Valid SC-200 Dumps shared by PassLeader for Helping Passing SC-200 Exam! PassLeader now offer the newest SC-200 VCE dumps and SC-200 PDF dumps, the PassLeader SC-200 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-200 dumps with VCE and PDF here: https://www.passleader.com/sc-200.html (311 Q&As Dumps –> 346 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-200 dumps from Cloud Storage: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE
NEW QUESTION 293
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains a user named User1. You need to ensure that User1 can manage Microsoft Defender XDR custom detection rules and Endpoint security policies. The solution must follow the principle of least privilege. Which role should you assign to User1?
A. Security Administrator
B. Security Operator
C. Cloud Device Administrator
D. Desktop Analytics Administrator
Answer: B
Explanation:
https://learn.microsoft.com/en-us/defender-xdr/custom-roles
NEW QUESTION 294
You have a Microsoft Sentinel workspace that contains a custom workbook named Workbook1. You need to create a visual based on the SecurityEvent table. The solution must meet the following requirements:
– Identify the number of security events ingested during the past week.
– Display the count of events by day in a timechart.
What should you add to Workbook1?
A. a query
B. a metric
C. a group
D. links or tabs
Answer: A
Explanation:
A query allows you to retrieve specific data from the SecurityEvent table. You can write a query that filters events based on the past week’s timestamp and aggregates the count of events by day. The timechart visualization will display this aggregated data over time, showing the event count trends.
NEW QUESTION 295
You have an Azure subscription. You need to stream the Microsoft Graph activity logs to a third-party security information and event management (SIEM) tool. The solution must minimize administrative effort. To where should you stream the logs?
A. an Azure Event Hubs namespace
B. an Azure Storage account
C. an Azure Event Grid namespace
D. a Log Analytics workspace
Answer: A
Explanation:
https://techcommunity.microsoft.com/t5/microsoft-entra-blog/microsoft-graph-activity-logs-is-now-generally-available/ba-p/4094535
NEW QUESTION 296
You have 500 on-premises devices. You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. You onboard 100 devices to Microsoft Defender 365. You need to identify any unmanaged on-premises devices. The solution must ensure that only specific onboarded devices perform the discovery. What should you do first?
A. Create a device group.
B. Create an exclusion.
C. Set Discovery mode to Basic.
D. Create a tag.
Answer: C
Explanation:
https://learn.microsoft.com/en-us/defender-endpoint/device-discovery?view=o365-worldwide
NEW QUESTION 297
You have a Microsoft 365 E5 subscription that contains a device named Device1. Device1 is enrolled in Microsoft Defender for Endpoint. Device1 reports an incident that includes a file named File1.exe as evidence. You initiate the Collect Investigation Package action and download the ZIP file. You need to identify the first and last time File1.exe was executed. What should you review in the investigation package?
A. Processes.
B. Autoruns.
C. Security event log.
D. Scheduled tasks.
E. Prefetch files.
Answer: E
Explanation:
To identify the first and last time that File1.exe was executed on Device1, you should review the Prefetch files in the investigation package. Prefetch files in Windows are designed to speed up the application launch process and contain information about how often and when a particular application is run. This data can be used to determine the execution history of File1.exe.
https://learn.microsoft.com/en-us/defender-endpoint/respond-machine-alerts#collect-investigation-package-from-devices
NEW QUESTION 298
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have a virtual machine named Server1 that runs Windows Server 2022 and is hosted in Amazon Web Services (AWS). You need to collect logs and resolve vulnerabilities for Server1 by using Defender for Cloud. What should you install first on Server1?
A. the Microsoft Monitoring agent
B. the Azure Monitor agent
C. the Azure Connected Machine agent
D. the Azure Pipelines agent
Answer: C
NEW QUESTION 299
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 500 Windows devices. You plan to create a Microsoft Defender XDR custom deception rule. You need to ensure that the rule will be applied to only 10 specific devices. What should you do first?
A. Add custom lures to the rule.
B. Add the IP address of each device to the list of decoy accounts and hosts of the rule.
C. Add the devices to a group.
D. Assign a tag to the devices.
Answer: D
NEW QUESTION 300
You have an on-premises network. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Identity. From the Microsoft Defender portal, you investigate an incident on a device named Device1 of a user named User1. The incident contains the following Defender for Identity alert:
“Suspected identity theft (pass-the-ticket) (external ID 2018)”
You need to contain the incident without affecting users and devices. The solution must minimize administrative effort. What should you do?
A. Disable User1 only.
B. Quarantine Device1 only.
C. Reset the password for all the accounts that previously signed in to Device1.
D. Disable User1 and quarantine Device1.
E. Disable User1, quarantine Device1, and reset the password for all the accounts that previously signed in to Device1.
Answer: E
NEW QUESTION 301
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. You are investigating an attacker that is known to use the Microsoft Graph API as an attack vector. The attacker performs the tactics shown the following table:
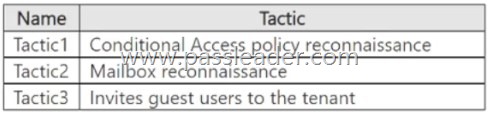
You need to search for malicious activities in your organization. Which tactics can you analyze by using the MicrosoftGraphActivityLogs table?
A. Tactic2 only.
B. Tactic1 and Tactic2 only.
C. Tactic2 and Tactic3 only.
D. Tactic1, Tactic2, and Tactic3.
Answer: D
NEW QUESTION 302
You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. WS1 uses Microsoft Defender for Cloud. You have the Microsoft security analytics rules shown in the following table:
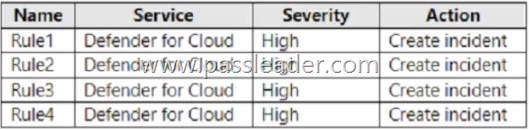
User1 performs an action that matches Rule1, Rule2, Rule3, and Rule4. How many incidents will be created in WS1?
A. 1
B. 2
C. 3
D. 4
Answer: D
Explanation:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/configure-email-notifications
NEW QUESTION 303
HotSpot
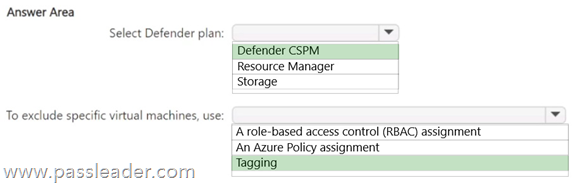
You have an Azure subscription that contains 50 virtual machines. You plan to deploy Microsoft Defender for Cloud. You need to enable agentless scanning for 40 virtual machines. The solution must create disk snapshots of the virtual machines and perform out-of-band analysis of the snapshots. What should you do? (To answer, select the appropriate options in the answer area.)
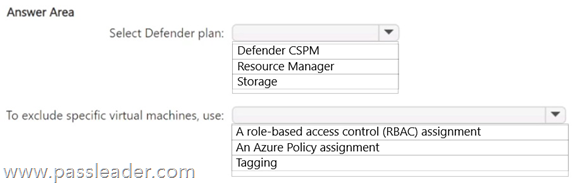
Explanation:
https://learn.microsoft.com/eN-us/azure/defender-for-cloud/concept-agentless-data-collection
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/azure-best-practices/resource-naming-and-tagging-decision-guide
NEW QUESTION 304
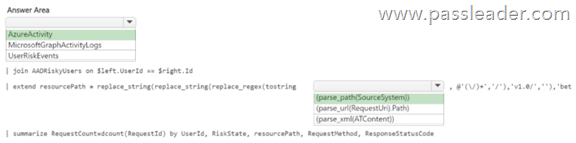
HotSpot
You have an Azure subscription that contains a Log Analytics workspace named Workspace1. You configure Azure activity logs and Microsoft Entra ID logs to be forwarded to Workspace1. You need to identify which Azure resources have been queried or modified by risky users. How should you complete the KQL query? (To answer, select the appropriate options in the answer area.)
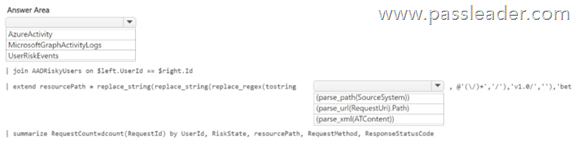
NEW QUESTION 305
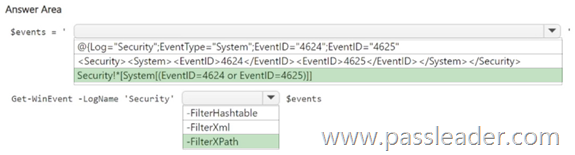
HotSpot
You have on-premises servers that run Windows Server. You have a Microsoft Sentinel workspace named SW1. SW1 is configured to collect Windows Security log entries from the servers by using the Azure Monitor Agent data connector. You plan to limit the scope of collected events to events 4624 and 4625 only. You need to use a PowerShell script to validate the syntax of the filter applied to the connector. How should you complete the script? (To answer, select the appropriate options in the answer area.)
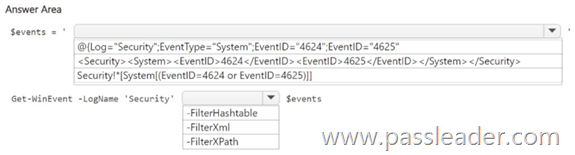
NEW QUESTION 306
Drag and Drop
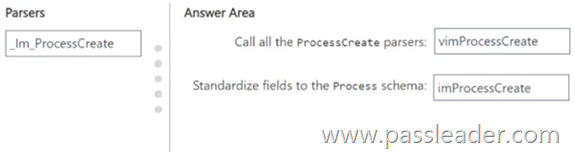
You have a Microsoft Sentinel workspace that contains the following Advanced Security Information Model (ASIM) parsers:
– _Im_ProcessCreate
– imProcessCreate
You create a new source-specific parser named vimProcessCreate. You need to modify the parsers to meet the following requirements:
– Call all the ProcessCreate parsers.
– Standardize fields to the Process schema.
Which parser should you modify to meet each requirement? (To answer, drag the appropriate parsers to the correct requirements. Each parser may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
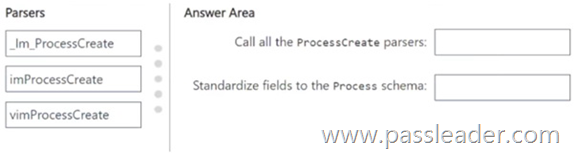
NEW QUESTION 307
……
Get the newest PassLeader SC-200 VCE dumps here: https://www.passleader.com/sc-200.html (311 Q&As Dumps –> 346 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-200 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE