Valid SC-200 Dumps shared by PassLeader for Helping Passing SC-200 Exam! PassLeader now offer the newest SC-200 VCE dumps and SC-200 PDF dumps, the PassLeader SC-200 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-200 dumps with VCE and PDF here: https://www.passleader.com/sc-200.html (116 Q&As Dumps –> 149 Q&As Dumps –> 217 Q&As Dumps –> 264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-200 dumps from Cloud Storage: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE
NEW QUESTION 101
You are configuring Microsoft Defender for Identity integration with Active Directory. From the Microsoft Defender for identity portal, you need to configure several accounts for attackers to exploit.
Solution: You add each account as a Sensitive account.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://docs.microsoft.com/en-us/defender-for-identity/manage-sensitive-honeytoken-accounts
NEW QUESTION 102
You have Linux virtual machines on Amazon Web Services (AWS). You deploy Azure Defender and enable auto-provisioning. You need to monitor the virtual machines by using Azure Defender.
Solution: You enable Azure Arc and onboard the virtual machines to Azure Arc.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-machines?pivots=azure-arc
NEW QUESTION 103
You are configuring Azure Sentinel. You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a livestream from a query.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center
NEW QUESTION 104
Your company has a single office in Istanbul and a Microsoft 365 subscription. The company plans to use conditional access policies to enforce multi-factor authentication (MFA). You need to enforce MFA for all users who work remotely. What should you include in the solution?
A. a fraud alert
B. a user risk policy
C. a named location
D. a sign-in user policy
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
NEW QUESTION 105
You are configuring Microsoft Cloud App Security. You have a custom threat detection policy based on the IP address ranges of your company’s United States-based offices. You receive many alerts related to impossible travel and sign-ins from risky IP addresses. You determine that 99% of the alerts are legitimate sign-ins from your corporate offices. You need to prevent alerts for legitimate sign-ins from known locations. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Configure automatic data enrichment.
B. Add the IP addresses to the corporate address range category.
C. Increase the sensitivity level of the impossible travel anomaly detection policy.
D. Add the IP addresses to the other address range category and add a tag.
E. Create an activity policy that has an exclusion for the IP addresses.
Answer: AD
NEW QUESTION 106
You have a Microsoft 365 tenant that uses Microsoft Exchange Online and Microsoft Defender for Office 365. What should you use to identify whether zero-hour auto purge (ZAP) moved an email message from the mailbox of a user?
A. the Threat Protection Status report in Microsoft Defender for Office 365
B. the mailbox audit log in Exchange
C. the Safe Attachments file types report in Microsoft Defender for Office 365
D. the mail flow report in Exchange
Answer: A
Explanation:
To determine if ZAP moved your message, you can use either the Threat Protection Status report or Threat Explorer (and real-time detections).
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/zero-hour-auto-purge?view=o365-worldwide
NEW QUESTION 107
You have a Microsoft 365 subscription that contains 1,000 Windows 10 devices. The devices have Microsoft Office 365 installed. You need to mitigate the following device threats:
– Microsoft Excel macros that download scripts from untrusted websites.
– Users that open executable attachments in Microsoft Outlook.
– Outlook rules and forms exploits.
What should you use?
A. Microsoft Defender Antivirus
B. attack surface reduction rules in Microsoft Defender for Endpoint
C. Windows Defender Firewall
D. adaptive application control in Azure Defender
Answer: B
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/overview-attack-surface-reduction?view=o365-worldwide
NEW QUESTION 108
You have a third-party security information and event management (SIEM) solution. You need to ensure that the SIEM solution can generate alerts for Azure Active Directory (Azure AD) sign-events in near real time. What should you do to route events to the SIEM solution?
A. Create an Azure Sentinel workspace that has a Security Events connector.
B. Configure the Diagnostics settings in Azure AD to stream to an event hub.
C. Create an Azure Sentinel workspace that has an Azure Active Directory connector.
D. Configure the Diagnostics settings in Azure AD to archive to a storage account.
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/overview-monitoring
NEW QUESTION 109
You create an Azure subscription. You enable Azure Defender for the subscription. You need to use Azure Defender to protect on-premises computers. What should you do on the on-premises computers?
A. Install the Log Analytics agent.
B. Install the Dependency agent.
C. Configure the Hybrid Runbook Worker role.
D. Install the Connected Machine agent.
Answer: A
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/security-center-enable-data-collection
NEW QUESTION 110
A security administrator receives email alerts from Azure Defender for activities such as potential malware uploaded to a storage account and potential successful brute force attacks. The security administrator does NOT receive email alerts for activities such as antimalware action failed and suspicious network activity. The alerts appear in Azure Security Center. You need to ensure that the security administrator receives email alerts for all the activities. What should you configure in the Security Center settings?
