Valid SC-100 Dumps shared by PassLeader for Helping Passing SC-100 Exam! PassLeader now offer the newest SC-100 VCE dumps and SC-100 PDF dumps, the PassLeader SC-100 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader SC-100 dumps with VCE and PDF here: https://www.passleader.com/sc-100.html (169 Q&As Dumps –> 197 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader SC-100 dumps from Cloud Storage: https://drive.google.com/drive/folders/1ByJyHdB_NYyHMI7Z_J24E5fgwr4Egv2X
NEW QUESTION 1
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint.
Does this meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 2
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance.
Does this meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 3
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
A. Yes
B. No
Answer: A
NEW QUESTION 4
You are designing the encryption standards for data at rest for an Azure resource. You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly.
Solution: For blob containers in Azure Storage, you recommend encryption that uses customer-managed keys (CMKs).
Does this meet the goal?
A. Yes
B. No
Answer: A
NEW QUESTION 5
Your company has on-premises Microsoft SQL Server databases. The company plans to move the databases to Azure. You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs. What should you include in the recommendation?
A. Azure SQL Managed Instance
B. Azure Synapse Analytics Dedicated SQL Pools
C. Azure SQL Database
D. SQL Server on Azure Virtual Machines
Answer: C
Explanation:
https://docs.microsoft.com/en-us/azure/azure-sql/database/dynamic-data-masking-overview?view=azuresql
NEW QUESTION 6
You need to design a solution to provide administrators with secure remote access to the virtual machines. The solution must meet the following requirements:
– Prevent the need to enable ports 3389 and 22 from the internet.
– Only provide permission to connect the virtual machines when required.
– Ensure that administrators use the Azure portal to connect to the virtual machines.
Which two actions should you include in the solution? (Each correct answer presents part of the solution. Choose two.)
A. Enable Azure Active Directory (Azure AD) Privileged Identity Management (PIM) roles as virtual machine contributors.
B. Configure Azure VPN Gateway.
C. Enable Just Enough Administration (JEA).
D. Enable just-in-time (JIT) VM access.
E. Configure Azure Bastion.
Answer: DE
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/just-in-time-access-usage?tabs=jit-config-asc%2Cjit-request-asc
https://docs.microsoft.com/en-us/azure/bastion/tutorial-create-host-portal
NEW QUESTION 7
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatical. What should you use?
A. The regulatory compliance dashboard in Defender for Cloud.
B. Azure Policy.
C. Azure Blueprints.
D. Azure role-based access control (Azure RBAC).
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/governance/policy/how-to/remediate-resources
NEW QUESTION 8
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud:
– Access to storage accounts with firewall and virtual network configurations should be restricted.
– Storage accounts should restrict network access using virtual network rules.
– Storage account should use a private link connection.
– Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
A. Azure Storage Analytics
B. Azure Network Watcher
C. Microsoft Sentinel
D. Azure Policy
Answer: D
NEW QUESTION 9
You are designing the security standards for containerized applications onboarded to Azure. You are evaluating the use of Microsoft Defender for Containers. In which two environments can you use Defender for Containers to scan for known vulnerabilities? (Each correct answer presents a complete solution. Choose two.)
A. Linux containers deployed to Azure Container Registry.
B. Linux containers deployed to Azure Kubernetes Service (AKS).
C. Windows containers deployed to Azure Container Registry.
D. Windows containers deployed to Azure Kubernetes Service (AKS).
E. Linux containers deployed to Azure Container Instances.
Answer: DE
NEW QUESTION 10
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation. You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc. Which three services can you use to provide security for the AWS resources? (Each correct answer presents a complete solution. Choose three.)
A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
B. Azure Active Directory (Azure AD) Conditional Access.
C. Microsoft Defender for servers.
D. Azure Policy.
E. Microsoft Defender for Containers.
Answer: ABE
NEW QUESTION 11
You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL). You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment. What should you include during the application design phase?
A. Static application security testing (SAST) by using SonarQube.
B. Dynamic application security testing (DAST) by using Veracode.
C. Threat modeling by using the Microsoft Threat Modeling Tool.
D. Software decomposition by using Microsoft Visual Studio Enterprise.
Answer: C
Explanation:
The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development. Also, we designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models.
https://docs.microsoft.com/en-us/azure/security/develop/threat-modeling-tool
NEW QUESTION 12
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States. You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface. What should you include in the recommendation?
A. Azure Firewall Premium
B. Azure Application Gateway Web Application Firewall (WAF)
C. Network Security Groups (NSGs)
D. Azure Traffic Manager and Application Security Groups
Answer: B
Explanation:
Roughly 20% of all Internet traffic comes from bad bots. They do things like scraping, scanning, and looking for vulnerabilities in your web application. When these bots are stopped at the Web Application Firewall (WAF), they can’t attack you. They also can’t use up your resources and services, such as your backends and other underlying infrastructure. You can enable a managed bot protection rule set for your WAF to block or log requests from known malicious IP addresses. The IP addresses are sourced from the Microsoft Threat Intelligence feed. Intelligent Security Graph powers Microsoft threat intelligence and is used by multiple services including Microsoft Defender for Cloud.
https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/bot-protection-overview
NEW QUESTION 13
You have a Microsoft 365 E5 subscription. You need to recommend a solution to add a watermark to email attachments that contain sensitive data. What should you include in the recommendation?
A. Microsoft Defender for Cloud Apps
B. Insider Risk Management
C. Microsoft Information Protection
D. Azure Purview
Answer: C
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
NEW QUESTION 14
Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity. You are informed about incidents that relate to compromised identities. You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered. Which Defender for Identity feature should you include in the recommendation?
A. standalone sensors
B. honeytoken entity tags
C. sensitivity labels
D. custom user tags
Answer: B
Explanation:
Honeytoken entities are used as traps for malicious actors. Any authentication associated with these honeytoken entities triggers an alert.
https://docs.microsoft.com/en-us/defender-for-identity/entity-tags
NEW QUESTION 15
You have a Microsoft 365 E5 subscription and an Azure subscription. You are designing a Microsoft Sentinel deployment. You need to recommend a solution for the security operations team. The solution must include custom views and a dashboard for analyzing security events. What should you recommend using in Microsoft Sentinel?
A. playbooks
B. workbooks
C. notebooks
D. threat intelligence
Answer: B
Explanation:
Microsoft Sentinel allows you to create custom workbooks across your data, and also comes with built-in workbook templates to allow you to quickly gain insights across your data as soon as you connect a data source.
NEW QUESTION 16
Your company has an office in Seattle. The company has two Azure virtual machine scale sets hosted on different virtual networks. The company plans to contract developers in India. You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements:
– Prevent exposing the public IP addresses of the virtual machines.
– Provide the ability to connect without using a VPN.
– Minimize costs.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Deploy Azure Bastion to one virtual network.
B. Deploy Azure Bastion to each virtual network.
C. Enable just-in-time VM access on the virtual machines.
D. Create a hub and spoke network by using virtual network peering.
E. Create NAT rules and network rules in Azure Firewall.
Answer: AC
Explanation:
https://docs.microsoft.com/en-us/azure/bastion/tutorial-create-host-portal
https://docs.microsoft.com/en-us/azure/defender-for-cloud/just-in-time-access-usage
NEW QUESTION 17
Your company is moving a big data solution to Azure. The company plans to use the following storage workloads:
– Azure Storage blob containers.
– Azure Data Lake Storage Gen2.
– Azure Storage file shares.
– Azure Disk Storage.
Which two storage workloads support authentication by using Azure Active Directory (Azure AD)? (Each correct answer presents a complete solution. Choose two.)
A. Azure Disk Storage.
B. Azure Storage blob containers.
C. Azure Storage file shares.
D. Azure Data Lake Storage Gen2.
Answer: BC
Explanation:
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blobs-introduction
https://docs.microsoft.com/en-us/azure/storage/files/storage-files-introduction
NEW QUESTION 18
Your company has a Microsoft 365 E5 subscription. The Chief Compliance Officer plans to enhance privacy management in the working environment. You need to recommend a solution to enhance the privacy management. The solution must meet the following requirements:
– Identify unused personal data and empower users to make smart data handling decisions.
– Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
– Provide users with recommendations to mitigate privacy risks.
What should you include in the recommendation?
A. Microsoft Viva Insights.
B. Advanced eDiscovery.
C. Privacy Risk Management in Microsoft Priva.
D. Communication compliance in insider risk management.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/privacy/priva/priva-overview
NEW QUESTION 19
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. Azure Active Directory (Azure AD) Conditional Access App Control policies.
B. OAuth app policies in Microsoft Defender for Cloud Apps.
C. App protection policies in Microsoft Endpoint Manager.
D. Application control policies in Microsoft Defender for Endpoint.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/mem/configmgr/protect/deploy-use/use-device-guard-with-configuration-manager
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/select-types-of-rules-to-create
NEW QUESTION 20
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Defender for Cloud, review the Azure security baseline for audit report.
B. From Defender for Cloud, add a regulatory compliance standard.
C. From Defender for Cloud, enable Defender for Cloud plans.
D. From Defender for Cloud, review the secure score recommendations.
Answer: B
Explanation:
https://docs.microsoft.com/en-gb/azure/defender-for-cloud/update-regulatory-compliance-packages#add-a-regulatory-standard-to-your-dashboard
NEW QUESTION 21
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard. You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
A. Azure Monitor webhooks
B. Azure Logics Apps
C. Azure Event Hubs
D. Azure Functions apps
Answer: B
Explanation:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/workflow-automation
NEW QUESTION 22
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements. Which two services should you leverage in the strategy? (Each correct answer presents part of the solution. Choose two.)
A. Azure AD Conditional Access
B. Microsoft Defender for Cloud Apps
C. Microsoft Defender for Cloud
D. Microsoft Defender for Endpoint
E. Access Reviews in Azure AD
Answer: AB
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
NEW QUESTION 23
Your company has devices that run either Windows 10, Windows 11, or Windows Server. You are in the process of improving the security posture of the devices. You plan to use security baselines from the Microsoft Security Compliance Toolkit. What should you recommend using to compare the baselines to the current device configurations?
A. Microsoft Intune
B. Policy Analyzer
C. Local Group Policy Object (LGPO)
D. Windows Autopilot
Answer: B
Explanation:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-framework/security-compliance-toolkit-10
NEW QUESTION 24
You are designing the security standards for a new Azure environment. You need to design a privileged identity strategy based on the Zero Trust model. Which framework should you follow to create the design?
A. Enhanced Security Admin Environment (ESAE)
B. Microsoft Security Development Lifecycle (SDL)
C. Rapid Modernization Plan (RaMP)
D. Microsoft Operational Security Assurance (OSA)
Answer: C
Explanation:
https://docs.microsoft.com/en-us/security/zero-trust/zero-trust-ramp-overview
NEW QUESTION 25
You have a Microsoft 365 E5 subscription. You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents. You need to recommend a solution to prevent Personally Identifiable Information (Pll) from being shared. Which two components should you include in the recommendation? (Each correct answer presents part of the solution. Choose two.)
A. data loss prevention (DLP) policies
B. sensitivity label policies
C. retention label policies
D. eDiscovery cases
Answer: AB
Explanation:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
NEW QUESTION 26
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription. All the on-premises servers in the perimeter network are prevented from connecting directly to the internet. The customer recently recovered from a ransomware attack. The customer plans to deploy Microsoft Sentinel. You need to recommend configurations to meet the following requirements:
– Ensure that the security operations team can access the security logs and the operation logs.
– Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? (Each correct answer presents a complete solution. Choose two.)
A. Azure Active Directory (Azure AD) Conditional Access policies.
B. A custom collector that uses the Log Analytics agent.
C. Resource-based role-based access control (RBAC).
D. The Azure Monitor agent.
Answer: CD
……
NEW QUESTION 97
HotSpot
You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications:
– Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests.
– Users will authenticate by using Azure Active Directory (Azure AD) user accounts.
You need to recommend an access security architecture for App1. What should you include in the recommendation? (To answer, select the appropriate options in the answer area.)

Answer:

Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/governance/identity-governance-overview
NEW QUESTION 98
HotSpot
You are designing an auditing solution for Azure landing zones that will contain the following components:
– SQL audit logs for Azure SQL databases.
– Windows Security logs from Azure virtual machines.
– Azure App Service audit logs from App Service web apps.
