Valid MD-100 Dumps shared by PassLeader for Helping Passing MD-100 Exam! PassLeader now offer the newest MD-100 VCE dumps and MD-100 PDF dumps, the PassLeader MD-100 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader MD-100 dumps with VCE and PDF here: https://www.passleader.com/md-100.html (315 Q&As Dumps –> 428 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader MD-100 dumps from Cloud Storage: https://drive.google.com/open?id=1nN5vMaeSbKiqjJwy-Y8KG-xvZL876tCK
NEW QUESTION 295
You have 10 new Windows 10 devices. You plan to deploy a provisioning package that will configure a wireless network profile. You need to ensure that a support technician can install the provisioning package on the devices. The solution must use the principle of least privilege. To which group should you add the support technician?
A. Users
B. Power Users
C. Network Configuration Operators
D. Administrators
Answer: D
Explanation:
https://docs.microsoft.com/en-us/windows/configuration/provisioning-packages/provisioning-apply-package
NEW QUESTION 296
You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data. You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit privilege use.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Files and folders are objects and are audited through object access, not though privilege use.
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
NEW QUESTION 297
Your company has an on-premises network that contains an Active Directory domain. The domain is synced to Microsoft Azure Active Directory (Azure AD). All computers in the domain run Windows 10 Enterprise. You have a computer named Computer1 that has a folder named C:\Folder1. You want to use File History to protect C:\Folder1.
Solution: You enable File History on Computer1. You then enable archiving for Folder1.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
File History only backs up copies of files that are in Libraries, and Desktop folders and the OneDrive files available offline on your PC. If you have files or folders elsewhere that you want backed up, you can add them to one of these folders.
https://support.microsoft.com/en-us/help/17128/windows-8-file-history
NEW QUESTION 298
Your network contains an Active Directory domain that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. The company plans to purchase computers preinstalled with Windows 10 Pro for all users. The company the following requirements:
– The new computers must be upgraded to Windows 10 Enterprise automatically.
– The new computers must be joined to Azure AD automatically when the user starts the new computers for the first time.
– The users must not be required to accept the End User License Agreement (EULA).
You need to deploy the new computers. What should you do?
A. Make use of the wipe and load refresh deployment method.
B. Perform in-place upgrade on the new computers.
C. Provide provisioning packages for the new computers.
D. Make use of Windows Autopilot.
Answer: D
Explanation:
Windows Autopilot is a collection of technologies used to set up and pre-configure new devices, getting them ready for productive use. You can also use Windows Autopilot to reset, repurpose and recover devices. The OEM Windows 10 installation on the new computers can be transformed into a “business-ready” state, applying settings and policies, installing apps, and even changing the edition of Windows 10 being used (e.g. from Windows 10 Pro to Windows 10 Enterprise) to support advanced features. The only interaction required from the end user is to connect to a network and to verify their credentials. Everything beyond that is automated.
https://docs.microsoft.com/en-us/windows/deployment/windows-autopilot/windows-autopilot
NEW QUESTION 299
Your company is not connected to the internet. The company purchases several new computers with Windows 10 Pro for its users. None of the new computers are activated. You need to activate the computers without connecting the network to the Internet. What should you do?
A. Make use of the Volume Activation Management Tool (VAMT).
B. Make use of the Key Management Service (KMS).
C. Make use of the Windows Process Activation Service.
D. Run the Get-WmiObject -query cmdlet.
Answer: B
Explanation:
You can configure one of the computers as a Key Management Service (KMS) host and activate the KMS host by phone. The other computers in the isolated network can then activate using the KMS host. Installing a KMS host key on a computer running Windows 10 allows you to activate other computers running Windows 10 against this KMS host and earlier versions of the client operating system, such as Windows 8.1 or Windows 7. Clients locate the KMS server by using resource records in DNS, so some configuration of DNS may be required. This scenario can be beneficial if your organization uses volume activation for clients and MAK-based activation for a smaller number of servers. To enable KMS functionality, a KMS key is installed on a KMS host; then, the host is activated over the Internet or by phone using Microsoft’s activation services.
https://docs.microsoft.com/en-us/windows/deployment/volume-activation/activate-using-key-management-service-vamt
NEW QUESTION 300
Your network contains an Active Directory domain. All users have been issued with computers that run Windows 8.1. A user named Mia Hamm has a computer named Computer1. You upgrade Computer1 to Windows 10 by performing a clean installation of Windows 10 without formatting the drives. You need to migrate the settings for Mia Hamm from Windows 8.1 to Windows 10. Which two actions should you perform? (Choose two.)
