilege. What should you include in the design? (To answer, select the appropriate options in the answer area.)
NEW QUESTION 369
Hotspot
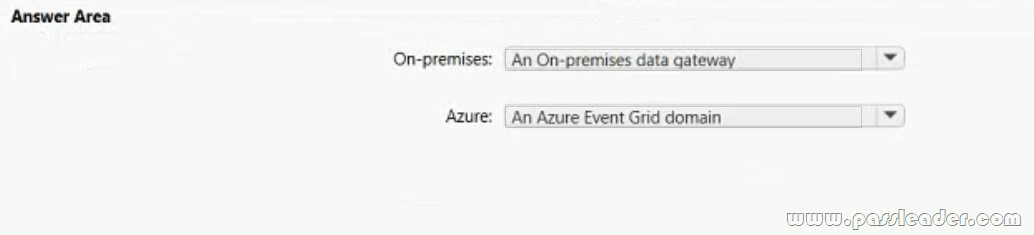
You have an Azure subscription named Subscription1 that is linked to a hybrid Azure Active Directory (Azure AD) tenant. You have an on-premises datacenter that does NOT have a VPN connection to Subscription1. The datacenter contains a computer named Server1 that has Microsoft SQL Server 2016 installed. Server1 is prevented from accessing the internet. An Azure logic app named LogicApp1 requires write access to a database on Server1. You need to recommend a solution to provide LogicApp1 with the ability to access Server1. What should you recommend deploying on-premises and in Azure? (To answer, select the appropriate options in the answer area.)
NEW QUESTION 370
Drag and Drop
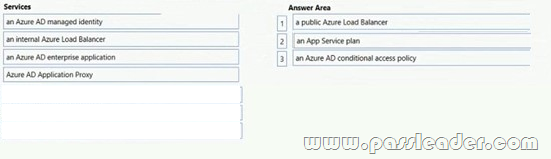
Your on-premises network contains a server named Server1 that runs an ASP.NET application named App1. You have a hybrid deployment of Azure Active Directory (Azure AD). You need to recommend a solution to ensure that users sign in by using their Azure AD account and Azure Multi-Factor Authentication (MFA) when they connect to App1 from the internet. Which three Azure services should you recommend be deployed and configured in sequence? (To answer, move the appropriate services from the list of services to the answer area and arrange them in the correct order.)
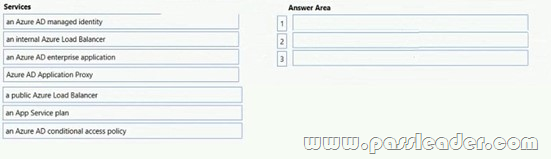
NEW QUESTION 371
Drag and Drop
A company named Contoso, Ltd- has an Azure Active Directory (Azure AD) tenant that uses the Basic license. You plan to deploy two applications to Azure. The applications have the requirements shown in the following table:
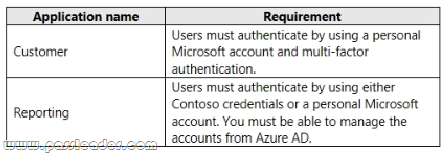
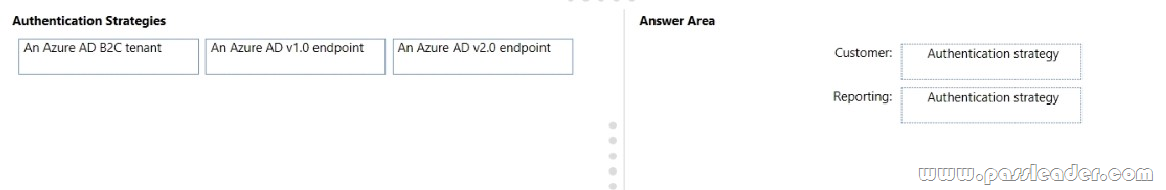
Which authentication strategy should you recommend for each application? (To answer, drag the appropriate authentication strategies to the correct applications. Each authentication strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
NEW QUESTION 372
……
Get the newest PassLeader AZ-304 VCE dumps here: https://www.passleader.com/az-304.html (380 Q&As Dumps –> 411 Q&As Dumps –> 432 Q&As Dumps)
And, DOWNLOAD the newest PassLeader AZ-304 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1R6gKXyDGLSdnm0n5rTRLOkJFkIR9zJ0R