Valid AZ-500 Dumps shared by PassLeader for Helping Passing AZ-500 Exam! PassLeader now offer the newest AZ-500 VCE dumps and AZ-500 PDF dumps, the PassLeader AZ-500 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader AZ-500 dumps with VCE and PDF here: https://www.passleader.com/az-500.html (367 Q&As Dumps –> 438 Q&As Dumps –> 531 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader AZ-500 dumps from Cloud Storage: https://drive.google.com/open?id=1CnqNGckypCByp19q05gCYQD-Qai7gnHt
NEW QUESTION 321
Your company has an Active Directory forest with a single domain, named weylandindustries.com. They also have an Azure Active Directory (Azure AD) tenant with the same name. You have been tasked with integrating Active Directory and the Azure AD tenant. You intend to deploy Azure AD Connect. Your strategy for the integration must make sure that password policies and user logon limitations affect user accounts that are synced to the Azure AD tenant, and that the amount of necessary servers are reduced.
Solution: You recommend the use of federation with Active Directory Federation Services (AD FS).
Does the solution meet the goal?
A. Yes
B. No
Answer: B
Explanation:
A federated authentication system relies on an external trusted system to authenticate users. Some companies want to reuse their existing federated system investment with their Azure AD hybrid identity solution. The maintenance and management of the federated system falls outside the control of Azure AD. It’s up to the organization by using the federated system to make sure it’s deployed securely and can handle the authentication load.
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
NEW QUESTION 322
Your Company’s Azure subscription includes a virtual network that has a single subnet configured. You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed. You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure SQL databases via the service endpoint. You need to perform a task on the virtual machine prior to deploying containers.
Solution: You install the container network interface (CNI) plug-in.
Does the solution meet the goal?
A. Yes
B. No
Answer: A
Explanation:
The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in supports both Linux and Windows platform. The plug-in assigns IP addresses from a virtual network to containers brought up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and virtual network resources. The plug-in doesn’t rely on overlay networks, or routes, for connectivity, and provides the same performance as virtual machines.
https://docs.microsoft.com/en-us/azure/virtual-network/container-networking-overview
NEW QUESTION 323
You are in the process of creating an Azure Kubernetes Service (AKS) cluster. The Azure Kubernetes Service (AKS) cluster must be able to connect to an Azure Container Registry. You want to make sure that Azure Kubernetes Service (AKS) cluster authenticates to the Azure Container Registry by making use of the auto-generated service principal.
Solution: You create an Azure Active Directory (Azure AD) role assignment.
Does the solution meet the goal?
A. Yes
B. No
Answer: A
Explanation:
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you need to create an Azure AD role assignment that grants the cluster’s service principal access to the container registry.
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
NEW QUESTION 324
Your company has Azure subscription linked to their Azure Active Directory (Azure AD) tenant. As a Global administrator for the tenant, part of your responsibilities involves managing Azure Security Center settings. You are currently preparing to create a custom sensitivity label.
Solution: You start by creating a custom sensitive information type.
Does the solution meet the goal?
A. Yes
B. No
Answer: A
Explanation:
https://docs.microsoft.com/en-us/office365/securitycompliance/customize-a-built-in-sensitive-information-type
NEW QUESTION 325
Your company’s Azure subscription is linked to their Azure Active Directory (Azure AD) tenant. After an internally developed application is registered in Azure AD, you are tasked with making sure that the application has the ability to access Azure Key Vault secrets on application the users’ behalf.
Solution: You configure a delegated permission with admin consent.
Does the solution meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 326
Your company has an Active Directory forest with a single domain, named weylandindustries.com. They also have an Azure Active Directory (Azure AD) tenant with the same name. After syncing all on-premises identities to Azure AD, you are informed that users with a givenName attribute starting with LAB should not be allowed to sync to Azure AD. Which of the following actions should you take?
A. You should make use of the Synchronization Rules Editor to create an attribute-based filtering rule.
B. You should configure a DNAT rule on the Firewall.
C. You should configure a network traffic filtering rule on the Firewall.
D. You should make use of Active Directory Users and Computers to create an attribute-based filtering rule.
Answer: A
Explanation:
Use the Synchronization Rules Editor and write attribute-based filtering rule.
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sync-change-the-configuration
NEW QUESTION 327
You have been tasked with applying conditional access policies for your company’s current Azure Active Directory (Azure AD). The process involves assessing the risk events and risk levels. Which of the following is the risk level that should be configured for users that have leaked credentials?