A. Run scanstate.exe and specify the C:\Users folder.
B. Run loadstate.exe and specify the C:\Windows.old folder.
C. Run usmultils.exe and specify the C:\Users folder.
D. Run scanstate.exe and specify the C:\Windows.old folder.
E. Run loadstate.exe and specify the C:\Users folder.
F. Run usmultils.exe and specify the C:\Windows.old folder.
Answer: DE
Explanation:
D: As we have performed a clean installation of Windows 10 without formatting the drives, User1’s Windows 8.1 user profile will be located in the \Windows.old folder. Therefore, we need to run scanstate.exe on the \Windows.old folder.
E: User1’s Windows 10 profile will be in the C:\Users folder so we need to run loadstate.exe to apply the changes in the C:\Users folder.
https://docs.microsoft.com/en-us/windows/deployment/usmt/usmt-how-it-works
https://docs.microsoft.com/en-us/windows/deployment/usmt/usmt-common-migration-scenarios#bkmk-fourpcrefresh
NEW QUESTION 301
You have a computer named Computer1 that runs Windows 10. You deploy an application named Application1 to Computer1. You need to assign credentials to Application1. You need to meet the following requirements:
– Ensure that the credentials for Application1 cannot be used by any user to log on to Computer1.
– Ensure that the principle of least privilege is maintained.
What should you do?
A. Configure Application1 to sign in as the Local System account and select the Allow service to interact with desktop check box.
B. Create a user account for Application1 and assign that user account the Deny log on locally user right.
C. Create a user account for Application1 and assign that user account the Deny log on as a service user right.
D. Configure Application1 to sign in as the Local Service account and select the Allow service to interact with desktop check box.
Answer: B
Explanation:
By using the Service1 account as the identity used by Application1, we are applying the principle of least privilege as required in this question. However, the Service1 account could be used by a user to sign in to the desktop on the computer. To sign in to the desktop on the computer, an account needs the log on locally right which all user accounts have by default. Therefore, we can prevent this by assigning Service1 the deny log on locally user right.
Incorrect:
Not A: Configuring Application1 to sign in as the Local System account would ensure that the identity used by Application1 cannot be used by a user to sign in to the desktop on Computer1. However, this does not use the principle of least privilege. The Local System account has full access to the system. Therefore, this solution does not meet the goal.
Not C: A service account needs the log on as a service user right. When you assign an account to be used by a service, that account is granted the log on as a service user right. Therefore, assigning Service1 the deny log on as a service user right would mean the service would not function.
Not D: The Local Service Account is a predefined local account used by the service control manager.
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/deny-log-on-locally
NEW QUESTION 302
Your network contains an Active Directory domain that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. All users have been issued with laptop computers as well as desktop computers that run Windows 10 Enterprise. All users have Microsoft 365 E3 licenses. A user named Mia Hamm informs you that she must perform a BitLocker recovery on her laptop but she does not have her BitLocker recovery key. You need to ensure that Mia Hamm can perform a BitLocker recovery on her laptop. What should you do?
A. Instruct Mia Hamm to log on to her desktop computer and run the repair-bde.exe command.
B. Instruct Mia Hamm to use the BitLocker Recovery Password Viewer to view the computer object of the laptop.
C. Instruct Mia Hamm to log on to her desktop computer and go to https://account.activedirectory.windowsazure.com and view the user account profile.
D. Instruct Mia Hamm to run the Enable-BitLocker cmdlet on her laptop.
Answer: C
Explanation:
The BitLocker recovery key is stored in Azure Active Directory.
https://celedonpartners.com/blog/storing-recovering-bitlocker-keys-azure-active-directory/
NEW QUESTION 303
Your company has an on-premises network that contains an Active Directory domain. The domain is synced to Microsoft Azure Active Directory (Azure AD). All computers in the domain run Windows 10 Enterprise. You have a computer named Computer1 that has a folder named Folder1. You must provide users in group named Group1 with the ability to view the list of files in Folder1. Your solution must ensure that the principle of least privilege is maintained. What should you do?
A. Assign the Full control permissions for the Folder1 folder to Group1.
B. Assign the Read permissions for the Folder1 folder to Group1.
C. Assign the List folder permissions for the Folder1 folder to Group1.
D. Assign the Take ownership permissions for the Folder1 folder to Group1.
Answer: C
Explanation:
https://www.online-tech-tips.com/computer-tips/set-file-folder-permissions-windows/
NEW QUESTION 304
You have a computer named Computer1 that runs Windows 10. Computer1 has a folder named C:\Folder1. You need to meet the following requirements:
– Log users that access C:\Folder1.
– Log users that modify and delete files in C:\Folder1.
Which two actions should you perform?
A. From the properties of C:\Folder1, configure the Auditing settings.
B. From the properties of C:\Folder1, select the Encryption contents to secure data option.
C. From the Audit Policy in the local Group Policy, configure Audit directory service access.
D. From the Audit Policy in the local Group Policy, you configure Audit object access.
E. From the Audit Policy in the local Group Policy, you configure Audit system events.
Answer: AD
Explanation:
Files and folders are objects and are audited through object access.
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
NEW QUESTION 305
Your company has a computer named Computer1 that runs Windows 10. Computer1 is used to provide guests with access to the Internet. Computer1 is a member of a workgroup. You want to configure Computer1 to use a user account sign in automatically when the the computer is started. The user must not be prompted for a user name and password. What should you do?
A. Configure Group Policy preferences.
B. Run the BCDBoot command.
C. Edit the Registry.
D. Run the MSConfig command.
Answer: C
Explanation:
In the registry, add a default user name and a default password in the HKEY_LOCAL_MACHINE \SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon sbukey.
https://support.microsoft.com/en-us/help/324737/how-to-turn-on-automatic-logon-in-windows
NEW QUESTION 306
Your network contains an Active Directory domain. The domain contains computers that run Windows 10. You must ensure that Windows BitLocker Drive Encryption is enabled on all client computers, even though a Trusted Platform Module (TPM) chip is installed in only some of them. You need to accomplish this goal by using one Group Policy object (GPO). What should you do?
A. Enable the Allow enhanced PINs for startup policy setting, and select the Allow BitLocker without a compatible TPM check box.
B. Enable the Enable use of BitLocker authentication requiring preboot keyboard input on slates policy setting, and select the Allow BitLocker without a compatible TPM check box.
C. Enable the Require additional authentication at startup policy setting, and select the Allow BitLocker without a compatible TPM check box.
D. Enable the Control use of BitLocker on removable drives policy setting, and select the Allow BitLocker without a compatible TPM check box.
Answer: C
Explanation:
We need to allow Windows BitLocker Drive Encryption on all client computers (including client computers that do not have Trusted Platform Module (TPM) chip). We can do this by enabling the option to allow BitLocker without a compatible TPM in the group policy. The “Allow BitLocker without a compatible TPM” option is a checkbox in the “Require additional authentication at startup” group policy setting. To access the “Allow BitLocker without a compatible TPM” checkbox, you need to first select Enabled on the “Require additional authentication at startup” policy setting.
https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-group-policy-settings#bkmk-unlockpol4
NEW QUESTION 307
You have a computer named Computer1. Computer1 runs Windows 10 Pro. Computer1 is experiencing connectivity issues. You need to view the IP addresses of any remote computer that Computer1 has an active TCP connection to. Should you do?
A. In Windows Administrative Tools, open Performance Monitor.
B. In the Control Panel, open Network and Internet. Then select Network and Sharing Center.
C. In Windows Administrative Tools, open Resource Monitor.
D. In the Setting app, open Update and Security. Then open Windows Security and select Firewall and Network protection.
Answer: C
NEW QUESTION 308
You have a computer named Computer1. Computer1 runs Windows 10 Pro. You attempt to start Computer1 but you receive the following error message:
“Bootmgr is missing.”
You need to be able to start Computer1. What should you do?
A. Start the computer in recovery mode and run the bootrec /rebuildbcd command.
B. Start the computer in recovery mode and run the diskpart /repair command.
C. Start the computer in recovery mode and run the bcdboot /s command.
D. Start the computer in recovery mode and run the bootcfg /debug command.
Answer: A
Explanation:
https://neosmart.net/wiki/bootmgr-is-missing/
NEW QUESTION 309
Your company has several mobile devices that run Windows 10. You need configure the mobile devices to meet the following requirements:
– Windows updates may only be download when mobile devices are connect to Wi-Fi.
– Access to email and the Internet must be possible at all times.
What should you do?
A. Open the Setting app and select Update & Security. Then select and configure Change active hours.
B. Open the Setting app and select Network & Internet. Then select Change connection properties, and set the Metered connection option for cellular network connections to On.
C. Open the Setting app and select Network & Internet. Then select Data Usage and set a data limit.
D. Open the Setting app and select Update & Security. Then select and configure Delivery Optimization.
Answer: B
Explanation:
https://www.makeuseof.com/tag/5-ways-temporarily-turn-off-windows-update-windows-10/
NEW QUESTION 310
Your company has a branch office that contains 25 workgroup computers. The computers run Windows 10 Pro. Users report that they cannot see other computers from Network in File Explorer. What should you do to resolve the issue?
A. Set Network profile to Private.
B. Turn off random hardware addresses for the network connection.
C. Set Network profile to Public.
D. Configure the network connection as a metered connection.
Answer: A
NEW QUESTION 311
You have a computer that runs Windows 10. You need to view the Windows Update diagnostic log. What should you do first?
A. From File Explorer, go to the C:\Windows\Logs\WindowsUpdate folder and select Show hidden files, folders, and drives.
B. From Windows Update in the Settings app, configure Advanced options.
C. From Event Viewer, modify the properties of the WindowsUpdateClient operational log.
D. From Windows PowerShell, run the Get-WindowsUpdateLog cmdlet.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/powershell/module/windowsupdate/get-windowsupdatelog?view=windowsserver2022-ps
NEW QUESTION 312
HotSpot
You have a computer that runs Windows 10. A feature update is installed automatically. You need to roll back the feature update. Up to how many days after the feature update is installed can you roll back the installation, and what should you use to perform the roll back? (To answer, select the appropriate options in the answer area.)
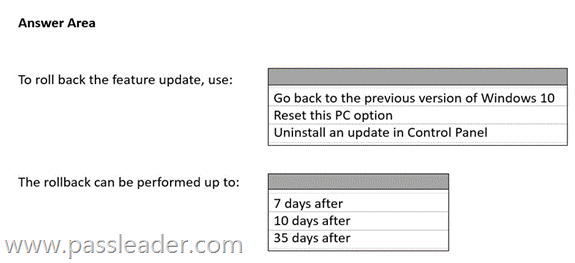
Explanation:
https://www.howtogeek.com/235474/how-to-roll-back-builds-and-uninstall-updates-on-windows-10/
NEW QUESTION 313
Drag and Drop
You have a computer that runs Windows 10 and has the Windows Assessment and Deployment Kit (Windows ADK) installed. You need to perform the following tasks:
– Prepare a Windows PE (WinPE) working directory.
– Add scripting support to a WinPE image.
– Mount and unmount a WinPE image.
Which command should you use for each task? (To answer, drag the appropriate commands to the correct tasks. Each command may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

Explanation:
https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/winpe-mount-and-customize?view=windows-11
https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/winpe-adding-powershell-support-to-windows-pe?view=windows-11
NEW QUESTION 314
……
Get the newest PassLeader MD-100 VCE dumps here: https://www.passleader.com/md-100.html (315 Q&As Dumps –> 428 Q&As Dumps)
And, DOWNLOAD the newest PassLeader MD-100 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=1nN5vMaeSbKiqjJwy-Y8KG-xvZL876tCK