Valid SC-200 Dumps shared by PassLeader for Helping Passing SC-200 Exam! PassLeader now offer the newest SC-200 VCE dumps and SC-200 PDF dumps, the PassLeader SC-200 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-200 dumps with VCE and PDF here: https://www.passleader.com/sc-200.html (91 Q&As Dumps –> 116 Q&As Dumps –> 149 Q&As Dumps –> 217 Q&As Dumps –> 264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-200 dumps from Cloud Storage: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE
NEW QUESTION 71
You need to configure Microsoft Cloud App Security to generate alerts and trigger remediation actions in response to external sharing of confidential files. Which two actions should you perform in the Cloud App Security portal? (Each correct answer presents part of the solution. Choose two.)
A. From Settings, select Information Protection, select Azure Information Protection, and then select Only scan files for Azure Information Protection classification labels and content inspection warnings from this tenant.
B. Select Investigate files, and then filter App to Office 365.
C. Select Investigate files, and then select New policy from search.
D. From Settings, select Information Protection, select Azure Information Protection, and then select Automatically scan new files for Azure Information Protection classification labels and content inspection warnings.
E. From Settings, select Information Protection, select Files, and then enable file monitoring.
F. Select Investigate files, and then filter File Type to Document.
Answer: DE
Explanation:
https://docs.microsoft.com/en-us/cloud-app-security/tutorial-dlp
https://docs.microsoft.com/en-us/cloud-app-security/azip-integration
NEW QUESTION 72
You use Azure Security Center. You receive a security alert in Security Center. You need to view recommendations to resolve the alert in Security Center. What should you do?
A. From Security alerts, select the alert, select Take Action, and then expand the Prevent future attacks section.
B. From Security alerts, select Take Action, and then expand the Mitigate the threat section.
C. From Regulatory compliance, download the report.
D. From Recommendations, download the CSV report.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/security-center-managing-and-responding-alerts
NEW QUESTION 73
You have a suppression rule in Azure Security Center for 10 virtual machines that are used for testing. The virtual machines run Windows Server. You are troubleshooting an issue on the virtual machines. In Security Center, you need to view the alerts generated by the virtual machines during the last five days. What should you do?
A. Change the rule expiration date of the suppression rule.
B. Change the state of the suppression rule to Disabled.
C. Modify the filter for the Security alerts page.
D. View the Windows event logs on the virtual machines.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/alerts-suppression-rules
NEW QUESTION 74
You are investigating an incident in Azure Sentinel that contains more than 127 alerts. You discover eight alerts in the incident that require further investigation. You need to escalate the alerts to another Azure Sentinel administrator. What should you do to provide the alerts to the administrator?
A. Create a Microsoft incident creation rule.
B. Share the incident URL.
C. Create a scheduled query rule.
D. Assign the incident.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/investigate-cases
NEW QUESTION 75
You are configuring Azure Sentinel. You need to send a Microsoft Teams message to a channel whenever an incident representing a sign-in risk event is activated in Azure Sentinel. Which two actions should you perform in Azure Sentinel? (Each correct answer presents part of the solution. Choose two.)
A. Enable Entity behavior analytics.
B. Associate a playbook to the analytics rule that triggered the incident.
C. Enable the Fusion rule.
D. Add a playbook.
E. Create a workbook.
Answer: AB
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/enable-entity-behavior-analytics
https://docs.microsoft.com/en-us/azure/sentinel/automate-responses-with-playbooks
NEW QUESTION 76
You have the following environment:
– Azure Sentinel
– A Microsoft 365 subscription
– Microsoft Defender for Identity
– An Azure Active Directory (Azure AD) tenant
You configure Azure Sentinel to collect security logs from all the Active Directory member servers and domain controllers. You deploy Microsoft Defender for Identity by using standalone sensors. You need to ensure that you can detect when sensitive groups are modified in Active Directory. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Configure the Advanced Audit Policy Configuration settings for the domain controllers.
B. Modify the permissions of the Domain Controllers organizational unit (OU).
C. Configure auditing in the Microsoft 365 compliance center.
D. Configure Windows Event Forwarding on the domain controllers.
Answer: AD
Explanation:
https://docs.microsoft.com/en-us/defender-for-identity/configure-windows-event-collection
https://docs.microsoft.com/en-us/defender-for-identity/configure-event-collection
NEW QUESTION 77
You are configuring Azure Sentinel. You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a scheduled query rule for a data connector.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
NEW QUESTION 78
You are configuring Azure Sentinel. You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a Microsoft incident creation rule for a data connector.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
NEW QUESTION 79
You have an Azure subscription that has Azure Defender enabled for all supported resource types. You need to configure the continuous export of high-severity alerts to enable their retrieval from a third- party security information and event management (SIEM) solution. To which service should you export the alerts?
A. Azure Cosmos DB
B. Azure Event Grid
C. Azure Event Hubs
D. Azure Data Lake
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/continuous-export?tabs=azure-portal
NEW QUESTION 80
You are responsible for responding to Azure Defender for Key Vault alerts. During an investigation of an alert, you discover unauthorized attempts to access a key vault from a Tor exit node. What should you configure to mitigate the threat?
A. Key Vault firewalls and virtual networks.
B. Azure Active Directory (Azure AD) permissions.
C. Role-based access control (RBAC) for the key vault.
D. The access policy settings of the key vault.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/key-vault/general/network-security
NEW QUESTION 81
You have an Azure subscription that contains a Log Analytics workspace. You need to enable just-in-time (JIT) VM access and network detections for Azure resources. Where should you enable Azure Defender?
A. at the subscription level
B. at the workspace level
C. at the resource level
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/enable-azure-defender
NEW QUESTION 82
You use Azure Defender. You have an Azure Storage account that contains sensitive information. You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From Azure Security Center, enable workflow automation.
B. Create an Azure logic app that has a manual trigger.
C. Create an Azure logic app that has an Azure Security Center alert trigger.
D. Create an Azure logic app that has an HTTP trigger.
E. From Azure Active Directory (Azure AD), add an app registration.
Answer: AC
Explanation:
https://docs.microsoft.com/en-us/azure/storage/common/azure-defender-storage-configure?tabs=azure-security-center
https://docs.microsoft.com/en-us/azure/security-center/workflow-automation
NEW QUESTION 83
You recently deployed Azure Sentinel. You discover that the default Fusion rule does not generate any alerts. You verify that the rule is enabled. You need to ensure that the Fusion rule can generate alerts. What should you do?
A. Disable, and then enable the rule.
B. Add data connectors.
C. Create a new machine learning analytics rule.
D. Add a hunting bookmark.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/connect-data-sources
NEW QUESTION 84
A company uses Azure Sentinel. You need to create an automated threat response. What should you use?
A. a data connector
B. a playbook
C. a workbook
D. a Microsoft incident creation rule
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
NEW QUESTION 85
You have an Azure Sentinel deployment in the East US Azure region. You create a Log Analytics workspace named LogsWest in the West US Azure region. You need to ensure that you can use scheduled analytics rules in the existing Azure Sentinel deployment to generate alerts based on queries to LogsWest. What should you do first?
A. Deploy Azure Data Catalog to the West US Azure region.
B. Modify the workspace settings of the existing Azure Sentinel deployment.
C. Add Azure Sentinel to a workspace.
D. Create a data connector in Azure Sentinel.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/extend-sentinel-across-workspaces-tenants
NEW QUESTION 86
You create a custom analytics rule to detect threats in Azure Sentinel. You discover that the rule fails intermittently. What are two possible causes of the failures? (Each correct answer presents part of the solution. Choose two.)
A. The rule query takes too long to run and times out.
B. The target workspace was deleted.
C. Permissions to the data sources of the rule query were modified.
D. There are connectivity issues between the data sources and Log Analytics.
Answer: AD
NEW QUESTION 87
You implement Safe Attachments policies in Microsoft Defender for Office 365. Users report that email messages containing attachments take longer than expected to be received. You need to reduce the amount of time it takes to deliver messages that contain attachments without compromising security. The attachments must be scanned for malware, and any messages that contain malware must be blocked. What should you configure in the Safe Attachments policies?
A. Dynamic Delivery.
B. Replace.
C. Block and Enable redirect.
D. Monitor and Enable redirect.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/safe-attachments?view=o365-worldwide
NEW QUESTION 88
You receive a security bulletin about a potential attack that uses an image file. You need to create an indicator of compromise (IoC) in Microsoft Defender for Endpoint to prevent the attack. Which indicator type should you use?
A. a URL/domain indicator that has Action set to Alert only
B. a URL/domain indicator that has Action set to Alert and block
C. a file hash indicator that has Action set to Alert and block
D. a certificate indicator that has Action set to Alert and block
Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/indicator-file?view=o365-worldwide
NEW QUESTION 89
HotSpot
You are informed of an increase in malicious email being received by users. You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign-ins performed by the recipients within an hour of receiving the known malicious email. How should you complete the query? (To answer, select the appropriate options in the answer area.)
