Valid SC-200 Dumps shared by PassLeader for Helping Passing SC-200 Exam! PassLeader now offer the newest SC-200 VCE dumps and SC-200 PDF dumps, the PassLeader SC-200 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-200 dumps with VCE and PDF here: https://www.passleader.com/sc-200.html (346 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-200 dumps from Cloud Storage: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE
NEW QUESTION 320
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 500 Windows devices. As part of an incident investigation, you identify the following suspected malware files:
– sys
– pdf
– docx
– xlsx
You need to create indicator hashes to block users from downloading the files to the devices. Which files can you block by using the indicator hashes?
A. File1.sys only.
B. File1.sys and File3.docx only.
C. File1.sys, File3.docx, and File4.xlsx only.
D. File2.pdf, File3.docx, and File4.xlsx only.
E. File1.sys, File2.pdf, File3.docx, and File4.xlsx.
Answer: E
Explanation:
Based on File hashes, you should be able to block each and every file with this hash, regardless the name of the file.
NEW QUESTION 321
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint and contains a user named User1 and a Microsoft 365 group named Group1. All users are assigned a Defender for Endpoint Plan 1 license. You enable Microsoft Defender XDR Unified role-based access control (RBAC) for Endpoints & Vulnerability Management. You need to ensure that User1 can configure alerts that will send email notifications to Group1. The solution must follow the principle of least privilege. Which permissions should you assign to User1?
A. Defender Vulnerability Management – Remediation handling.
B. Alerts investigation.
C. Live response capabilities: Basic.
D. Manage security settings.
Answer: D
NEW QUESTION 322
You have an Azure subscription named Sub1 that uses Microsoft Defender for Cloud. You need to assign the PCI DSS 4.0 initiative to Sub1 and have the initiative displayed in the Defender for Cloud Regulatory compliance dashboard. From Security policies in the Environment settings, you discover that the option to add more industry and regulatory standards is unavailable. What should you do first?
A. Configure the Continuous export settings for Log Analytics.
B. Enable the Cloud Security Posture Management (CSPM) plan for the subscription.
C. Configure the Continuous export settings for Azure Event Hubs.
D. Disable the Microsoft Cloud Security Benchmark (MCSB) assignment.
Answer: B
NEW QUESTION 323
You have a Microsoft Sentinel workspace named SW1. You need to identify which anomaly rules are enabled in SW1. What should you review in Microsoft Sentinel?
A. Content hub.
B. Entity behavior.
C. Analytics.
D. Settings.
Answer: C
NEW QUESTION 324
You have an Azure subscription that contains a Microsoft Sentinel workspace named WS1. You create a hunting query that detects a new attack vector. The attack vector maps to a tactic listed in the MITRE ATT&CK database. You need to ensure that an incident is created in WS1 when the new attack vector is detected. What should you configure?
A. a hunting livestream session
B. a query bookmark
C. a scheduled query rule
D. a Fusion rule
Answer: C
NEW QUESTION 325
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR. The security team at your company detects command and control (C2) agent traffic on the network. Agents communicate once every 50 hours. You need to create a Microsoft Defender XDR custom detection rule that will identify compromised devices and establish a pattern of communication. The solution must meet the following requirements:
– Identify all the devices that have communicated during the past 14 days.
– Minimize how long it takes to identify the devices.
To what should you set the detection frequency for the rule?
A. Every 12 hours.
B. Every 24 hours.
C. Every three hours.
D. Every hour.
Answer: A
NEW QUESTION 326
You have a Microsoft 365 E5 subscription. Automated investigation and response (AIR) is enabled in Microsoft Defender for Office 365 and devices use full automation in Microsoft Defender for Endpoint. You have an incident involving a user that received malware-infected email messages on a managed device. Which action requires manual remediation of the incident?
A. soft deleting the email message
B. hard deleting the email message
C. isolating the device
D. containing the device
Answer: C
NEW QUESTION 327
You have a Microsoft 365 subscription that uses Microsoft Defender XDR and contains a Windows device named Device1. The timeline of Device1 includes three files named File1.ps1, File2.exe, and File3.dll. You need to submit files for deep analysis in Microsoft Defender XDR. Which files can you submit?