A. the severity level of email notifications
B. a cloud connector
C. the Azure Defender plans
D. the integration settings for Threat detection
Answer: A
Explanation:
https://techcommunity.microsoft.com/t5/microsoft-365-defender/get-email-notifications-on-new-incidents-from-microsoft-365/ba-p/2012518
NEW QUESTION 111
You have an Azure subscription that contains a virtual machine named VM1 and uses Azure Defender. Azure Defender has automatic provisioning enabled. You need to create a custom alert suppression rule that will supress false positive alerts for suspicious use of PowerShell on VM1. What should you do first?
A. From Azure Security Center, add a workflow automation.
B. On VM1, run the Get-MPThreatCatalog cmdlet.
C. On VM1 trigger a PowerShell alert.
D. From Azure Security Center, export the alerts to a Log Analytics workspace.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/manage-alerts?view=o365-worldwide
NEW QUESTION 112
You use Azure Sentinel. You need to use a built-in role to provide a security analyst with the ability to edit the queries of custom Azure Sentinel workbooks. The solution must use the principle of least privilege. Which role should you assign to the analyst?
A. Azure Sentinel Contributor
B. Security Administrator
C. Azure Sentinel Responder
D. Logic App Contributor
Answer: A
Explanation:
Azure Sentinel Contributor can create and edit workbooks, analytics rules, and other Azure Sentinel resources.
https://docs.microsoft.com/en-us/azure/sentinel/roles
NEW QUESTION 113
You create a hunting query in Azure Sentinel. You need to receive a notification in the Azure portal as soon as the hunting query detects a match on the query. The solution must minimize effort. What should you use?
A. a playbook
B. a notebook
C. a livestream
D. a bookmark
Answer: C
Explanation:
Use livestream to run a specific query constantly, presenting results as they come in.
https://docs.microsoft.com/en-us/azure/sentinel/hunting
NEW QUESTION 114
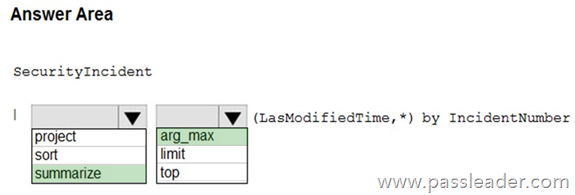
HotSpot
You need to create a query for a workbook. The query must meet the following requirements:
– List all incidents by incident number.
– Only include the most recent log for each incident.
How should you complete the query? (To answer, select the appropriate options in the answer area.)
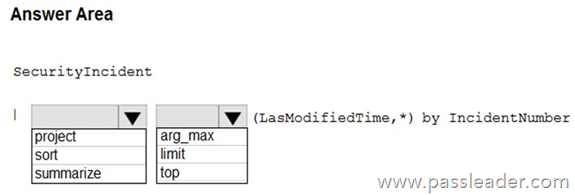
Explanation:
https://www.drware.com/whats-new-soc-operational-metrics-now-available-in-sentinel/
NEW QUESTION 115
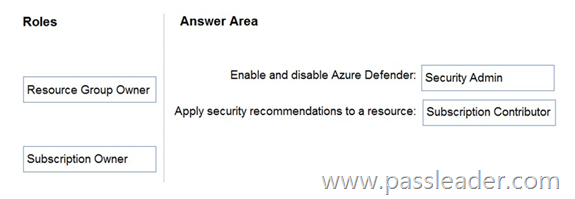
Drag and Drop
You have an Azure subscription. You need to delegate permissions to meet the following requirements:
– Enable and disable Azure Defender.
– Apply security recommendations to resource.
The solution must use the principle of least privilege. Which Azure Security Center role should you use for each requirement? (To answer, drag the appropriate roles to the correct requirements. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
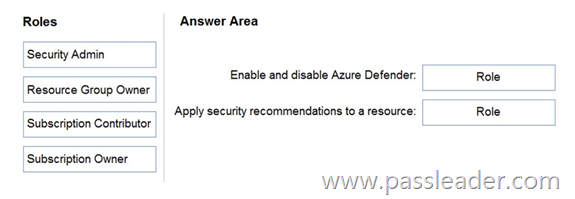
Explanation:
https://docs.microsoft.com/en-us/azure/security-center/security-center-permissions
NEW QUESTION 116
……
Get the newest PassLeader SC-200 VCE dumps here: https://www.passleader.com/sc-200.html (116 Q&As Dumps –> 149 Q&As Dumps –> 217 Q&As Dumps –> 264 Q&As Dumps –> 282 Q&As Dumps –> 311 Q&As Dumps –> 346 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-200 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1D7sX6DDpE-AaGl4QV9bMBXnyAbBcL2CE