A. None
B. Low
C. Medium
D. High
Answer: D
Explanation:
http://www.rebeladmin.com/2018/09/step-step-guide-configure-risk-based-azure-conditional-access-policies/
NEW QUESTION 328
You have been tasked with configuring an access review, which you plan to assigned to a new collection of reviews. You also have to make sure that the reviews can be reviewed by resource owners. You start by creating an access review program and an access review control. You now need to configure the Reviewers. Which of the following should you set Reviewers to?
A. Selected users.
B. Members (Self).
C. Group Owners.
D. Anyone.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
https://docs.microsoft.com/en-us/azure/active-directory/governance/manage-programs-controls
NEW QUESTION 329
Your company recently created an Azure subscription. You have, subsequently, been tasked with making sure that you are able to secure Azure AD roles by making use of Azure Active Directory (Azure AD) Privileged Identity Management (PIM). Which of the following actions should you take FIRST?
A. You should sign up Azure Active Directory (Azure AD) Privileged Identity Management (PIM) for Azure AD roles.
B. You should consent to Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
C. You should discover privileged roles.
D. You should discover resources.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-getting-started
NEW QUESTION 330
Your company has an Azure Container Registry. You have been tasked with assigning a user a role that allows for the uploading of images to the Azure Container Registry. The role assigned should not require more privileges than necessary. Which of the following is the role you should assign?
A. Owner
B. Contributor
C. AcrPush
D. AcrPull
Answer: C
Explanation:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
NEW QUESTION 331
You make use of Azure Resource Manager templates to deploy Azure virtual machines. You have been tasked with making sure that Windows features that are not in use, are automatically inactivated when instances of the virtual machines are provisioned. Which of the following actions should you take?
A. You should make use of Azure DevOps.
B. You should make use of Azure Automation State Configuration.
C. You should make use of network security groups (NSG).
D. You should make use of Azure Blueprints.
Answer: B
Explanation:
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines. Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
NEW QUESTION 332
Your company’s Azure subscription includes Windows Server 2016 Azure virtual machines. You are informed that every virtual machine must have a custom antimalware virtual machine extension installed. You are writing the necessary code for a policy that will help you achieve this. Which of the following is an effect that must be included in your code?
A. Disabled
B. Modify
C. AuditIfNotExists
D. DeployIfNotExists
Answer: D
Explanation:
DeployIfNotExists executes a template deployment when the condition is met.
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
NEW QUESTION 333
You have been tasked with enabling Advanced Threat Protection for an Azure SQL Database server. Advanced Threat Protection must be configured to identify all types of threat detection. Which of the following will happen if when a faulty SQL statement is generate in the database by an application?
A. A Potential SQL injection alert is triggered.
B. A Vulnerability to SQL injection alert is triggered.
C. An Access from a potentially harmful application alert is triggered.
D. A Brute force SQL credentials alert is triggered.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-threat-detection-overview
NEW QUESTION 334
Your company has an Azure subscription that includes two virtual machines, named VirMac1 and VirMac2, which both have a status of Stopped (Deallocated). The virtual machines belong to different resource groups, named ResGroup1 and ResGroup2. You have also created two Azure policies that are both configured with the virtualMachines resource type. The policy configured for ResGroup1 has a policy definition of Not allowed resource types, while the policy configured for ResGroup2 has a policy definition of Allowed resource types. You then create a Read-only resource lock on VirMac1, as well as a Read-only resource lock on ResGroup2. Which of the following is TRUE with regards to the scenario? (Choose two.)
A. You will be able to start VirMac1.
B. You will NOT be able to start VirMac1.
C. You will be able to create a virtual machine in ResGroup2.
D. You will NOT be able to create a virtual machine in ResGroup2.
Answer: BC
Explanation:
https://docs.microsoft.com/en-us/azure/governance/blueprints/concepts/resource-locking
NEW QUESTION 335
You have been tasked with delegate administrative access to your company’s Azure key vault. You have to make sure that a specific user can set advanced access policies for the key vault. You also have to make sure that access is assigned based on the principle of least privilege. Which of the following options should you use to achieve your goal?
A. Azure Information Protection
B. RBAC
C. Azure AD Privileged Identity Management (PIM)
D. Azure DevOps
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
NEW QUESTION 336
You have been tasked with delegate administrative access to your company’s Azure key vault. You have to make sure that a specific user is able to add and delete certificates in the key vault. You also have to make sure that access is assigned based on the principle of least privilege. Which of the following options should you use to achieve your goal?
A. A key vault access policy.
B. Azure policy.
C. Azure AD Privileged Identity Management (PIM).
D. Azure DevOps.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
NEW QUESTION 337
You have an Azure virtual machine that runs Windows Server R2. You plan to deploy and configure an Azure Key vault, and enable Azure Disk Encryption for the virtual machine. Which of the following is TRUE with regards to Azure Disk Encryption for a Windows VM?
A. It is supported for basic tier VMs.
B. It is supported for standard tier VMs.
C. It is supported for VMs configured with software-based RAID systems.
D. It is supported for VMs configured with Storage Spaces Direct (S2D).
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/disk-encryption-windows
NEW QUESTION 338
You have an Azure virtual machine that runs Ubuntu 16.04-DAILY-LTS. You plan to deploy and configure an Azure Key vault, and enable Azure Disk Encryption for the virtual machine. Which of the following is TRUE with regards to Azure Disk Encryption for a Linux VM?
A. It is NOT supported for basic tier VMs.
B. It is NOT supported for standard tier VMs.
C. OS drive encryption for Linux virtual machine scale sets is supported.
D. Custom image encryption is supported.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/virtual-machines/linux/disk-encryption-linux
NEW QUESTION 339
You want to gather logs from a large number of Windows Server 2016 computers using Azure Log Analytics. You are configuring an Azure Resource Manager template to deploy the Microsoft Monitoring Agent to all the servers automatically. Which of the following should be included in the template? (Choose two.)
A. WorkspaceID
B. AzureADApplicationID
C. WorkspaceKey
D. StorageAccountKey
Answer: AC
Explanation:
https://blogs.technet.microsoft.com/manageabilityguys/2015/11/19/enabling-the-microsoft-monitoring-agent-in-windows-json-templates/
NEW QUESTION 340
You have a sneaking suspicion that there are users trying to sign in to resources which are inaccessible to them. You decide to create an Azure Log Analytics query to confirm your suspicions. The query will detect unsuccessful user sign-in attempts from the last few days. You want to make sure that the results only show users who had failed to sign-in more than five times. Which of the following should be included in your query?
A. The EventID and CountIf() parameters.
B. The ActivityID and CountIf() parameters.
C. The EventID and Count() parameters.
D. The ActivityID and Count() parameters.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/examples
NEW QUESTION 341
Your company uses Azure DevOps with branch policies configured. Which of the following is TRUE with regards to branch policies? (Choose two.)
A. It enforces your team’s change management standards.
B. It controls who can read and update the code in a branch.
C. It enforces your team’s code quality.
D. It places a branch into a read-only state.
Answer: AC
Explanation:
Branch policies help teams protect their important branches of development. Policies enforce your team’s code quality and change management standards.
https://docs.microsoft.com/en-us/azure/devops/repos/git/branch-policies?view=azure-devops&viewFallbackFrom=vsts
NEW QUESTION 342
After creating a new Azure subscription, you are tasked with making sure that custom alert rules can be created in Azure Security Center. You have created an Azure Storage account. Which of the following is the action you should take?
A. You should make sure that Azure Active Directory (Azure AD) Identity Protection is removed.
B. You should create a DLP policy.
C. You should create an Azure Log Analytics workspace.
D. You should make sure that Security Center has the necessary tier configured.
Answer: C
Explanation:
You need write permission in the workspace that you select to store your custom alert.
https://docs.microsoft.com/en-us/azure/security-center/security-center-custom-alert
NEW QUESTION 343
Your company’s Azure subscription includes an Azure Log Analytics workspace. Your company has a hundred on-premises servers that run either Windows Server 2012 R2 or Windows Server 2016, and is linked to the Azure Log Analytics workspace. The Azure Log Analytics workspace is set up to gather performance counters associated with security from these linked servers. You have been tasked with configuring alerts according to the information gathered by the Azure Log Analytics workspace. You have to make sure that alert rules allow for dimensions, and that alert creation time should be kept to a minimum. Furthermore, a single alert notification must be created when the alert is created and when the alert is sorted out. You need to make use of the necessary signal type when creating the alert rules. Which of the following is the option you should use?
A. You should make use of the Activity log signal type.
B. You should make use of the Application Log signal type.
C. You should make use of the Metric signal type.
D. You should make use of the Audit Log signal type.
Answer: C
Explanation:
Metric alerts in Azure Monitor provide a way to get notified when one of your metrics cross a threshold. Metric alerts work on a range of multi-dimensional platform metrics, custom metrics, Application Insights standard and custom metrics. Note: Signals are emitted by the target resource and can be of several types. Metric, Activity log, Application Insights, and Log.
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-metric
NEW QUESTION 344
Your company’s Azure subscription includes a hundred virtual machines that have Azure Diagnostics enabled. You have been tasked with retrieving the identity of the user that removed a virtual machine fifteen days ago. You have already accessed Azure Monitor. Which of the following options should you use?
A. Application Log
B. Metrics
C. Activity Log
D. Logs
Answer: C
Explanation:
Azure activity logs provide insight into the operations that were performed on resources in your subscription. Activity logs were previously known as “audit logs” or “operational logs,” because they report control-plane events for your subscriptions.
https://docs.microsoft.com/en-us/azure/security/azure-log-audit
NEW QUESTION 345
You have been tasked with making sure that you are able to modify the operating system security configurations via Azure Security Center. To achieve your goal, you need to have the correct pricing tier for Azure Security Center in place. Which of the following is the pricing tier required?
A. Advanced
B. Premium
C. Standard
D. Free
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/security-center-pricing
NEW QUESTION 346
You are in the process of configuring an Azure policy via the Azure portal. Your policy will include an effect that will need a managed identity for it to be assigned. Which of the following is the effect in question?
A. AuditIfNotExist
B. Disabled
C. DeployIfNotExist
D. EnforceOPAConstraint
Answer: C
Explanation:
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity.
https://docs.microsoft.com/bs-latn-ba/azure/governance/policy/how-to/remediate-resources
NEW QUESTION 347
You have been tasked with creating an Azure key vault using PowerShell. You have been informed that objects deleted from the key vault must be kept for a set period of 90 days. Which two of the following parameters must be used in conjunction to meet the requirement? (Choose two.)
A. EnabledForDeployment
B. EnablePurgeProtection
C. EnabledForTemplateDeployment
D. EnableSoftDelete
Answer: BD
Explanation:
https://docs.microsoft.com/en-us/powershell/module/azurerm.keyvault/new-azurermkeyvault
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-ovw-soft-delete
NEW QUESTION 348
Drag and Drop
Your company has an Azure SQL database that has Always Encrypted enabled. You are required to make the relevant information available to application developers to allow them to access data in the database. Which two of the following options should be made available? (Answer by dragging the correct options from the list to the answer area.)

Answer:
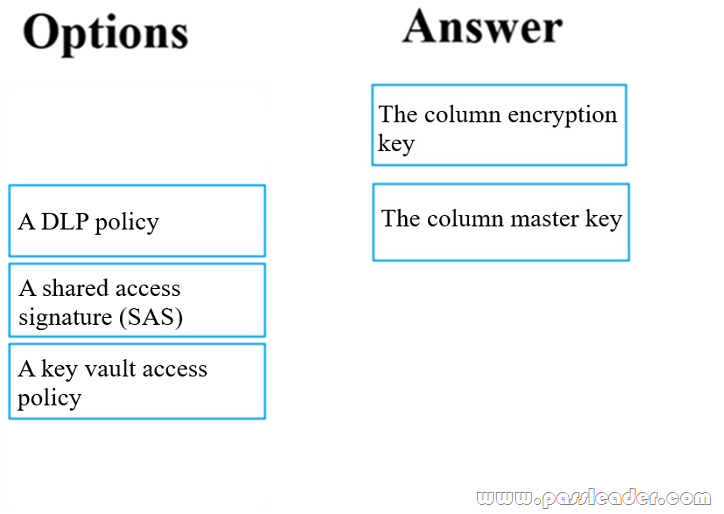
Explanation:
Always Encrypted uses two types of keys: column encryption keys and column master keys. A column encryption key is used to encrypt data in an encrypted column. A column master key is a key-protecting key that encrypts one or more column encryption keys.
https://docs.microsoft.com/en-us/sql/relational-databases/security/encryption/always-encrypted-database-engine
NEW QUESTION 349
……
Get the newest PassLeader AZ-500 VCE dumps here: https://www.passleader.com/az-500.html (367 Q&As Dumps –> 438 Q&As Dumps –> 531 Q&As Dumps)
And, DOWNLOAD the newest PassLeader AZ-500 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=1CnqNGckypCByp19q05gCYQD-Qai7gnHt