Valid MS-101 Dumps shared by PassLeader for Helping Passing MS-101 Exam! PassLeader now offer the newest MS-101 VCE dumps and MS-101 PDF dumps, the PassLeader MS-101 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader MS-101 dumps with VCE and PDF here: https://www.passleader.com/ms-101.html (291 Q&As Dumps –> 331 Q&As Dumps –> 351 Q&As Dumps –> 383 Q&As Dumps –> 518 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader MS-101 dumps from Cloud Storage: https://drive.google.com/open?id=1sFmn9dFNysQ7vB81xG2ETWkNUxgpyxtK
NEW QUESTION 184
Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD). The domain contains two servers named Server1 and Server2 that run Windows Server 2016. Server1 has the File Server Resource Manager role service installed. You need to configure Server1 to use the Azure Rights Management (Azure RMS) connector. You install the Microsoft Management connector on Server1. What should you do next on Server1?
A. Run the GenConnectorConfig.ps1 script.
B. Configure the URL of the AIPMigrated group.
C. Enable BitLocker Drive Encryption (BitLocker).
D. Install a certification authority (CA).
Answer: A
Explanation:
If you want to use the server configuration tool for the RMS connector, to automate the configuration of registry settings on your on-premises servers, download and run the GenConnectorConfig.ps1 script.
https://docs.microsoft.com/en-us/azure/information-protection/install-configure-rms-connector#installing-the-rms-connector
NEW QUESTION 185
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do first?
A. From Microsoft Cloud App Security, create an access policy.
B. From the Security & Compliance admin center, create an eDiscovery case.
C. From Microsoft Cloud App Security, create an activity policy.
D. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
Answer: D
Explanation:
A DLP policy contains a few basic things:
– Where to protect the content: locations such as Exchange Online, SharePoint Online, and OneDrive for Business sites, as well as Microsoft Teams chat and channel messages.
– When and how to protect the content by enforcing rules comprised of:
1). Conditions the content must match before the rule is enforced. For example, a rule might be configured to look only for content containing Social Security numbers that’s been shared with people outside your organization.
2). Actions that you want the rule to take automatically when content matching the conditions is found. For example, a rule might be configured to block access to a document and send both the user and compliance officer an email notification.
https://docs.microsoft.com/en-us/microsoft-365/compliance/data-loss-prevention-policies
NEW QUESTION 186
You have a Microsoft 365 subscription. From the subscription, you perform an audit log search, and you download all the results. You plan to review the audit log data by using Microsoft Excel. You need to ensure that each audited property appears in a separate Excel column. What should you do first?
A. From Power Query Editor, transform the JSON data.
B. Format the Operations column by using conditional formatting.
C. Format the AuditData column by using conditional formatting.
D. From Power Query Editor, transform the XML data.
Answer: A
Explanation:
After you search the Office 365 audit log and download the search results to a CSV file, the file contains a column named AuditData, which contains additional information about each event. The data in this column is formatted as a JSON object, which contains multiple properties that are configured as property:value pairs separated by commas. You can use the JSON transform feature in the Power Query Editor in Excel to split each property in the JSON object in the AuditData column into multiple columns so that each property has its own column. This lets you sort and filter on one or more of these properties.
https://docs.microsoft.com/en-us/microsoft-365/compliance/export-view-audit-log-records
NEW QUESTION 187
Hotspot
You have a Microsoft 365 subscription. You are planning a threat management solution for your organization. You need to minimize the likelihood that users will be affected by the following threats:
– Opening files in Microsoft SharePoint that contain malicious content
– Impersonation and spoofing attacks in email messages
Which policies should you create in the Security & Compliance admin center? (To answer, select the appropriate options in the answer area.)
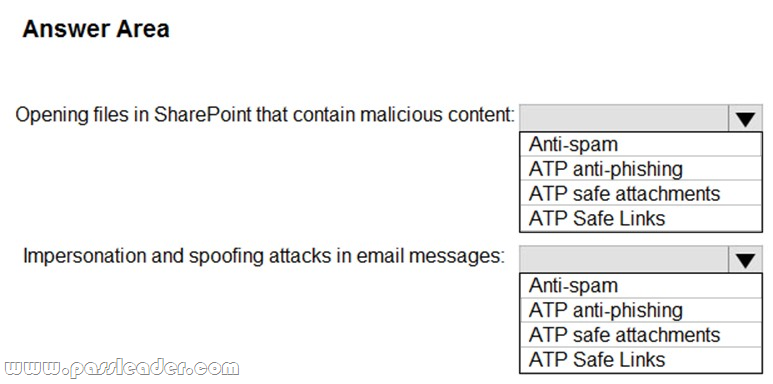
Answer:

Explanation:
Box 1: ATP Safe Attachments. ATP Safe Attachments provides zero-day protection to safeguard your messaging system, by checking email attachments for malicious content. It routes all messages and attachments that do not have a virus/ malware signature to a special environment, and then uses machine learning and analysis techniques to detect malicious intent. If no suspicious activity is found, the message is forwarded to the mailbox.
Box 2: ATP anti-phishing. ATP anti-phishing protection detects attempts to impersonate your users and custom domains. It applies machine learning models and advanced impersonation-detection algorithms to avert phishing attacks.
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/office-365-atp#configure-atp-policies
NEW QUESTION 188
Hotspot
You have a Microsoft 365 subscription. All users are assigned Microsoft Azure Active Directory Premium licenses. From the Device Management admin center, you set Microsoft Intune as the MDM authority. You need to ensure that when the members of a group named Marketing join a device to Azure Active Directory (Azure AD), the device is enrolled automatically in Intune. The Marketing group members must be limited to five devices enrolled in Intune. Which two options should you use to perform the configurations? (To answer, select the appropriate blades in the answer area.)