You need to recommend a centralized logging solution for the landing zones. The solution must meet the following requirements:
– Log all privileged access.
– Retain logs for at least 365 days.
– Minimize costs.
What should you include in the recommendation? (To answer, select the appropriate options in the answer area.)

NEW QUESTION 99
Drag and Drop
You have a Microsoft 365 subscription. You need to recommend a security solution to monitor the following activities:
– User accounts that were potentially compromised.
– Users performing bulk file downloads from Microsoft SharePoint Online.
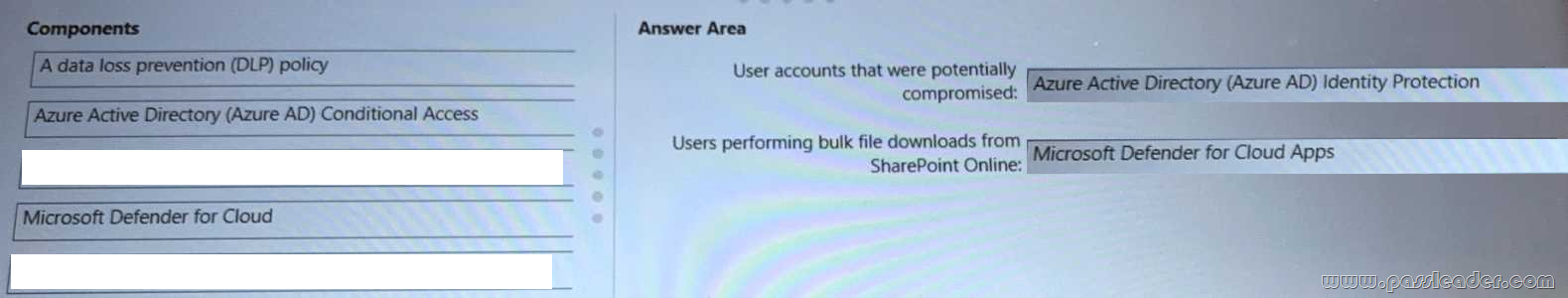
What should you include in the recommendation for each activity? (To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

NEW QUESTION 100
Drag and Drop
Your company has Microsoft 365 E5 licenses and Azure subscriptions. The company plans to automatically label sensitive data stored in the following locations:
– Microsoft SharePoint Online
– Microsoft Exchange Online
– Microsoft Teams
You need to recommend a strategy to identify and protect sensitive data. Which scope should you recommend for the sensitivity label policies? (To answer, drag the appropriate scopes to the correct locations. Each scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)

NEW QUESTION 101
Case Study 1 – Fabrikam, Inc.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
A. Azure Key Vault
B. GitHub Advanced Security
C. Application Insights in Azure Monitor
D. Azure DevTest Labs
Answer: B
NEW QUESTION 102
Case Study 1 – Fabrikam, Inc.
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements. What should you include in the recommendation?
A. Transparent Data Encryption (TDE)
B. Always Encrypted
C. Row-Level Security (RLS)
D. Dynamic Data Masking
E. Data Classification
Answer: D
Explanation:
https://docs.microsoft.com/en-us/sql/relational-databases/security/dynamic-data-masking?view=sql-server-ver16
……
NEW QUESTION 106
Case Study 2 – Litware, Inc.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements. What should you configure for each landing zone?
A. Azure DDoS Protection Standard.
B. An Azure Private DNS zone.
C. Microsoft Defender for Cloud.
D. An ExpressRoute gateway.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/ddos-protection/ddos-protection-overview
NEW QUESTION 107
Case Study 2 – Litware, Inc.
To meet the application security requirements, which two authentication methods must the applications support? (Each correct answer presents a complete solution. Choose two.)
A. Security Assertion Markup Language (SAML)
B. NTLMv2
C. Certificate-Based Authentication
D. Kerberos
Answer: AC
NEW QUESTION 108
……
Get the newest PassLeader SC-100 VCE dumps here: https://www.passleader.com/sc-100.html (169 Q&As Dumps –> 197 Q&As Dumps)
And, DOWNLOAD the newest PassLeader SC-100 PDF dumps from Cloud Storage for free: https://drive.google.com/drive/folders/1ByJyHdB_NYyHMI7Z_J24E5fgwr4Egv2X