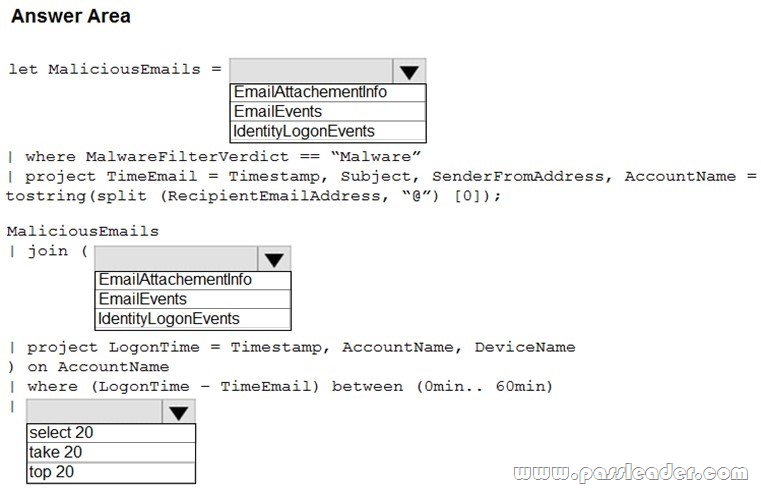
Answer:
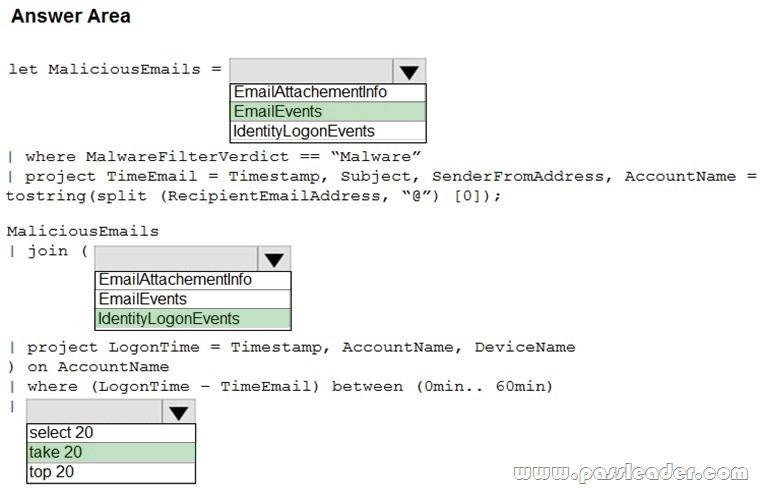
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/advanced-hunting-query-emails-devices?view=o365-worldwide
NEW QUESTION 90
Drag and Drop
Your company deploys Azure Sentinel. You plan to delegate the administration of Azure Sentinel to various groups. You need to delegate the following tasks:
– Create and run playbooks.
– Create workbooks and analytic rules.
The solution must use the principle of least privilege. Which role should you assign for each task? (To answer, drag the appropriate roles to the correct tasks. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
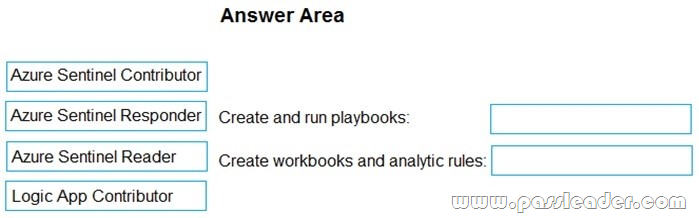
Answer:
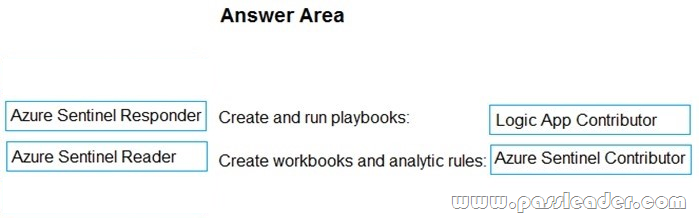
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/roles
NEW QUESTION 91
……
Get the newest PassLeader SC-200 VCE dumps here: https://www.passleader.com/sc-200.html (91 Q&As Dumps –> 116 Q&As Dumps –> 149 Q&As Dumps –> 217 Q&As Dumps –> 264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-200 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE