Valid 98-366 Dumps shared by PassLeader for Helping Passing 98-366 Exam! PassLeader now offer the newest 98-366 VCE dumps and 98-366 PDF dumps, the PassLeader 98-366 exam questions have been updated and ANSWERS have been corrected, get the newest PassLeader 98-366 dumps with VCE and PDF here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
BTW, DOWNLOAD part of PassLeader 98-366 dumps from Cloud Storage: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc
QUESTION 81
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
To set lower security settings in Internet Explorer for an extranet site, add the site’s URL to the Local Intranet zone.
A. Internet
B. Trusted Sites
C. Extranet Sites
D. No change is needed
Answer: B
Explanation:
The level of security set for Trusted sites is applied to sites that you have specifically indicated to be ones that you trust not to damage your computer or information.
QUESTION 82
You are helping a friend set up a public-facing web server for a home office. Your friend wants to protect the internal network from intrusion. What should you do?
A. Set the web server in a perimeter network.
B. Set the web server to block access on ports 80 and 443.
C. Configure the firewall to block access on ports 80 and 443.
D. Set the IP address of the web server to be within the LAN.
Answer: A
Explanation:
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization’s external-facing services to a larger and untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s local area network (LAN); an external network node only has direct access to equipment in the DMZ, rather than any other part of the network.
QUESTION 83
Hotspot
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Answer:

Explanation:
– Network bridging is the action taken by network equipment to create an aggregate network from either two or more communication networks, or two or more network segments. If one or more segments of the bridged network are wireless, it is known as wireless bridging.
– In Wi-Fi, repeater mode is a variation on bridging. Rather than join multiple LANs, repeater mode is intended mainly to increase the range of a single wireless LAN by extending the same wireless signal.
– In Wi-Fi networking, bridging mode allows two or more wireless access points (APs) to communicate with each for the purpose of joining multiple LANs.
QUESTION 84
What are two characteristics of the CSMA/CD access method? (Choose two.)
A. It checks to see if a collision has been detected.
B. It does a round robin search for requests to transmit from all nodes on the network.
C. It signals its intent to transmit on the network.
D. It waits until the transmission medium is idle.
Answer: AD
Explanation:
Main procedure for the CSMA/CD:
1. Is my frame ready for transmission? If yes, it goes on to the next point.
2. Is medium idle? If not, wait until it becomes ready.
3. Start transmitting.
4. Did a collision occur? If so, go to collision detected procedure.
5. Reset retransmission counters and end frame transmission.
Note:
Carrier Sense Multiple Access With Collision Detection (CSMA/CD) is a media access control method used most notably in local area networking using early Ethernet technology. It uses a carrier sensing scheme in which a transmitting data station detects other signals while transmitting a frame, and stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to resend the frame.
QUESTION 85
What are two characteristics of a mesh network topology? (Choose two.)
A. It is fault tolerant because of redundant connections.
B. Every node connects to every other node on the network.
C. It works best for networks with a large number of nodes.
D. It requires less cabling than either a star or ring topology.
Answer: AB
Explanation:
In a (full) mesh network topology, each of the network node, computer and other devices, are interconnected with one another. Every node not only sends its own signals but also relays data from other nodes. In fact a true mesh topology is the one where every node is connected to every other node in the network. This type of topology is very expensive as there are many redundant connections, thus it is not mostly used in computer networks. It is commonly used in wireless networks.
QUESTION 86
Which protocol is responsible for automatically assigning IP addresses?
A. HTTP
B. DHCP
C. DNS
D. WINS
Answer: B
Explanation:
Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables a server to automatically assign an IP address to a computer from a defined range of numbers (i.e., a scope) configured for a given network.
QUESTION 87
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
According to the OSI model, encryption takes place on the transport layer.
A. Presentation
B. Network
C. Application
D. No change is needed
Answer: A
Explanation:
SSL or TLS encryption takes place at the presentation layer, Layer 6 of the OSI model.
QUESTION 88
Hotspot
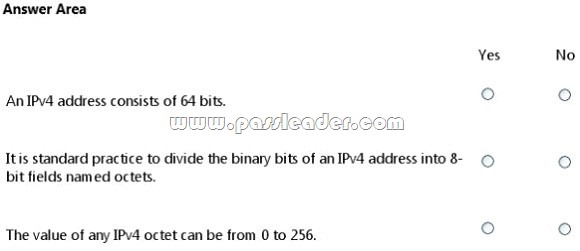
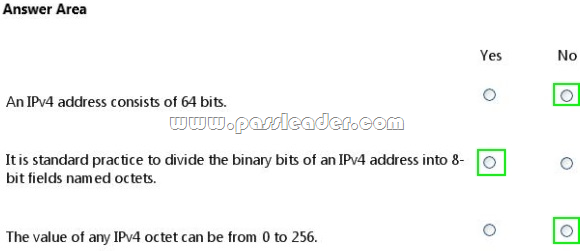
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.
Answer:
Explanation:
– IPv4 uses a 32-bit address scheme.
– IPv4 addresses may be written in any notation expressing a 32-bit integer value, but for human convenience, they are most often written in the dot-decimal notation, which consists of four octets of the address expressed individually in decimal and separated by periods.
– Each octet has a value between 0 and 255.
QUESTION 89
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
IPSec policies for two machines on a LAN can be modified by using the IPSec policy snap-in on Windows 7.
A. Windows Firewall with Advanced Security snap-in
B. LAN adapter properties
C. Remote Access snap-in
D. No change is needed
Answer: A
Explanation:
Windows Firewall with Advanced Security is an advanced interface for IT professionals to use to configure both Windows Firewall and Internet Protocol security (IPsec) settings for the computers on their networks. (Applies To: Windows 7, Windows Server 2008, Windows Server 2008 R2, Windows Vista)
QUESTION 90
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select ‘No change is needed” if the underlined text makes the statement correct.
An Address Resolution Protocol (ARP) table is used to associate IP addresses with host names.
A. MAC addresses
B. HomeGroup membership
C. Preferred routers
D. No change is needed
Answer: A
Explanation:
Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address (MAC address) that is recognized in the local network.
QUESTION 91
Which network device interconnects computers in a workgroup, is able to be remotely configured, and provides the best throughput?
A. Unmanaged switch
B. Hub
C. Router
D. Managed switch
Answer: D
Explanation:
Managed switches: these switches have one or more methods to modify the operation of the switch. Common management methods include: a command-line interface (CLI) accessed via serial console, telnet or Secure Shell, an embedded Simple Network Management Protocol (SNMP) agent allowing management from a remote console or management station, or a web interface for management from a web browser.
Incorrect:
Not A: Unmanaged switches are basic plug-and-play switches with no remote configuration, management, or monitoring options, although many can be locally monitored and configured via LED indicators and DIP switches.
Not B: Hubs cannot be managed.
Not C: Switches are faster than routers.
QUESTION 92
What is the maximum cable length for a single Cat5 UTP cable run?
A. 285 feet/86.87 meters
B. 328 feet/99.97 meters
C. 432 feet/131.67 meters
D. 600 feet/182.88 meters
Answer: B
Explanation:
Cat5/5e/6 Ethernet Copper Cabling has a Maximum Segment Length of 100 meters.
QUESTION 93
Hotspot
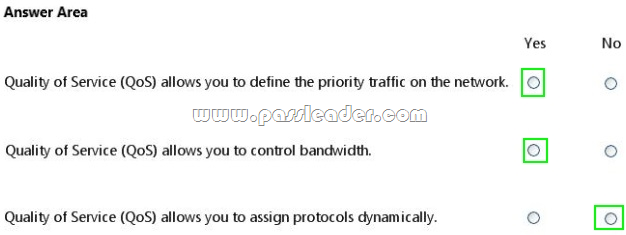
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is worth one point.

Answer:
Explanation:
– QoS traffic control: Regulate data flows by classifying, scheduling, and marking packets based on priority and by shaping traffic (smoothing bursts of traffic by limiting the rate of flow). Traffic control mechanisms segregate traffic into service classes and control delivery to the network. The service class assigned to a traffic flow determines the QoS treatment the traffic receives.
– The goal of QoS is to provide preferential delivery service for the applications that need it by ensuring sufficient bandwidth, controlling latency and jitter, and reducing data loss.
QUESTION 94
Which of these cable types transmits data the greatest distance?
A. Multi-mode fiber
B. Single-mode fiber
C. Cat5e
D. Cat6
Answer: B
Explanation:
When working with distances up to 2 km, use multimode optical-fiber cable. Like multi-mode optical fibers, single mode fibers do exhibit modal dispersion resulting from multiple spatial modes but with narrower modal dispersion. Single mode fibers are therefore better at retaining the fidelity of each light pulse over longer distances than multi-mode fibers. Cat5e and Cat6 max cable length is 100 metres.
QUESTION 95
What is a similarity between Layer 2 and Layer 3 switches?
A. Both provide a high level of security to the network.
B. Both use logical addressing to forward transmissions.
C. Both forward packets onto the network.
D. Both allow the implementation of VLANs.
Answer: D
Explanation:
A single layer-2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them via one or more routers; such a domain is referred to as a virtual local area network, virtual LAN or VLAN. LANs are layer 2 constructs, so they can be supported by both Layer 2 and Layer 3 switches.
Incorrect:
Not A: Layer 2 switches do not provide high level of security.
Not B: Another name for logical address is IP address. Only Layer 3 switches uses IP address. Layer 2 switches uses MAC addresses.
Not C: only Layer 3 switches forward packets on the network (like routers).
QUESTION 96
This question requires that you evaluate the underlined text to determine if it is correct. Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
“Dynamic routing” is fault tolerant.
A. Static routing
B. Default route
C. Least cost routing
D. No change is needed
Answer: D
Explanation:
Dynamic routing protocols can be fault tolerant.
QUESTION 97
You need to run four Ethernet network drops. Each drop is approximately 125 feet/46.33 meters. An interference exists along the path of each drop. You need to ensure that interference is reduced. Which cable type should you use?
A. STP Cat5e
B. UTP Cat5e
C. Cat3
D. UTP Cat6
Answer: A
Explanation:
Shielded cable, here STP Cat5e, would reduce interference.
QUESTION 98
What is an example of a Layer 3 device that connects multiple computers and networks?
A. Packet
B. Repeater
C. Switch
D. Router
Answer: D
Explanation:
A router is a layer 3 device, although some newer switches also perform layer 3 functions.
QUESTION 99
Which metric does Routing Information Protocol (RJP) use to determine the least costly route?
A. Delay
B. Host ID
C. Hop count
D. Interface
Answer: C
Explanation:
RIP uses a single routing metric (hop count) to measure the distance between the source and a destination network.
QUESTION 100
What are two differences between switches and hubs? (Choose two.)
A. Switches are slower than hubs because of the extra addressing functions that switches perform.
B. Switches send data to all of the computers that are connected to them for efficiency.
C. Switches are capable of sending and receiving data at the same time.
D. Switches identify the intended destination of the data that they receive.
Answer: AD
Explanation:
Hubs repeat everything they receive and can be used to extend the network. Switches control the flow of network traffic based on the address information in each packet. A switch learns which devices are connected to its ports (by monitoring the packets it receives), and then forwards on packets to the appropriate port only. This allows simultaneous communication across the switch, improving bandwidth.
Get the newest PassLeader 98-366 VCE dumps here: https://www.passleader.com/98-366.html (220 Q&As Dumps –> 261 Q&As Dumps)
And, DOWNLOAD the newest PassLeader 98-366 PDF dumps from Cloud Storage for free: https://drive.google.com/open?id=0B-ob6L_QjGLpVVhXZTVKdDJpSnc