A. File1.ps1 only.
B. File2.exe only.
C. File3.dll only.
D. File2.exe and File3.dll only.
E. File1.ps1 and File2.exe only.
F. File1.ps1, File2.exe, and File3.dll.
Answer: D
Explanation:
Deep analysis currently supports extensive analysis of portable executable (PE) files (including .exe and .dll files). PE files typically have .exe or .dll extensions (executable programs or applications).
https://learn.microsoft.com/en-us/defender-endpoint/respond-file-alerts#deep-analysis
NEW QUESTION 328
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. You need to identify all the entities affected by an incident. Which tab should you use in the Microsoft Defender portal?
A. Investigations
B. Assets
C. Evidence and Response
D. Alerts
Answer: C
NEW QUESTION 329
You have a Microsoft 365 subscription that uses Microsoft Defender XDR. You are investigating an attacker that is known to use the Microsoft Graph API as an attack vector. The attacker performs the tactics shown the following table:
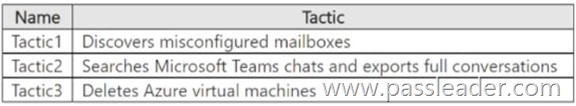
You need to search for malicious activities in your organization. Which tactics can you analyze by using the MicrosoftGraphActivityLogs table?
A. Tactic1 only.
B. Tactic2 only.
C. Tactic1 and Tactic3 only.
D. Tactic2 and Tactic3 only.
E. Tactic1, Tactic2, and Tactic3.
Answer: E
NEW QUESTION 330
HotSpot
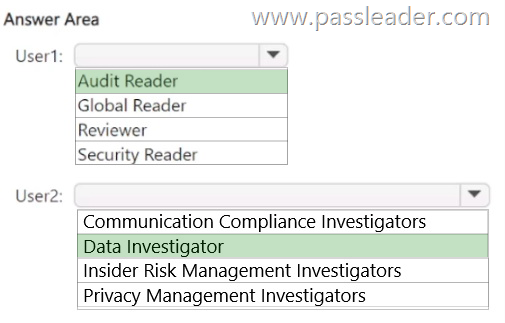
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains two users named User1 and User2. You need to ensure that the users can perform searches by using the Microsoft Purview portal. The solution must meet the following requirements:
– Ensure that User1 can search the Microsoft Purview Audit service logs and review the Microsoft Purview Audit service configuration.
– Ensure that User2 can search Microsoft Exchange Online mailboxes.
– Follow the principle of least privilege.
To which Microsoft Purview role group should you add each user? (To answer, select the appropriate options in the answer area.)
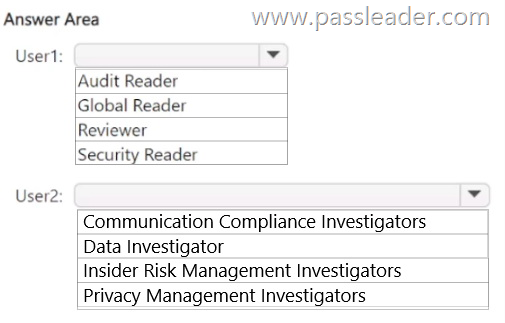
NEW QUESTION 331
HotSpot
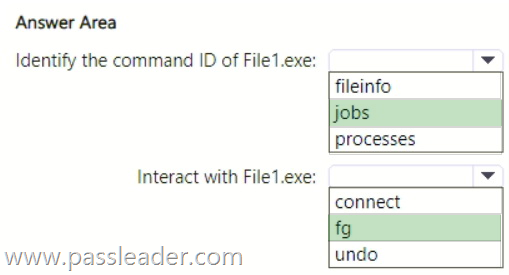
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device1. You initiate a live response session on Device1 and launch an executable file named File1.exe in the background. You need to perform the following actions:
– Identify the command ID of File1.exe.
– Interact with File1.exe.
Which live response command should you run for each action? (To answer, select the appropriate options in the answer area.)
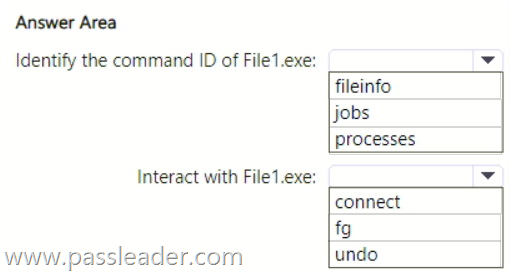
Explanation:
https://learn.microsoft.com/en-us/defender-endpoint/live-response
NEW QUESTION 332
……
Get the newest PassLeader SC-200 VCE dumps here: https://www.passleader.com/sc-200.html (346 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-200 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE