Valid SC-200 Dumps shared by PassLeader for Helping Passing SC-200 Exam! PassLeader now offer the newest SC-200 VCE dumps and SC-200 PDF dumps, the PassLeader SC-200 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-200 dumps with VCE and PDF here: https://www.passleader.com/sc-200.html (264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-200 dumps from Cloud Storage: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE
NEW QUESTION 228
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. You need to ensure that you can investigate threats by using data in the unified audit log of Microsoft Defender for Cloud Apps. What should you configure first?
A. the User enrichment settings
B. the Azure connector
C. the Office 365 connector
D. the Automatic log upload settings
Answer: C
Explanation:
https://learn.microsoft.com/en-us/defender-cloud-apps/connect-office-365
NEW QUESTION 229
You have an Azure subscription that uses Microsoft Defender for Servers Plan 1 and contains a server named Server1. You enable agentless scanning. You need to prevent Server1 from being scanned. The solution must minimize administrative effort. What should you do?
A. Create an exclusion tag.
B. Upgrade the subscription to Defender for Servers Plan 2.
C. Create a governance rule.
D. Create an exclusion group.
Answer: A
Explanation:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/enable-agentless-scanning-vms#exclude-machines-from-scanning
NEW QUESTION 230
You need to configure Microsoft Defender for Cloud Apps to generate alerts and trigger remediation actions in response to external sharing of confidential files. Which two actions should you perform in the Microsoft 365 Defender portal? (Each correct answer presents part of the solution. Choose two.)
A. From Settings, select Information Protection, select Azure Information Protection, and then select Only scan files for Azure Information Protection classification labels and content inspection warnings from this tenant.
B. From Cloud apps, select Files, and then filter File Type to Document.
C. From Settings, select Information Protection, select Files, and then enable file monitoring.
D. From Cloud apps, select Files, and then filter App to Office 365.
E. From Cloud apps, select Files, and then select New policy from search.
F. From Settings, select Information Protection, select Azure Information Protection, and then select Automatically scan new files for Azure Information Protection classification labels and content inspection warnings.
Answer: BF
NEW QUESTION 231
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. You need to identify any devices that triggered a malware alert and collect evidence related to the alert. The solution must ensure that you can use the results to initiate device isolation for the affected devices. What should you use in the Microsoft 365 Defender portal?
A. Incidents
B. Remediation
C. Investigations
D. Advanced Hunting
Answer: C
Explanation:
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/respond-machine-alerts?view=o365-worldwide
NEW QUESTION 232
You have an Azure subscription that uses Microsoft Defender for Cloud. You have a GitHub account named Account1 that contains 10 repositories. You need to ensure that Defender for Cloud can access the repositories in Account1. What should you do first in the Microsoft Defender for Cloud portal?
A. Enable integrations.
B. Enable a plan.
C. Add an environment.
D. Enable security policies.
Answer: C
Explanation:
To add an environment, you need to sign in to the Azure portal, go to Microsoft Defender for Cloud > Environment settings, select Add environment, and then select GitHub. You also need to enter a name, select your subscription, resource group, and region.
https://learn.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-github#connect-your-github-account
NEW QUESTION 233
You have a Microsoft Sentinel playbook that is triggered by using the Azure Activity connector. You need to create a new near-real-time (NRT) analytics rule that will use the playbook. What should you configure for the rule?
A. the incident automation settings
B. the query rule
C. entity mapping
D. the alert automation settings
Answer: B
Explanation:
To create an NRT rule, you need to follow these steps:
– From the Microsoft Sentinel navigation menu, select Analytics.
– Select Create from the button bar, then NRT query rule (preview) from the drop-down list.
– Follow the instructions of the analytics rule wizard.
NEW QUESTION 234
You need to visualize Microsoft Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC). What should you use?
A. Notebooks in Microsoft Sentinel
B. Microsoft Defender for Cloud Apps
C. Azure Monitor
Answer: A
Explanation:
Notebooks are interactive tools that allow you to run Python code, query data, perform machine learning, and create visualizations. Notebooks can help you hunt for threats, investigate incidents, and perform data analysis using Microsoft Sentinel data and external data sources.
NEW QUESTION 235
HotSpot
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD. You need to identify the 100 most recent sign-in attempts recorded on devices and AD DS domain controllers. How should you complete the KQL query? (To answer, select the appropriate options in the answer area.)
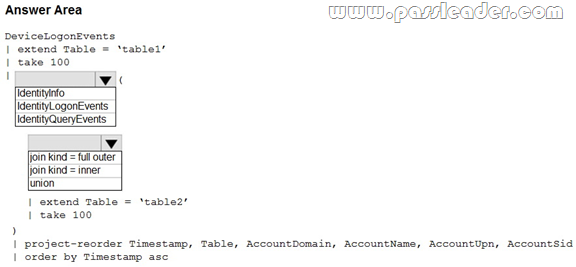
Answer:

