Valid MS-500 Dumps shared by PassLeader for Helping Passing MS-500 Exam! PassLeader now offer the newest MS-500 VCE dumps and MS-500 PDF dumps, the PassLeader MS-500 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader MS-500 dumps with VCE and PDF here: https://www.passleader.com/ms-500.html (245 Q&As Dumps –> 264 Q&As Dumps –> 330 Q&As Dumps –> 412 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader MS-500 dumps from Cloud Storage: https://drive.google.com/open?id=1AMq2tUY1mE3Y-RycYB-rPdtfEC69Sfil
NEW QUESTION 229
You have a Microsoft 365 E5 subscription that contains a user named User1. The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1. For User1, you select Confirm user compromised. User1 can still sign in. You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the user risk policy to block access when the user risk level is medium and higher.
Does this meet the goal?
A. Yes
B. No
Answer: B
NEW QUESTION 230
You have a Microsoft 365 E5 subscription that contains a user named User1. The Azure Active Directory (Azure AD) Identity Protection risky users report identities User1. For User1, you select Confirm user compromised. User1 can still sign in. You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level.
Solution: You configure the user risk policy to block access when the user risk level is high.
Does this meet the goal?
A. Yes
B. No
Answer: A
NEW QUESTION 231
You have a Microsoft 365 E5 subscription. You plan to create a conditional access policy named Policy1. You need to be able to use the sign-in risk level condition in Policy1. What should you do first?
A. Connect Microsoft Endpoint Manager and Microsoft Defender for Endpoint.
B. From the Azure Active Directory admin center, configure the Diagnostics settings.
C. From the Endpoint Management admin center, create a device compliance policy.
D. Onboard Azure Active Directory (Azure AD) Identity Protection.
Answer: D
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-risk
NEW QUESTION 232
You have a Microsoft 165 E5 subscription. You need to enable support for sensitivity labels in Microsoft SharePoint Online. What should you use?
A. the SharePoint admin center
B. the Microsoft J65 admin center
C. the Microsoft 365 compliance center
D. the Azure Active Directory admin
Answer: D
NEW QUESTION 233
You have a Microsoft 365 subscription named contofco.com. You need to configure Microsoft OneDrive for Business external sharing to meet the following requirements:
– Enable flic sharing for users that rave a Microsoft account.
– Block file sharing for anonymous users.
What should you do?
A. From Advanced settings tor external sharing, select Allow or Nock sharing with people on specific domains and add contoso.com.
B. From the External sharing settings for OneDrive, select Existing external users.
C. From the External sharing settings for OneDrive, select New and existing external users.
D. From the External sharing settings for OneDrive, select Only people in your organization.
Answer: B
NEW QUESTION 234
You have Microsoft 365subscription. You need to be notified by email whenever an administrator starts an ediscovery search. What should you do from the Security & Compliance admin center?
A. Prom Alerts, create an alert policy.
B. From Search & investigation, create a guided search.
C. From ediscovery orate an eDiscovery case.
D. From Reports, create a managed schedule.
Answer: A
NEW QUESTION 235
You have a Microsoft 365 subscription linked to an Azure Active Directory (Azure AD) tenant that contains a user named User1. You need to grant User1 permission to search Microsoft 365 audit logs. The solution must use the principle of least privilege. Which rote should you assign to User1?
A. the View-Only Audit Logs role m the Security & Compliance admin
B. the Security reader role in the Azure Active Directory admin center
C. the View-Only Audit Logs role in the Exchange admin center
D. the Compliance Management role in the Exchange admin center
Answer: B
NEW QUESTION 236
You have a Microsoft 365 tenant that uses Azure Information Protection to encrypt sensitive content. You plan to implement Microsoft Cloud App Security to inspect protected files that are uploaded to Microsoft OneDrive for Business. You need to ensure that at Azure Information Protection-protected files can be scanned by using Cloud App Security. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. From the Cloud App Security admin center, enable file monitoring of software as a service (SaaS) apps.
B. From the Cloud App Security admin center, create an OAuth app policy for apps that have the Have full access to user files permission.
C. From the Microsoft 365 compliance admin center create a data loss prevention (EXP) policy that contains an exception for content that contains a sensitive information type.
D. From the Azure Active Directory admin center, grant Cloud App Security permission to read all the protected content of the tenant.
Answer: BD
NEW QUESTION 237
You have an Azure Active Directory (Azure AD) tenant that has a Microsoft 365 subscription. You recently configured the tenant to require multi factor authentication (MFA) for risky sign ins. You need to review the users who required MFA. What should you do?
A. From the Microsoft 365 admin center, review a Security & Compliance report.
B. From the Azure Active Directory admin center, download the sign-ms to a CSV file.
C. From the Microsoft 365 Compliance admin center, run an audit log search and download the results to a CSV file.
D. From the Azure Active Directory admin center, review the Authentication methods activities.
Answer: D
NEW QUESTION 238
You have a hybrid Azure Active Directory (Azure AD) tenant that has pass-through authentication enabled. You plan to implement Azure AD identity Protection and enable the user risk policy. You need to configure the environment to support the user risk policy. What should you do?
A. Enable password hash synchronization.
B. Configure a conditional access policy.
C. Enforce the multi-factor authentication (MFA) registration policy.
D. Enable the sign-in risk policy.
Answer: C
NEW QUESTION 239
You have a Microsoft 365 E5 subscription. You need to ensure that users who are assigned the Exchange administrator role have time-limited permissions and must use multi factor authentication (MFA) to request the permissions. What should you use to achieve the goal?
A. Microsoft 365 user management.
B. Microsoft Azure AD group management.
C. Security & Compliance permissions.
D. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management.
Answer: D
NEW QUESTION 240
You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager. You need to enable Microsoft Defender Exploit Guard (Microsoft Defender EG) on the devices. Which type of device configuration profile should you use?
A. Endpoint protection.
B. Device restrictions.
C. Microsoft Defender for Endpoint.
D. Identity protection.
Answer: A
NEW QUESTION 241
You have a Microsoft 365 E5 subscription. You need to use Microsoft Cloud App Security to identify documents stored in Microsoft SharePomt Online that contain proprietary information. What should you create in Cloud App Security?
A. a data source and a file policy
B. a data source and an app discovery policy
C. an app connector and an app discovery policy
D. an app connector and a we policy
Answer: B
NEW QUESTION 242
HotSpot
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table:
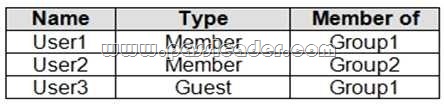
You assign an enterprise application named App1 to Group1 and User2. You configure an Azure AD access review of App1. The review has the following settings:
– Review name: Review1
– Start date: 01152020
– Frequency: One time
– End date: 02142020
– Users to review: Assigned to an application
– Scope: Everyone
– Applications: App1
– Reviewers: Members (self)
– Auto apply results to resource: Enable
– Should reviewer not respond: Take recommendations
On February 15, 2020, you review the access review report and see the entries shown in the following table:

For each of the following statements, select Yes if the statement is true. Otherwise, select No.

NEW QUESTION 243
HotSpot
You have an Azure Sentinel workspace. You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate. You need to configure the workspace to meet the following requirements:
– Call the Azure logic app when an alert is triggered for a risky sign-in.
– To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? (To answer, select the appropriate options in the answer area.)
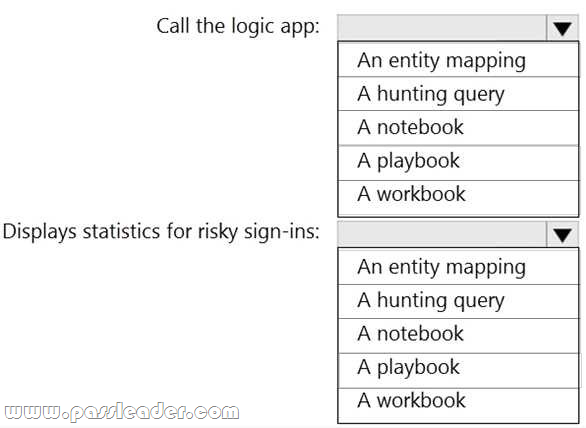
Answer:

Explanation:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
NEW QUESTION 244
……
Get the newest PassLeader MS-500 VCE dumps here: https://www.passleader.com/ms-500.html (245 Q&As Dumps –> 264 Q&As Dumps –> 330 Q&As Dumps –> 412 Q&As Dumps)
And, DOWNLOAD the newest PassLeader MS-500 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=1AMq2tUY1mE3Y-RycYB-rPdtfEC69Sfil