Answer:

Explanation:
Device enrollment manager (DEM) is an Intune permission that can be applied to an Azure AD user account and lets the user enroll up to 1,000 devices. You can create and manage enrollment restrictions that define what devices can enroll into management with Intune, including the:
– Number of devices.
– Operating systems and versions.
The Marketing group members must be limited to five devices enrolled in Intune.
https://docs.microsoft.com/en-us/intune/enrollment/device-enrollment-manager-enroll
https://docs.microsoft.com/en-us/intune/enrollment/enrollment-restrictions-set
NEW QUESTION 189
Hotspot
You have an Azure Active Directory (Azure AD) tenant that contains two users named User1 and User2. On September 5, 2019, you create and enforce a terms of use (ToU) in the tenant. The ToU has the following settings:
– Name: Terms1
– Display name: Terms1 name
– Require users to expand the terms of use: Off
– Require users to consent on every device: Off
– Expire consents: On
– Expire starting on: October 10, 2019
– Frequency: Monthly
User1 accepts Terms1 on September 5, 2019. User2 accepts Terms1 on October 5, 2019. When will Terms1 expire for the first time for each user? (To answer, select the appropriate options in the answer area.)

Answer:

Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/terms-of-use
NEW QUESTION 190
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign up for Microsoft Store for Business. The tenant contains the users shown in the following table:

Microsoft Store for Business has the following Shopping behavior settings:
– Make everyone a Basic Purchaser is set to Off.
– Allow app requests is set to On.
You need to identify which users can add apps to the Microsoft Store for Business private store. Which users should you identify?
A. User1 and User2
B. User3 only
C. User1 only
D. User3 and User4
Answer: A
NEW QUESTION 191
Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table:

You enroll all the computers in Upgrade Readiness. You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade.
Solution: You set the importance status of App2 to Low install count.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
If an app is installed on less than 2% of the targeted devices, it’s marked Low install count. Two percent is the default value. You can adjust the threshold in the readiness settings from 0% to 10%. Desktop Analytics automatically marks these apps as Ready to upgrade.
https://docs.microsoft.com/en-us/configmgr/desktop-analytics/about-deployment-plans
NEW QUESTION 192
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. Your company purchases a Microsoft 365 subscription. You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Cloud App Security admin center, you assign the App/instance admin role for all Microsoft Online Services to User1.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
App/instance admin: Has full or read-only permissions to all of the data in Microsoft Cloud App Security that deals exclusively with the specific app or instance of an app selected.
https://docs.microsoft.com/en-us/cloud-app-security/manage-admins
NEW QUESTION 193
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant is configured to use Azure AD Identity Protection. You plan to use an application named App1 that creates reports of Azure AD Identity Protection usage. You register App1 in the tenant. You need to ensure that App1 can read the risk event information of contoso.com. To which API should you delegate permissions?
A. Windows Azure Service Management API
B. Windows Azure Active Directory
C. Microsoft Graph
D. Office 365 Management
Answer: C
Explanation:
https://docs.microsoft.com/en-us/graph/api/resources/identityprotection-root?view=graph-rest-beta
NEW QUESTION 194
You have a Microsoft 365 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP). All the devices in your organization are onboarded to Microsoft Defender ATP. You need to ensure that an alert is generated if malicious activity was detected on a device during the last 24 hours. What should you do?
A. From Alerts queue, create a suppression rule and assign an alert.
B. From the Security & Compliance admin center, create an audit log search.
C. From Advanced hunting, create a query and a detection rule.
D. From the Security & Compliance admin center, create a data loss prevention (DLP) policy.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/custom-detection-rules
NEW QUESTION 195
You have a Microsoft 365 subscription. You plan to connect to Microsoft Exchange Online PowerShell and run the following cmdlets:
– Search-MailboxAuditLog
– Test-ClientAccessRule
– Set-GroupMailbox
– Get-Mailbox
Which cmdlet will generate an entry in the Microsoft Office 365 audit log?
A. Search-MailboxAuditLog
B. Test-ClientAccessRule
C. Set-GroupMailbox
D. Get-Mailbox
Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide#exchange-admin-audit-log
NEW QUESTION 196
……
Get the newest PassLeader MS-101 VCE dumps here: https://www.passleader.com/ms-101.html (291 Q&As Dumps –> 331 Q&As Dumps –> 351 Q&As Dumps –> 383 Q&As Dumps –> 518 Q&As Dumps)
And, DOWNLOAD the newest PassLeader MS-101 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=1sFmn9dFNysQ7vB81xG2ETWkNUxgpyxtK