Explanation:
Box 1: IdentityLogonEvents. The final column requires “AccountUpn.” Therefore, “IdentityInfo” would not be appropriate. Since it’s about sign-in attempts to ADDS domain controllers, “IdentityLogonEvents” would be the suitable choice.
Box 2: union. We need to extract the latest 100 sign-in attempts from BOTH “Devices” AND “ADDS domain controllers”. Using “union” would be optimal.
NEW QUESTION 236
HotSpot
You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD. You need to identify LDAP requests by AD DS users to enumerate AD DS objects. How should you complete the KQL query? (To answer, select the appropriate options in the answer area.)

Answer:

Explanation:
Box 1: IdentityQueryEvents. When considering a table with AccountSid and it’s about the LDAP request, it is “IdentityQueryEvents”.
Box 2: isnotempty. For determining whether there is a value in the AccountSid, it is “isnotempty”.
NEW QUESTION 237
HotSpot
Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD. You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. You need to identify all the interactive authentication attempts by the users in the finance department of your company. How should you complete the KQL query? (To answer, select the appropriate options in the answer area.)

Answer:

Explanation:
https://learn.microsoft.com/en-us/microsoft-365/security/defender/advanced-hunting-identitylogonevents-table?view=o365-worldwide
NEW QUESTION 238
HotSpot
You have a Microsoft 365 E5 subscription that uses Microsoft Purview and contains a user named User1. User1 shares a Microsoft Power BI report file from the Microsoft OneDrive folder of your company to an external user by using Microsoft Teams. You need to identify which Power BI report file was shared. How should you configure the search? (To answer, select the appropriate options in the answer area.)

NEW QUESTION 239
HotSpot
You have an Azure subscription named Sub1 that uses Microsoft Defender for Cloud. You have an Azure DevOps organization named AzDO1. You need to integrate Sub1 and AzDO1. The solution must meet the following requirements:
– Detect secrets exposed in pipelines by using Defender for Cloud.
– Minimize administrative effort.
What should you do? (To answer, select the appropriate options in the answer area.)

Answer:

Explanation:
https://learn.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-devops?branch=main
https://learn.microsoft.com/en-us/azure/defender-for-cloud/azure-devops-extension
NEW QUESTION 240
HotSpot
You have a Microsoft Sentinel workspace named sws1. You need to create a query that will detect when a user creates an unusually large numbers of Azure AD user accounts. How should you complete the query? (To answer, select the appropriate options in the answer area.)
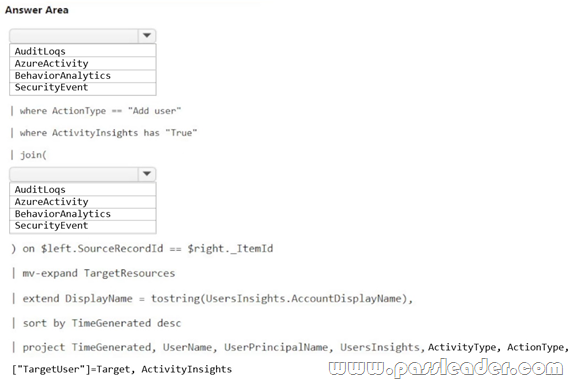
NEW QUESTION 241
HotSpot
You have a custom detection rule that includes the following KQL query:

For each of the following statements, select Yes if True. Otherwise, select No.
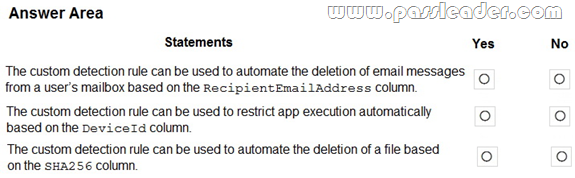
Answer:

Explanation:
https://learn.microsoft.com/en-us/microsoft-365/security/defender/custom-detection-rules?view=o365-worldwide#4-specify-actions
NEW QUESTION 242
……
Get the newest PassLeader SC-200 VCE dumps here: https://www.passleader.com/sc-200.html (264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-200 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE

